Web application firewall
Web application firewalls (WAFs) are a type of intrusion detection and prevention system and might be either a hardware or software solution. It is specifically designed to inspect HTTP(s) and analyse the GET and POST requests using the appalling detection logic explained below. Web application firewall software is generally available as a web server plugin.
WAF has become extremely popular and various companies offer a variety of solutions in different price categories, from small businesses to large corporations. Modern WAF is popular because it has a wide range of covered tasks, so web application developers can rely on it for various security issues, but with the assumption that this solution cannot guarantee absolute protection. A basic WAF workflow is shown below.
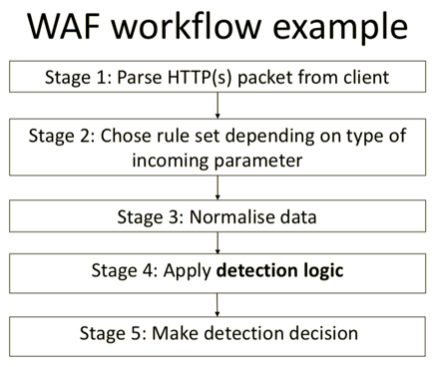
Its main function is the detection and blocking of queries in which, according to WAF analysis, there are some anomalies, or an attacking vector is traced. Such an analysis should not make it difficult for legitimate users to interact with a web application, but, at the same time, it must accurately and timely detect any attempted attack. In order to implement this functionality, WAF developers usually use regular expressions, tokens, behavioural analysis, reputation analysis and machine learning, and, often, all these technologies are used together.
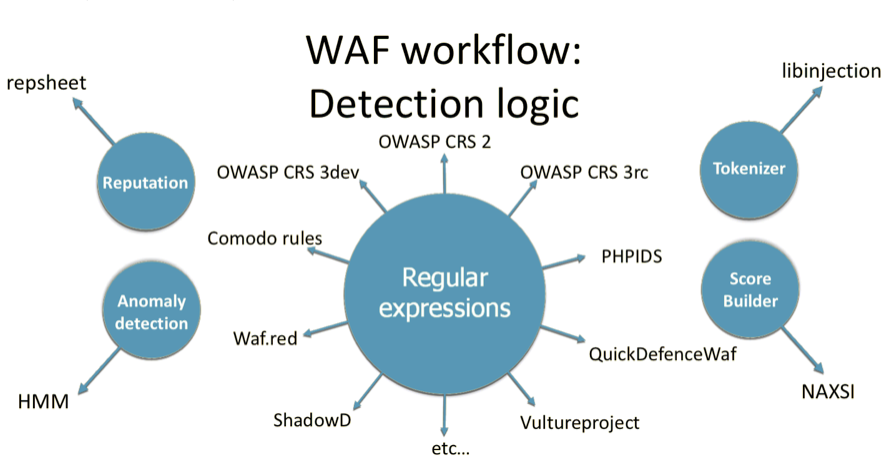
In addition, WAF can also provide other functionality: protection from DDoS, blocking of IP-addresses of attackers, tracking of suspicious IP-addresses, adding an HTTP-only flag to the cookie, or adding the functionality of CSRF-tokens. Each WAF is individual and has a unique internal arrangement, but there are some typical methods used for analysis.
Regular expression
Most of the existing WAFs are based on rules based on regular expressions. To create them, some well-known sets of attacks are studied by the WAF developer and, consequently, key syntactic constructions are determined, the presence of which can be claimed to carry out the attack. Based on the results obtained, regular expressions are written that can find such constructions. For instance, by analyzing HTTP headers such as Server: Apache Tomcat/7.0.x, WAF can block a response and thereby prevent server information leakage or, alternatively, raise an alert.
However, this approach has a number of drawbacks. The range of applicability of a regular expression is limited to one query, and often even a specific query parameter, which obviously reduces the effectiveness of such requests. Secondly, the syntax of regular expressions, the complex logic of text protocols, allowing the replacement of equivalent constructs and the use of different representations of symbols, lead to errors when creating such rules. The table below shows the most common bypass techniques.
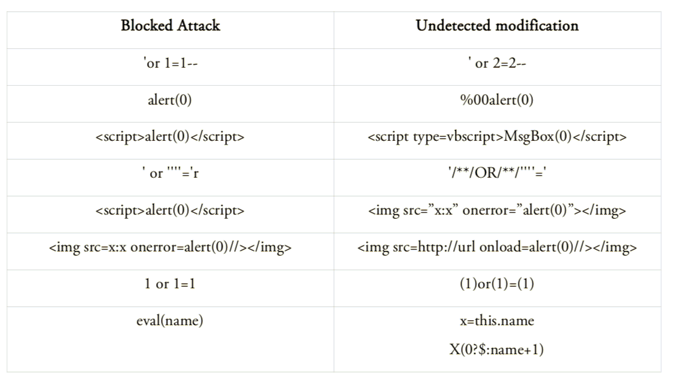
SQL obfuscation. It is possible to change the expression so that, using the syntax of the language, it can get rid of spaces. For example, in SQL, you can use brackets and stars:
s/*/e/**//*e*//*/l/*le*c*//*/ect~~/**/1 or /id=1+un/**/ion+sel/**/ect+1,2,3--
The other is based on using different encodings in such a way that the WAF does not decode the data in certain places. For example, after replacing one character with its url-code in the normalisation process, WAF will not be able to understand that it is necessary to decode the data and skip the request, while the same parameter will be accepted and successfully decoded by the web application.

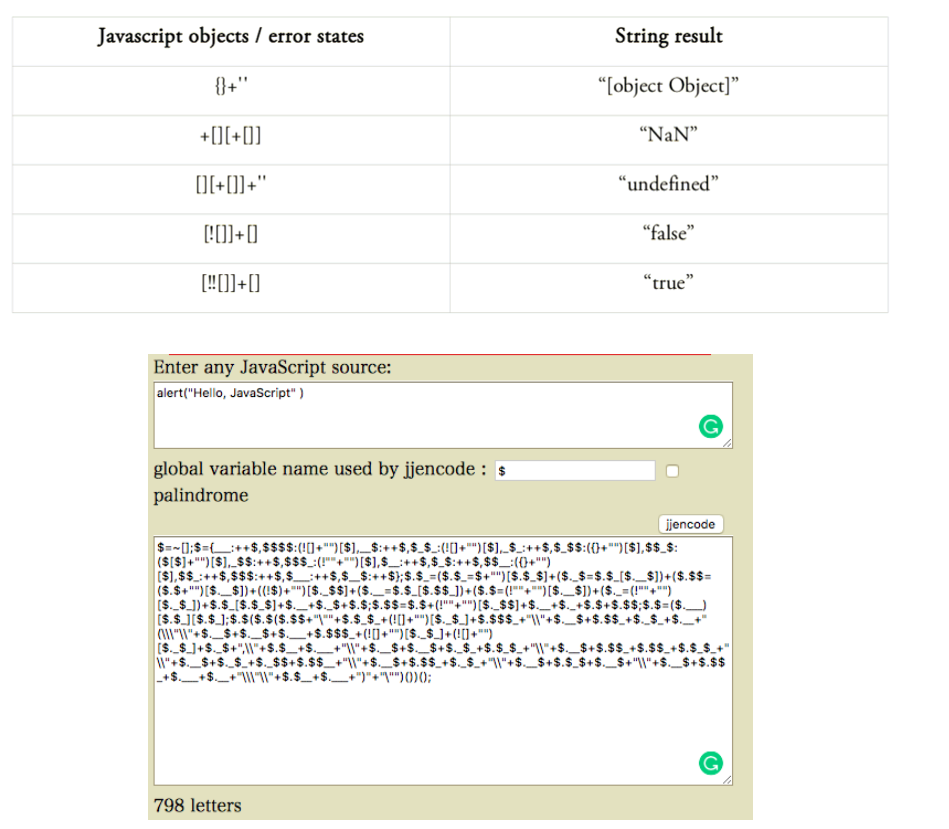
Search for atypical equivalent syntactic constructions. This method is used to find a way of operation that could not be considered by WAF developers, or the vector was absent in the study sample for machine learning. One of these constructs is the Non-alphanumeric Javascript code representation, an example of which is shown below.
Score building method
This approach does not detect attacks, but it complements other methods, making them more precise and flexible. The reason for the introduction of the tool is that the presence in the query of some suspicious design is insufficient for detecting an attack, or, on the contrary, it can lead to a large number of false-positive errors. This problem is solved by introducing a scoring system. For example, each rule based on regular expressions is supplemented with information about the criticality of its operation; After identifying all the worked rules, their criticality is summarised. In the case of overcoming a certain threshold value, the attack is detected and the request is blocked.
