One of the most time-consuming steps while implementing a SIEM solution is writing and tuning "Playbook" document – a set of reaction procedures SOC Team has to follow in case of alert triggering.
During one of our implementation projects I stoped for a moment and thought: how can I optimize (ideally automate) the Playbook execution – in a playful way?
<cut/>
First of all – how does Playbook looks like? Here is a basic snippet of this document:
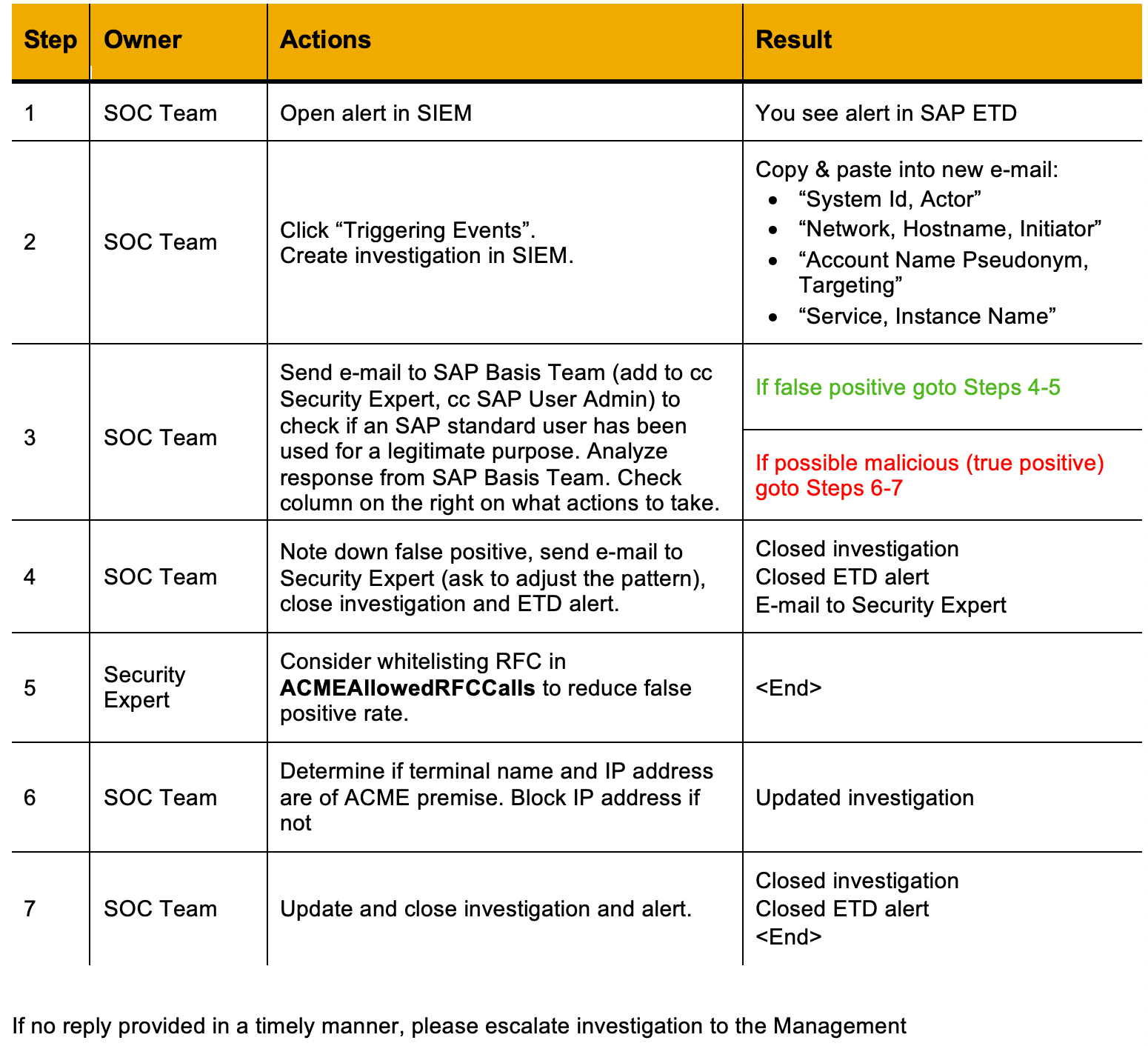
One of the ideas I could come up with was – hey, why don't we add some AI on top of it? Everyone is doing AI nowadays, isn't it? Can we automate SOC activities with some extra help of a Chatbot?
TensorFlow is one of the well known free and open-source libraries available for machine learning and deep neural networks and it was the first thing to investigate.
OK, now I forgot to mention one substantial fact – our SIEM solution (Enterprise Threat Detection, or SAP ETD) comes from SAP SE, which means this SIEM solution runs on SAP HANA as a platform. How can I integrate Tensorflow into HANA platform?
Quick research confirmed that it was possible:
Tensorflow Machine Learning Model Integration with SAP HANA
Nowadays we can integrate TensorFlow even with ABAP environment:
How To Use TensorFlow Seamlessly Inside ABAP
OK, Google, that goes far beyond my humble research..
So I decided to focus on end-to-end solutions. Let's try to make use of SAP Conversational AI (CAI). Luckily, there is a trial service available, hopefully no programming skills is necessary.
Now that I am logged onto a trial version CAI, let's create a "performing actions" Chatbot named "SEC", which would be (at least) able to participate in some basic discussions, such as greetings, small talks and weather:
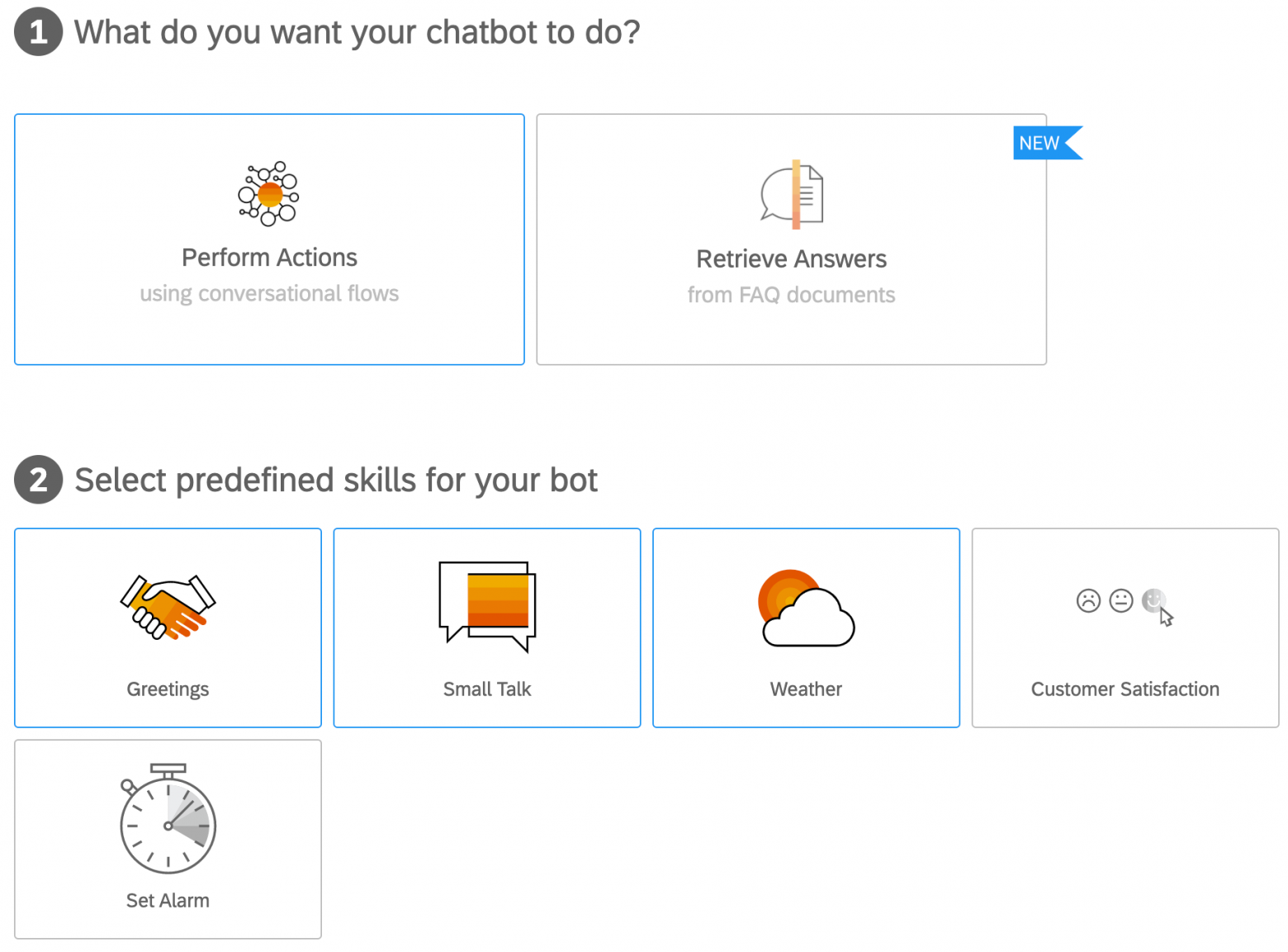
This newly born bot is already able to do some basic activities, but let's add some extra security-relevant capabilities (intents) to it:
Initiator – collect information about attacker's terminal id
Username – collect information about attacker's username
System – collect information about attacker's system
Inform – inform SAP Basis Team about possible attacker in their system
Alert – collect information about triggered alert
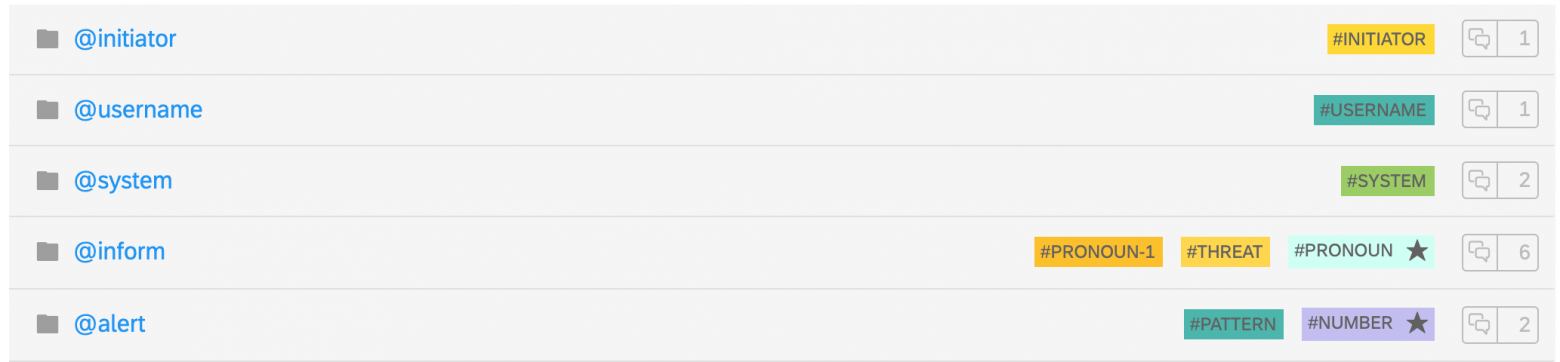
Now we group these new "intents" into new "skills" so that our bot would be able to "register alerts" and "talk to basis":
The last thing I want to do is of course bot training:

When training is finished I can test the bot:

When the bot says "We have blocked this terminal..." that's no joke because one of the "talk to basis" skills was calling external APIs:

What do you think of Chatbot helping SOC Team registering alerts and reacting to threats? Tell in comments
