Intercepting Program Startup on Windows and Trying to Not Mess Things Up
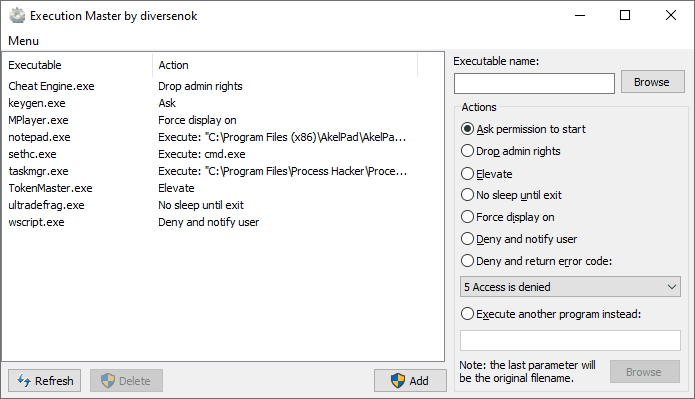
Have you ever heard of Image File Execution Options (IFEO)? It is a registry key under HKEY_LOCAL_MACHINE that controls things like Global Flags and Mitigation Policies on a per-process basis. One of its features that drew my attention is a mechanism designed to help developers debug multi-process applications. Imagine a scenario where some program creates a child process that crashes immediately. In case you cannot launch this child manually (that can happen for various reasons), you might have a hard time troubleshooting this problem. With IFEO, however, you can instruct the system to launch your favorite debugger right when it's about to start this troublesome process. Then you can single-step through the code and figure what goes wrong. Sounds incredibly useful, right?
I don't know about you, but I immediately saw this feature as a mechanism for executing arbitrary code when someone creates a new process. Even more importantly, it happens synchronously, i.e., the target won't start unless we allow it. Internally, the system swaps the path to the image file with the debugger's location, passing the former as a parameter. Therefore, it becomes the debugger's responsibility to start the application and then attach itself to it.
So, are there any limitations on what we can do if we register ourselves as a debugger? Let's push this opportunity to the limits and see what we can achieve.

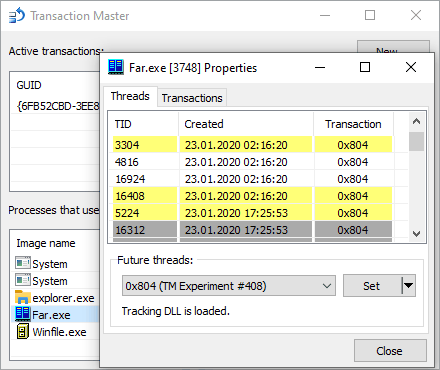 One of the modules in the Windows kernel provides support for combining a set of file operations into an entity known as a transaction. Just like in databases, these entities are isolated and atomic. You can make some changes to the file system that won't be visible outside until you commit them. Or, as an alternative, you can always rollback everything. In any case, you act upon the group of operations as a whole. Precisely what needed to preserve consistency while installing software or updating our systems, right? If something goes wrong — the installer or even the whole system crashes — the transaction rolls back automatically.
One of the modules in the Windows kernel provides support for combining a set of file operations into an entity known as a transaction. Just like in databases, these entities are isolated and atomic. You can make some changes to the file system that won't be visible outside until you commit them. Or, as an alternative, you can always rollback everything. In any case, you act upon the group of operations as a whole. Precisely what needed to preserve consistency while installing software or updating our systems, right? If something goes wrong — the installer or even the whole system crashes — the transaction rolls back automatically.