How to understand when proxies are lying: verification of physical locations of network proxies using an active geolocation algorithm
People all over the world use commercial proxies to hide their true location or identity. This can be done to solve various tasks, including accessing blocked information or ensuring privacy.
But how correct are the providers of such proxies when they claim that their servers are located in a certain country? This is a fundamentally important question, the answer to which depends on whether it is possible to use a certain service at all for those customers who are concerned about protecting personal information.
A group of American scientists from the Universities of Massachusetts, Carnegie Mellon and Stony Brook published a study in which they checked the real locations of the servers of seven popular proxy providers. We have prepared a short summary of the main results.
Introduction
Proxy operators often do not provide any information that could confirm the accuracy of their statements about the location of servers. IP-to-location databases usually confirm the advertising theses of such companies, however, there is a large amount of evidence of errors in these databases.
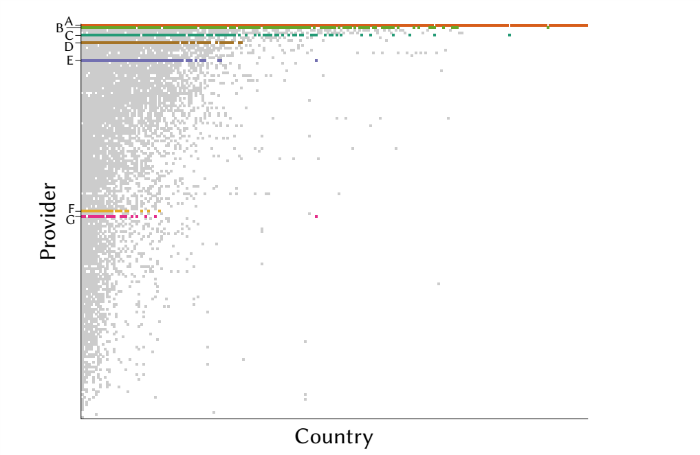
In the course of the study, American scientists estimated the location of 2,269 proxy servers operated by seven proxy companies and located in a total of 222 countries and territories. The analysis showed that at least a third of all servers are not located in the countries that companies claim in their marketing materials. Instead, they are located in countries with cheap and reliable hosting: The Czech Republic, Germany, the Netherlands, the United Kingdom, and the United States.
Server locations analysis
Commercial VPN and proxy providers can affect the accuracy of the IP-to-location databases – companies have the ability to manipulate, for example, location codes in router names. As a result, marketing materials may claim a large number of locations available to users, whereas in reality, to save money and improve reliability, servers are physically located in a small number of countries, although IP-to-location databases indicate the opposite.
To check the real locations of the servers, the researchers used an active geolocation algorithm. It was used to evaluate the roundtrip of a packet sent to the server side and to other well-known hosts on the Internet.
At the same time, only less than 10% of the tested proxies respond to ping, and scientists could not run any measurement software on the server itself for obvious reasons. They only had the ability to send packets through a proxy, so the roundtrip to any point in space is the amount of time it takes for a packet to reach from the test host to the proxy and from the proxy to the destination.

During the research, specialized software was developed based on four active geolocation algorithms: CBG, Octant, Spotter, and hybrid Octant/Spotter. The solution code is available on GitHub.
Since it was impossible to rely on the IP-to-location database, the researchers used a list of RIPE Atlas anchor hosts for the experiments – the information in this database is available online, it is constantly updated, and the documented locations are correct, moreover, hosts from the list constantly send ping signals to each other and update roundtrip data in a public database.
The solutions developed by scientists is a web application that establishes secure (HTTPS) TCP connections over an unsecured HTTP 80 port. If the server is not responding to this port, then a failure will occur after one request, however, if the server is responding to this port, the browser will receive a SYN-ACK response with the TLS ClientHello packet. This will trigger a protocol error, and the browser will display the error, but only after the second roundtrip.
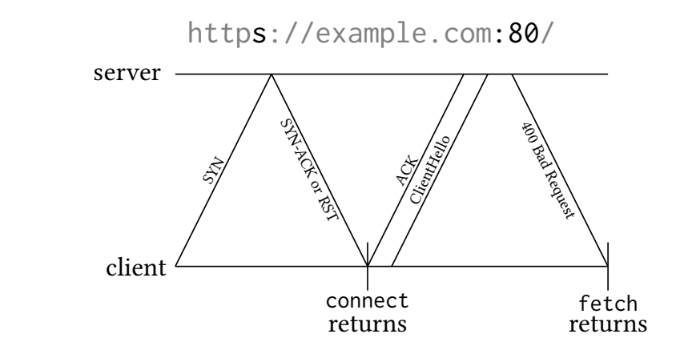
Thus, the web application can measure the time of one or two roundtrips. A similar service was implemented in the form of a program run from the command line.
None of the tested providers names the exact location of their proxy servers. At best, cities are mentioned, but most often there is information only about the country. Even when the city is mentioned, incidents can occur – for example, researchers studied the configuration file of one of the servers called usa.new-york-city.cfg, which contained instructions for connecting to a server called chicago.vpn-provider.example. So you can more or less accurately confirm only that the server belongs to a specific country.
Results
Based on the results of tests using the active geolocation algorithm, the researchers were able to confirm the locations of 989 of the 2,269 IP addresses. In the case of 642, this could not be done, and 638 are definitely not in the country where they should be according to the assurances of the
proxy services. More than 400 of these false addresses are actually located on the same continent as the declared country.
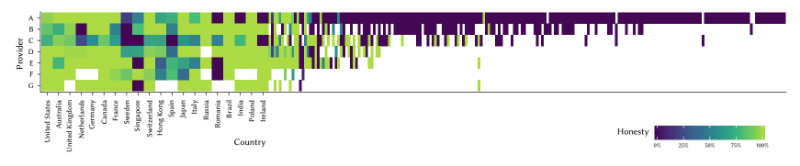
Suspicious hosts were found on each of the seven providers tested. The researchers asked the companies for comments, but they all declined to communicate.