Recently I've received the Announcing Windows 10 Insider Preview Build 18999 including an update for «Your Phone» app, and my first thing was — is there something useful for digital forensics?
So, I've immediately installed this app on my test workstation and connected it with my Android phone. On the same time I was checking for all system activities with Process Monitor to understand where all Your Phone app files are stored.

It seems that all files are located in:
Here is the content inside this folder:

And you can see a couple of .db files which are SQLite Databases
Well, I've downloaded a simple SQLite Browser and opened them one-by-one to check the internals. Some of DBs were empty, therefore I'll describe only ones with “Forensically sound” info.
1. Notifications.db
Notifications table:
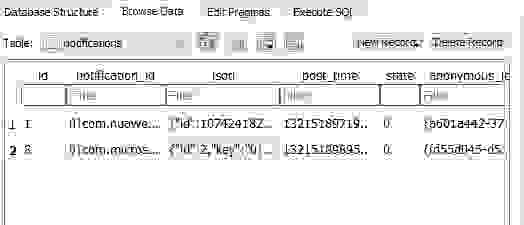
When something happens on your Android smartphone, the notification about the event appears and Your Phone app puts this event here, into this table. I've sent a email from the desktop to my smartphone, a popup notification about new letter has appeared and here you can see a lot of properties which were extracted from the notification:
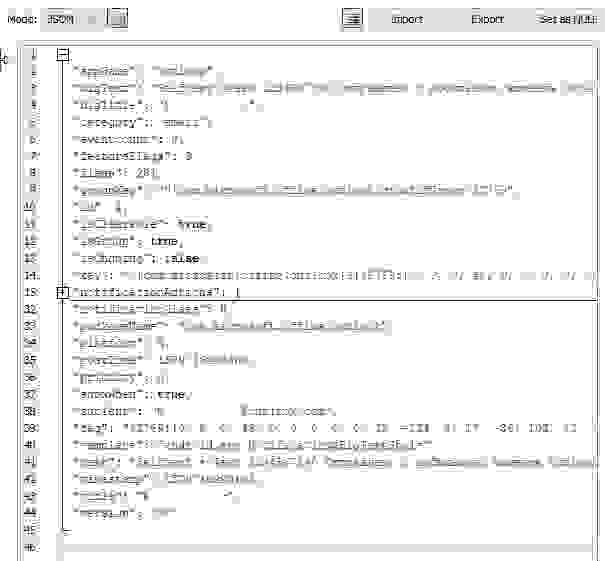
appname — my mobile email app
bigtext — subject and text
bigtitle — my name
posttime — timestamp when the message has been received by email server in Unix-time format
subtext — sender's email address
timestamp — timestamp when the message has been sent
Well, an investigator does not even need the message itself, he can get a lot of info, including the text, from the notification.
2. Phone.db
I found a lot of interesting tables inside!
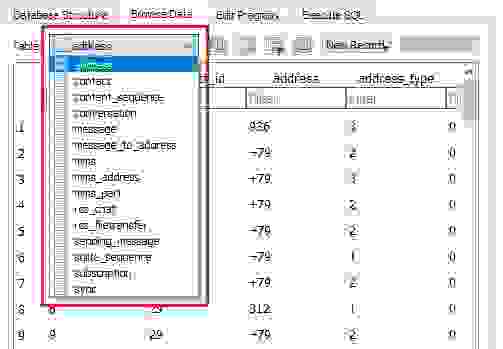
Address table:
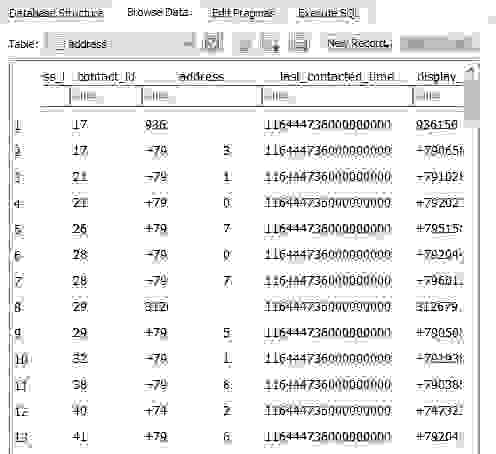
BOOM! All incoming numbers with timestamps! Cool!
Contact table:

