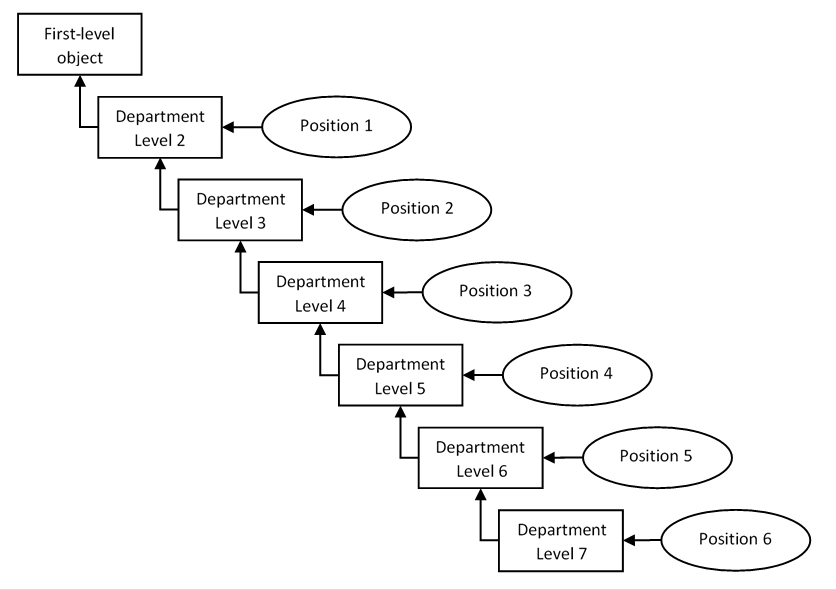
Proactive search for complex threats seems to be a useful technology but inaccessible for many organizations. Is it really so? What do companies need to do to start Threat Hunting? What tools are needed for threat hunting? What trends in this area can be seen on the market in the coming years? These are some of the questions I would like to answer in my article today.
What is Threat Hunting?
Threat Hunting is a search for threats in a proactive mode when the information security specialist is sure that the network is compromised. He should understand how his network operates in order to be able to identify various attacks by examining the existing anomalies.
Threat Hunting is a search for threats that have already bypassed automated detection systems. Moreover, most often, you do not have signals or alerts that allow you to detect an intrusion.
From the SOC perspective, Threat Hunting is an extension of the service that allows you to counter any level of intruders, including those who use previously unknown tools and methods.
Threat Hunting can be based on some data obtained by a security specialist, or it can be based on a hypothesis. If after testing the hypothesis, the test gives a positive result, then later, it can be used to improve the processes and mechanisms of detecting threats. And also, Threat Hunting allows you to find blind spots in the security system and expand the monitoring area.
What organizations need Threat Hunting?
Proactive threat hunting is relevant to those organizations that can become the target of a complex, targeted APT attack. At the same time, given the trend towards supply chain attacks, a small company may also become a target for motivated attackers.



 Since 2011 all Intel GPUs (integrated and discrete Intel Graphics products) include Intel Quick Sync Video (QSV) — the dedicated hardware core for video encoding and decoding. Intel QSV is supported by all popular video processing applications across multiple OSes including
Since 2011 all Intel GPUs (integrated and discrete Intel Graphics products) include Intel Quick Sync Video (QSV) — the dedicated hardware core for video encoding and decoding. Intel QSV is supported by all popular video processing applications across multiple OSes including