Java vs .Net: Who will Reign in the Future?

Here we will see the battle between Java and Microsoft .Net in order to make this clear which language is better to choose. For that, you may also have a quick look at this short video:

Before discussing the topic I’d like to start with a general suggestion not to use multiple inheritance and especially diamond unless you are strongly forced to. You may use e.g. composition or aggregation instead.
Well, “Diamond inheritance problem” is some kind of steady expression which formed many years ago. You can easily find a lot of articles suggesting usage of “virtual public” to avoid the ambiguity and so on. For instance, https://en.wikipedia.org/wiki/Multiple_inheritance

That is not wrong as for the problem stated but anyway it is quite one-side statement.
Below you can find:
Last October, I made the first demoscene production after an almost two-decades-long break — a demo for PICO-8 fantasy console “PICOCHAK: Attack of Donuts.” This article is “behind the scenes” or PICOCHAK.
The onslaught of data security breaches today is relentless, with thousands of major breaches each year and 50 percent more breaches in 2019 vs. 2018, according to a report by Risk Based Security. The costs for each breach have burgeoned as well, with the average cost of a data breach at about $3.92 million.
Securing data from breaches not only spares bottom line and publicity, it's now also a basic legal requirement to comply with rapidly growing data privacy laws.
While organizations have long had to comply with industry-specific standards, such as HIPAA in healthcare and the Payment Card Industry Data Security Standard (PCI DSS), you now also face new consumer privacy regulations. Including:
This is a post about first steps and first pitfalls in modernization of old enterprise application using "supersonic subatomic java" quarkus as it is positioned by RedHat.
In the end of 2019 I was invited to work in a project in our company, where an old monolithic application should be split into micro-services. Basic reasoning behind this decision was, that framework which is used in application is near to it's end-of-life. The application should be rewritten in any case. If it should be rewritten in any case, why not to split it into micro-services?
Since last 10 years, I was working mostly with java and we had in the project specialists with java knowledge, we have decided to give java-based frameworks a try for back-end functionality.
OK, let's use spring-cloud for that purpose, was our first thought. But then, we have had a look onto quarkus, which has been released in the end of 2019. We have decided to give it a try, keeping in mind building of native applications using GraalVM.
Native applications from our perspective could give us following benefits:
We were aware about possible drawbacks of this solution:
What would be the standard quick security related tuning to configure before you install the meat?
release: 2005, Ubuntu + CentOS (supposed to work with Amazon Linux, Fedora, Debian, RHEL as well)

In just a few years, quantum computing and quantum information theory has gone from a fringe subject offered in small classes at odd hours in the corner of the physics building annex to a full complement of classes in well-funded programs being held at quantum centers and institutes at leading universities.
The question now for many would-be quantum computer students is not, “Are there universities that even offer classes in quantum computing,” but, rather, “Which universities are leaders at quantum computing research.”
We’ll look at some of the best right now:
Good content makes customers loyal, forms a positive brand image, and raises sales in the long term. But it only works if content reaches its target audience. To bring together prospective clients and relevant messages content marketing platforms are used. Learn how they can improve campaigns of marketing agencies, media buyers, and companies.
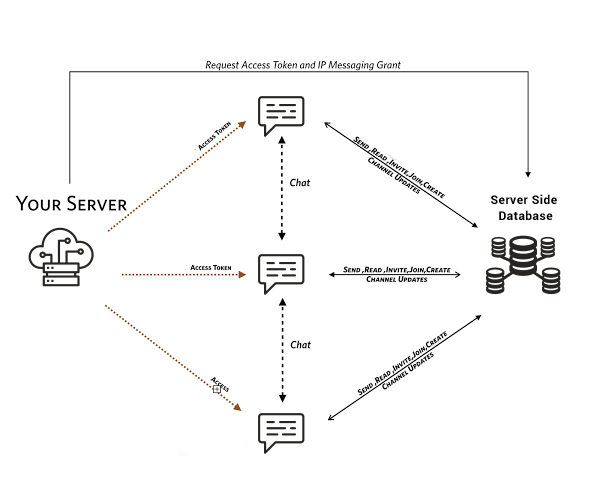


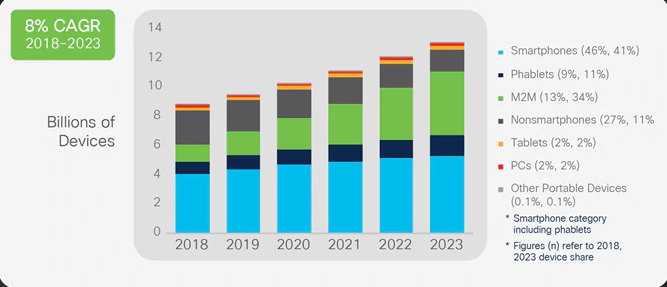
Source: Google Images

Authorization is one of the first problems developers face upon starting a new project. And one of the most common types of authorization (from my experience) is the token-based authorization (usually using JWT).
From my perspective, this article looks like "what I wanted to read two weeks ago". My goal was to write minimalistic and reusable code with a clean and straightforward interface. I had the next requirements for my implementation of the auth management: