For the first time PVS-Studio provided support for the CWE classification in the 6.21 release. It took place on January 15, 2018. Years have passed since then and we would like to tell you about the improvements related to the support of this classification in the latest analyzer version.

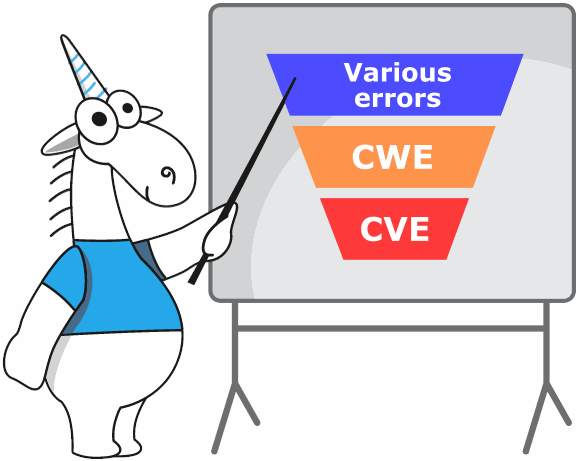
We position the PVS-Studio analyzer as a Static Application Security Testing (SAST) tool. This means our analyzer not only detects typos and errors in code, but also searches for potential vulnerabilities and correlates them with various standards (CWE, OWASP, SEI CERT, MISRA, AUTOSAR, etc.). Why potential vulnerabilities? Because potential vulnerabilities (CWE) may become real vulnerabilities (CVE) only if someone exploits them. And to make it happen many, sometimes unrelated, factors must often coincide.
That's why we decided to check how well PVS-Studio covers the most common defects now. To do this, it's enough to refer to the CWE Top 25 list. Somehow, we missed this list. Well, it's time to make amends!
CWE. What this is and what it is for
Let's refresh some moments and definitions in memory. If you're already good at terminology and know the difference between CVE and CWE, why we need CVSS and how CWE Top 25 is ranked, you can skip this part. Otherwise, I strongly recommend that you refresh those terms before you read the article. Below is a rather free interpretation of some points of CWE FAQ and CVE FAQ:
How does a software defect differ from a software vulnerability?
Defects are errors, failures and other problems of implementation, design or architecture of the software that can lead to vulnerabilities.
Vulnerabilities are errors that have already been found by someone. Attackers may use these vulnerabilities to get access to a system or a network, to disrupt services, etc.
What is CWE? How is it different from CVE and what does CVSS have to do with it?
- CWE (Common Weakness Enumeration) is a general list of security defects.
- CVE (Common Vulnerabilities and Exposures) is a list of vulnerabilities and defects found in various software.
- CVSS (Common Vulnerability Scoring System) is a numerical score that indicates the potential severity of a vulnerability (CVE). It is based on a standardized set of characteristics.
What is CWE Top 25?
CWE Top 25 is a list of the most dangerous and common defects. These defects are dangerous because someone can easily find and exploit them. Attackers can use them to disrupt the application's operation, steal data or even completely take over a system. CWE Top 25 is a significant community resource. It helps developers, testers, users, project managers, security researchers and teachers. They use this list to get an idea of the most common and dangerous security defects now.
What is an algorithm to compile and rank the CWE Top 25 list?
To create the current version of CWE Top 25, the CWE Team used data from U.D National Vulnerability Database (NVD) for 2019–2020. Next, the team of researchers used their own formula to calculate the ranking order. This formula takes into account the frequency, with which a defect (CWE) is the main cause of a vulnerability, and the potential danger of exploitation. The team made the formula that way, so it normalizes the frequency and predicted severity relative to their minimum and maximum values.
To obtain the frequency of mentions, the formula calculates how many times CVE referred to CWE within the NVD. The formula uses only those CVEs, which have a reference to CWE. If the formula uses the full data set, it will lead to very low frequency rates and an insignificant difference amongst the different types of defects.
Freq = {count(CWE_X' ∈ NVD) for each CWE_X' in NVD}
Fr(CWE_X) = (count(CWE_X ∈ NVD) — min(Freq)) / (max(Freq) — min(Freq))
Another important component of the scoring formula is a defect's severity. The following formula calculates it:
Sv(CWE_X) = (average_CVSS_for_CWE_X — min(CVSS)) / (max(CVSS) — min(CVSS))
At the end, the final score is calculated by multiplying the frequency of mention by the severity score.
Score(CWE_X) = Fr(CWE_X) * Sv(CWE_X) * 100
This approach introduces a bias by analyzing only detected vulnerabilities and can potentially exclude a significant part of data. Although, the CWE Team believes that this approach helps to compile a more accurate CWE Top 25 list every year.
