PVS-Studio in the Clouds — Running the Analysis on Travis CI


.NET is a relative newcomer in the open-source world, and its popularity is nowhere near mainstream platforms like Node.js. So you can imagine there're few tutorials that deal with .NET and frameworks such as ASP.NET on Heroku. And those that do, probably won't use containers.
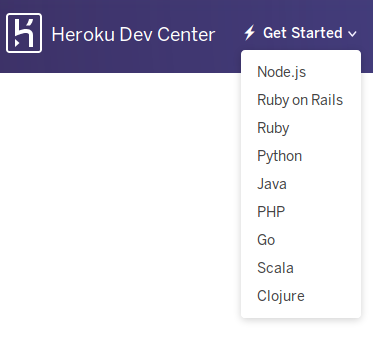
Do you see C#/.NET here? Yes, me neither.
My name is Vladimir, and I develop mobile front-end for Yandex Mail. Our apps have had a dark theme for a while, but it was incomplete: only the interface and plain emails were dark. Messages with custom formatting remained light and stood out against the dark interface, hurting our users’ eyes at night.
Today I'll tell you how we fixed this problem. You will learn about two simple techniques that didn't work for us and the method that finally did the trick — adaptive page recoloring. I'll also share some ideas about adapting images to a dark theme. To be fair, darkening pages with custom CSS is a rather peculiar task, but I believe some of you may find our experience helpful.



 Google loves easter eggs. It loves them so much, in fact, that you could find them in virtually every product of theirs. The tradition of Android easter eggs began in the very earliest versions of the OS (I think everyone there knows what happens when you go into the general settings and tap the version number a few times).
Google loves easter eggs. It loves them so much, in fact, that you could find them in virtually every product of theirs. The tradition of Android easter eggs began in the very earliest versions of the OS (I think everyone there knows what happens when you go into the general settings and tap the version number a few times).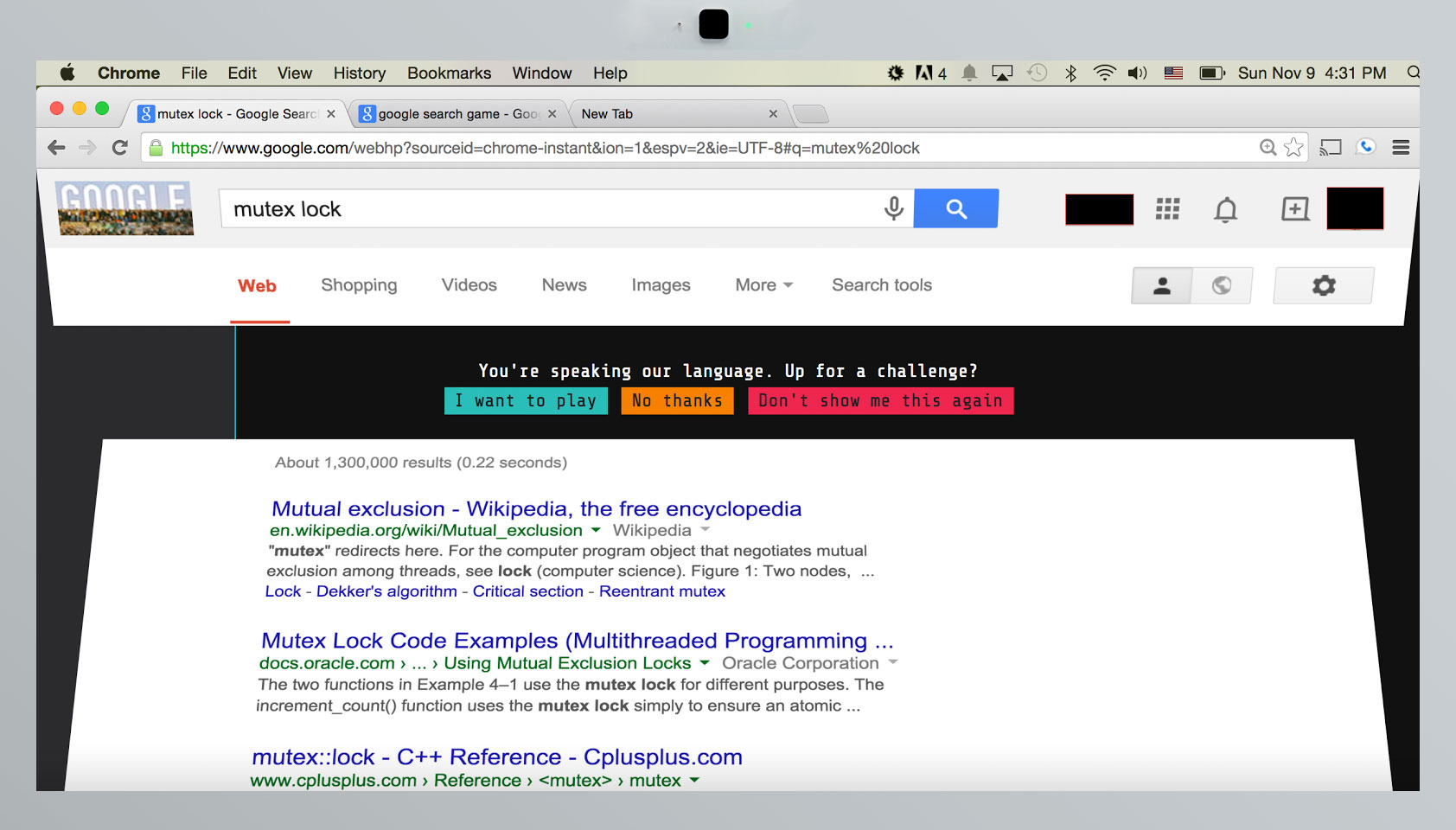

