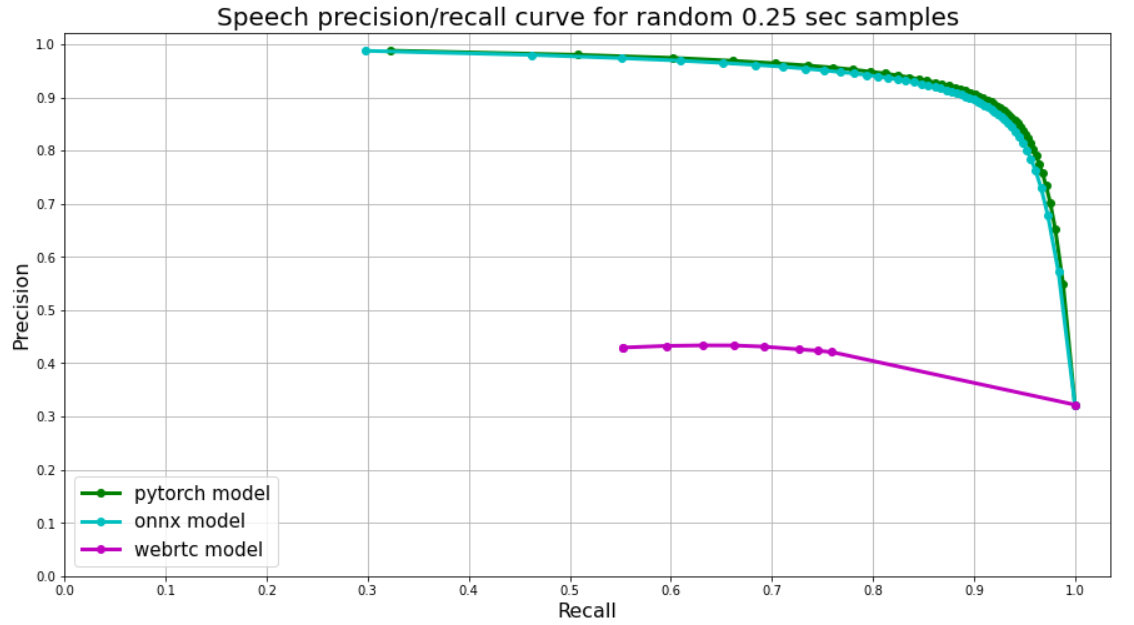
At the beginning of the year 2021, Qrator Labs is celebrating its 10 year anniversary. On January 19 our company marks the official passing of a formal 10 years longevity mark, entering its second decade of existence.
Everything started a little bit earlier - when at the age of 10 Alex saw the Robotron K 1820 - in 2008, when Alexander Lyamin - the founder and CEO of Qrator Labs, approached the Moscow State University superiors, where he worked as a NOC engineer at the time, with an idea of a DDoS-attack mitigation research project. The MSU's network was one of the largest in the country and, as we know now, it was the best place to hatch a future technology.
That time MSU administration agreed, and Mr Lyamin took his own hardware to the university, simultaneously gathering a team. In two years, by summer 2010, the project turned out to be that successful. It courted the DDoS attack of a bandwidth exceeding the MSU's upstream bandwidth capability. And on June 22 MSU superiors gave Mr Lyamin a choice - to shut down or find money to incorporate.
Alexander Lyamin chose to incorporate with his own means, which effectively meant that the needed infrastructure must be built from scratch. The initial design should be distributed instead of concentrated within one network, which resources were not enough for this specific task. And by September 1, 2010, those first server sites were ready and running.