Behavior Analysis
Detecting attempts to exploit vulnerabilities in query parameters is not the only task of WAF. It is important to identify the vulnerability search procedure itself, which can manifest itself in attempts to scan, directory brute force, parameter fuzzing, and other methods of vulnerability detection that are often used by automated tools, and react accordingly to them. More advanced WAFs even know how to build an XML file with query chains that are typical for normal user behaviour and block attempts to send requests in a different order than standard behaviour. This mechanism not only counteracts attacks, but also complicates the process of finding a vulnerability.
Tokeniser parser analysers
This approach to detecting attacks is a complex concept; however, it is not easy to disassemble it on the C ++ primer of the Libinjection library, which allows to quickly and accurately detect SQL injection attacks. At present, for the Libinjection library, there are ports for various programming languages, including Java, C and Python. The mechanism is reduced to the search for signatures, represented as a sequence of tokens. Some of the signatures are added to the built-in black list and are considered unacceptable or malicious. In other words, before you analyse any query, it first leads to a set of tokens. Tokens are divided into different types, string, char, regular operator, number, comment, variable, etc.
One of the main drawbacks of this method is that it is possible to construct such a design that will lead to the incorrect formation of tokens; hence, the signature of the request will be different from the expected one.
Attacks directed at tokenisers are associated with attempts to break the logic by breaking the request into tokens using token-breakers. These are such symbols that allow you to influence the choice of a string element to match a specific token, and, thus, bypass the search by signatures. In open access, there are some cheat sheets, obtained by Mysql fuzzing and subsequent query checking in Libinjection.
Reputation analysis
The reputation mechanism is directly inherited from firewalls and antiviruses. Today, almost any WAF includes lists of addresses of VPN services, anonymisers, Tor network nodes and botnet participants which can be used to block requests originating from suspicious addresses. More advanced WAFs are able to automatically update their databases and make additional entries based on the analysed traffic.
Summary
In general, the Web Application Firewall is a modern and good protection tool, and it will never be superfluous for web applications. The main idea of finding ways to bypass WAF is to bring the requested query to a form in which it is still understandable to the attacked web application, but it is not understandable or seems not harmless for WAF.
However, there are several classes of vulnerabilities that WAF cannot detect. This can be any logical vulnerability, in this case there are no abnormal behaviours in the requests. Moreover, some studies conducted to optimise WAF rules also show methods of excluding legitimate requests from the inspection process, which can be potentially dangerous. WAF is also most likely to be of no use in identifying rivals, such as race condition and unsafe user authentication.
Reference
Vladimir Ivanov (2016) Tables of allowed symbols in different inputs of SQL expression, result of parsing fuzz tables. Available at: www.blackhat.com/docs/us-16/materials/us- 16-Ivanov-Web-Application-Firewalls-Analysis-Of-Detection-Logic.pdf
Torrano-Gimenez, C., Perez-Villegas, A. and Alvarez, G. (2009) ‘A Self-learning Anomaly- Based Web Application Firewall’, Springer, Berlin, Heidelberg. doi: doi.org/10.1007/978-3-642-04091-7_11.
Ramsingh, C. and Centonze, P. (2017) ‘Program Analysis For Database Injections’, INTERNATIONAL JOURNAL OF COMPUTERS & TECHNOLOGY, 16(6), pp. 6977– 6986. doi: 10.24297/ijct.v16i6.6332.
Prokhorenko, V., Choo, K. K. R. and Ashman, H. (2016) ‘Web application protection techniques: A taxonomy’, Journal of Network and Computer Applications, 60, pp. 95–112. doi: 10.1016/j.jnca.2015.11.017.
Prandl, S., Lazarescu, M. and Pham, D. (2015). A Study of Web Application Firewall Solutions. Information Systems Security, pp.501-510. doi: 10.1007/978-3-319-26961-0_29.
Positive-Technologies (2016a) ‘Web Application Firewalls: Attacking detection logic mechanisms’. Available at: www.blackhat.com/docs/us-16/materials/us-16-Ivanov- Web-Application-Firewalls-Analysis-Of-Detection-Logic.pdf.
OWASP (2017) SQL Injection Bypassing WAF. Available at: www.owasp.org/index.php/SQL_Injection_Bypassing_WAF.