Is the Top 25 updated annually?
Yes, it is. For information about previous versions, visit CWE Top 25 archive.
Who participates in the development of CWE Top 25?
The CWE community includes individual researchers and representatives of numerous organizations, the scientific community, and government agencies. They are all interested in elimination of software defects. You can get a list of CWE Team members on the "CWE Community Members" page.
Why should I know that?
Today, developers use CWE as the main tool when discussing the elimination and / or minimizing security defects in the architecture, design, code, and software implementation. Organizations use CWE as a standard measure for evaluating software security verification tools and as a common baseline standard for identifying, preventing, and minimizing negative consequences.
Can you give us examples of errors?
The CWE classification covers the most common problems with the development of software and various equipment. For example:
- software defects: buffer overflows; errors in format strings; structure and data validation problems; common special elements manipulation; channel and path errors; handler errors; UI errors; pathname traversal and equivalence errors; authentication errors; resource management errors; insufficient data verification; code evaluation and injection problems; randomness and predictability problems;
- hardware defects: core and computation errors typically associated with CPUs, graphics, Vision, AI, FPGA, and uControllers; privilege separation and access control issues related to the identification and policy, shared resources, locking controls, and other features and mechanisms; power, clock, and reset concerns related to voltage, electrical current, temperature, clock frequency control and state saving/restoring.
Read more about classification on the cwe.mitre.org website.
The situation today
We have been using the CWE classification for PVS-Studio diagnostics for more than three years. Their number increases every year. In 2018, we covered only 94 points on the CWE list. Now it's almost 130. However, this article isn't about the total number of diagnostics. Let's talk about those that are included in the list of the most dangerous diagnostics in 2021. If you want to read the full list, you can get it in the "CWE compliance" section of our documentation.
Below is a table of correspondence between the CWE Top 25 2021 list and the PVS-Studio diagnostics, divided by programming languages. In the future, we are going to regularly update the table with the CWE Top 25 coverage on our website.
| # |
CWE ID |
Name |
Evaluation |
PVS-Studio diagnostics |
|---|---|---|---|---|
| 1 |
CWE-787 |
Out-of-bounds Write |
65,93 |
C++: V512, V557, V582, V645 C#: V3106 Java: V6025 |
| 2 |
CWE-79 |
Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') |
46,84 |
C#: V5610 |
| 3 |
CWE-125 |
Out-of-bounds Read |
24,90 |
C++: V512, V557, V582 C#: V3106 Java: V6025 |
| 4 |
CWE-20 |
Improper Input Validation |
20,47 |
C++: V739, V781, V1010, V1024, V5009 |
| 5 |
CWE-78 |
Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') |
19,55 |
C++: V1010, V5009 |
| 6 |
CWE-89 |
Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') |
19,54 |
C#: V5608 |
| 7 |
CWE-416 |
Use After Free |
16,83 |
C++: V623, V723, V758, V774, V1017 |
| 8 |
CWE-22 |
Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') |
14,69 |
C#: V5609 |
| 9 |
CWE-352 |
Cross-Site Request Forgery (CSRF) |
14,46 |
Coming in the future |
| 10 |
CWE-434 |
Unrestricted Upload of File with Dangerous Type |
8,45 |
Coming in the future |
| 11 |
CWE-306 |
Missing Authentication for Critical Function |
7,93 |
Coming in the future |
| 12 |
CWE-190 |
Integer Overflow or Wraparound |
7,12 |
C++: V629, V658, V673, V683, V1026, V1028, V5004, V5005, V5006, V5007, V5010, V5011 C#: V3113 Java: V6105 |
| 13 |
CWE-502 |
Deserialization of Untrusted Data |
6,71 |
C#: V5611 |
| 14 |
CWE-287 |
Improper Authentication |
6,58 |
Coming in the future |
| 15 |
CWE-476 |
NULL Pointer Dereference |
6,54 |
C++: V522, V595, V664, V713, V1004 C#: V3027, V3042, V3080, V3095, V3100, V3125, V3145, V3146, V3148, V3149, V3152, V3153, V3168 Java: V6008, V6060, V6093 |
| 16 |
CWE-798 |
Use of Hard-coded Credentials |
6,27 |
C++: V5013 C#: V5601 Java: V5305 |
| 17 |
CWE-119 |
Improper Restriction of Operations within the Bounds of a Memory Buffer |
5,84 |
C++: V512, V557, V582, V769, V783, V1004 |
| 18 |
CWE-862 |
Missing Authorization |
5,47 |
Coming in the future |
| 19 |
CWE-276 |
Incorrect Default Permissions |
5,09 |
Coming in the future |
| 20 |
CWE-200 |
Exposure of Sensitive Information to an Unauthorized Actor |
4,74 |
Coming in the future |
| 21 |
CWE-522 |
Insufficiently Protected Credentials |
4,21 |
Coming in the future |
| 22 |
CWE-732 |
Incorrect Permission Assignment for Critical Resource |
4,20 |
Coming in the future |
| 23 |
CWE-611 |
Improper Restriction of XML External Entity Reference |
4,02 |
Coming in the future |
| 24 |
CWE-918 |
Server-Side Request Forgery (SSRF) |
3,78 |
Coming in the future |
| 25 |
CWE-77 |
Improper Neutralization of Special Elements used in a Command ('Command Injection') |
3,58 |
Coming in the future |
The table shows that PVS-Studio now covers 52% (13 out of 25) of the CWE Top 25 2021 list. It seems that 52% is not so much. However, we continue to develop diagnostics further. In the future we will be able to find even more defects. If we reduce this list to the 10 most dangerous and common defects, the picture becomes clearer — the total coverage grows to 80%. :) But this is a completely different story.
Changes in the CWE Top 25 over the past year
For the most sophisticated, I suggest looking at a brief statistic on movements in the CWE Top 25 over the past year.
The five biggest upshifts:
| # |
CWE ID |
Name |
Position in 2020 |
Position in 2021 |
Annual change |
|---|---|---|---|---|---|
| 1 |
CWE-276 |
Incorrect Default Permissions |
41 |
19 |
22▲ |
| 2 |
CWE-306 |
Missing Authentication for Critical Function |
24 |
11 |
13▲ |
| 3 |
CWE-502 |
Deserialization of Untrusted Data |
21 |
13 |
8▲ |
| 4 |
CWE-862 |
Missing Authorization |
25 |
18 |
7▲ |
| 5 |
CWE-77 |
Improper Neutralization of Special Elements used in a Command ('Command Injection') |
31 |
25 |
6▲ |
The five biggest downshifts:
| # |
CWE ID |
Name |
Position in 2020 |
Position in 2021 |
Annual change |
|---|---|---|---|---|---|
| 1 |
CWE-200 |
Exposure of Sensitive Information to an Unauthorized Actor |
7 |
20 |
13▼ |
| 2 |
CWE-119 |
Improper Restriction of Operations within the Bounds of a Memory Buffer |
5 |
17 |
12▼ |
| 3 |
CWE-94 |
Improper Control of Generation of Code ('Code Injection') |
17 |
28 |
11▼ |
| 4 |
CWE-269 |
Improper Privilege Management |
22 |
29 |
7▼ |
| 5 |
CWE-732 |
Incorrect Permission Assignment for Critical Resource |
16 |
22 |
6▼ |
Most of the CWEs presented in the table above belong to categories that are difficult to analyze. We can explain their rating decline (and their appearance in this table). The community has improved its educational, instrumental, and analytical capabilities, thereby reduced the frequency of mentioning errors related to these categories.
«Newbies» in the Top 25:
| # |
CWE ID |
Name |
Position in 2020 |
Position in 2021 |
Annual change |
|---|---|---|---|---|---|
| 1 |
CWE-276 |
Incorrect Default Permissions |
41 |
19 |
22▲ |
| 2 |
CWE-918 |
Server-Side Request Forgery (SSRF) |
27 |
24 |
3▲ |
| 3 |
CWE-77 |
Improper Neutralization of Special Elements used in a Command ('Command Injection') |
31 |
25 |
6▲ |
And in the end — the defects that were dropped out of the CWE Top 25 in 2021:
| # |
CWE ID |
Name |
Position in 2020 |
Position in 2021 |
Annual change |
|---|---|---|---|---|---|
| 1 |
CWE-400 |
Uncontrolled Resource Consumption |
23 |
27 |
4▼ |
| 2 |
CWE-94 |
Improper Control of Generation of Code ('Code Injection') |
17 |
28 |
11▼ |
| 3 |
CWE-269 |
Improper Privilege Management |
22 |
29 |
7▼ |
Conclusion
I hope you enjoyed this article and understood the current terminology.
Fortunately, static analyzers help us fight potential vulnerabilities. Therefore, I suggest that you download and test the PVS-Studio static analyzer with your project. Maybe a couple of CWEs crept into your code and are about to become CVE :)
Additional links:
- Technologies used in the PVS-Studio code analyzer for finding bugs and potential vulnerabilities.
- Potential vulnerability.
- Zero-day vulnerability.
- What is the difference between DevOps and DevSecOps?
- OWASP, vulnerabilities, and taint analysis in PVS-Studio for C#. Stir, but don't shake.