BOOM again! The whole contact list even with photos :))
Message table:
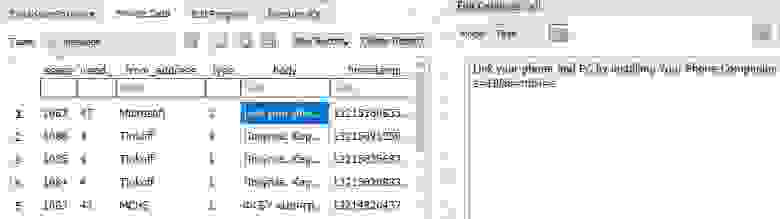
Text messages (SMS) with senders' names (I've cut senders with numbers, but you can trust me — they are there) and timestamps, and text (yes, from banks and kind of)
Subscription table:
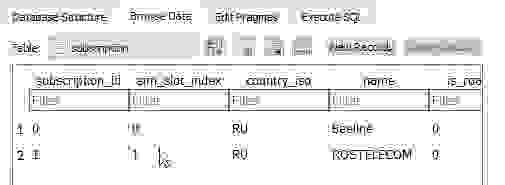
Here is the info about SIM cards
3. Photos.db
Photo table:

What a surprise! All pics stored on the mobile phone with timestamps :-)
4. Settings.db
Phone_apps table:

All installed apps list. Not so interesting, but who knows…
So, as a final — what do I think about it?
Of course it's really unsecured way to store so important info in unencrypted databases. As example, an intruder can get a remote access to your laptop or workstation (using Telegram RAT, haha :)) and download a lot of your important personal data.
On the other hand — this is a good place to get more digital evidences for a computer forensics investigator, for instance, in cases when inseder was involved in enterprise-targeted cyberattack. Getting a phone number of attack organizer is a good point for further investigation.
Be secured and thank you for attention!
So, I've immediately installed this app on my test workstation and connected it with my Android phone. On the same time I was checking for all system activities with Process Monitor to understand where all Your Phone app files are stored.

It seems that all files are located in:
%userprofile%\AppData\Local\Packages\Microsoft.YourPhone_???????\LocalCache\Indexed\????????????????\System\DatabaseWhere "????" is randomized ID
Here is the content inside this folder:

And you can see a couple of .db files which are SQLite Databases
Well, I've downloaded a simple SQLite Browser and opened them one-by-one to check the internals. Some of DBs were empty, therefore I'll describe only ones with “Forensically sound” info.
1. Notifications.db
Notifications table:

When something happens on your Android smartphone, the notification about the event appears and Your Phone app puts this event here, into this table. I've sent a email from the desktop to my smartphone, a popup notification about new letter has appeared and here you can see a lot of properties which were extracted from the notification:

appname — my mobile email app
bigtext — subject and text
bigtitle — my name
posttime — timestamp when the message has been received by email server in Unix-time format
subtext — sender's email address
timestamp — timestamp when the message has been sent
Well, an investigator does not even need the message itself, he can get a lot of info, including the text, from the notification.
2. Phone.db
I found a lot of interesting tables inside!

Address table:

BOOM! All incoming numbers with timestamps! Cool!
Contact table:

BOOM again! The whole contact list even with photos :))
Message table:

Text messages (SMS) with senders' names (I've cut senders with numbers, but you can trust me — they are there) and timestamps, and text (yes, from banks and kind of)
Subscription table:

Here is the info about SIM cards
3. Photos.db
Photo table:

What a surprise! All pics stored on the mobile phone with timestamps :-)
4. Settings.db
Phone_apps table:

All installed apps list. Not so interesting, but who knows…
So, as a final — what do I think about it?
Of course it's really unsecured way to store so important info in unencrypted databases. As example, an intruder can get a remote access to your laptop or workstation (using Telegram RAT, haha :)) and download a lot of your important personal data.
On the other hand — this is a good place to get more digital evidences for a computer forensics investigator, for instance, in cases when inseder was involved in enterprise-targeted cyberattack. Getting a phone number of attack organizer is a good point for further investigation.
Be secured and thank you for attention!