Hi. My name is Michael Kapelko. I've been developing software professionally for more than 10 years. Recent years were dedicated to iOS. I develop games and game development tools in my spare time.
Overview
Today I want to share my experience of teaching kids to program. I'm going to discuss the following topics:
 This article contains a brief squeeze from my own experience and that of my colleagues, with whom I had been fighting incidents day and night. And many incidents would never have occurred if all these microservices that we love so much were written at least a little more carefully.
This article contains a brief squeeze from my own experience and that of my colleagues, with whom I had been fighting incidents day and night. And many incidents would never have occurred if all these microservices that we love so much were written at least a little more carefully.
Unfortunately, some programmers seriously believe that a Dockerfile with any team at all inside is a microservice in itself and can be deployed even now. Dockers are running — money are incoming. This approach turns into problems starting from performance degradation, inability to debug, service failures and ending in a nightmare called Data Inconsistency.
If you feel that the time has come to launch one more app in Kubernetes / ECS / whatever, then I have something to object to.
In this article I'm going to tell you about one of the currying options and partial application of the functions in C++ which is my personal favourite. I'm also going to show my own pilot implementation of this thing and explain the point of currying without complex mathematical formula, making it really simple for you. We'll also see what's under the hood of kari.hpp library which we'll be using for currying functions. Anyway, there are lots of fascinating stuff inside, so welcome!


I'm stunned by the illogicality of others, and they are stunned by the fact that I'm a robot." This phrase perfectly describes the peculiarities of my interaction with the world around me. I'm like this robot. Or an alien. I can only guess how the other people see me. But now I know for sure that others consider me at least strange. The feeling is mutual. Many actions of people around me seem completely irrational and illogical to me.
For a long time, this baffled me. I didn't understand what was going on, and considered myself a deep introvert, a withdrawn, gloomy dude who did not understand people and their feelings at all. I kept wondering what was wrong with me…

Hello, everybody!
My name is Alexander Zubkov and today I’d like to talk about routing loops.

The third quarter of 2021 brought a massive upheaval in the scale and intensity of DDoS attacks worldwide.
It all led to September when together with Yandex, we uncovered one of the most devastating botnets since the Mirai and named it Meris, as it was held accountable for a series of attacks with a very high RPS rate. And as those attacks were aimed all over the world, our quarterly statistics also changed.
This quarter, we've also prepared for your consideration a slice of statistics on the application layer (L7) DDoS attacks. Without further ado, let us elaborate on the details of DDoS attacks statistics and BGP incidents for Q3, 2021.

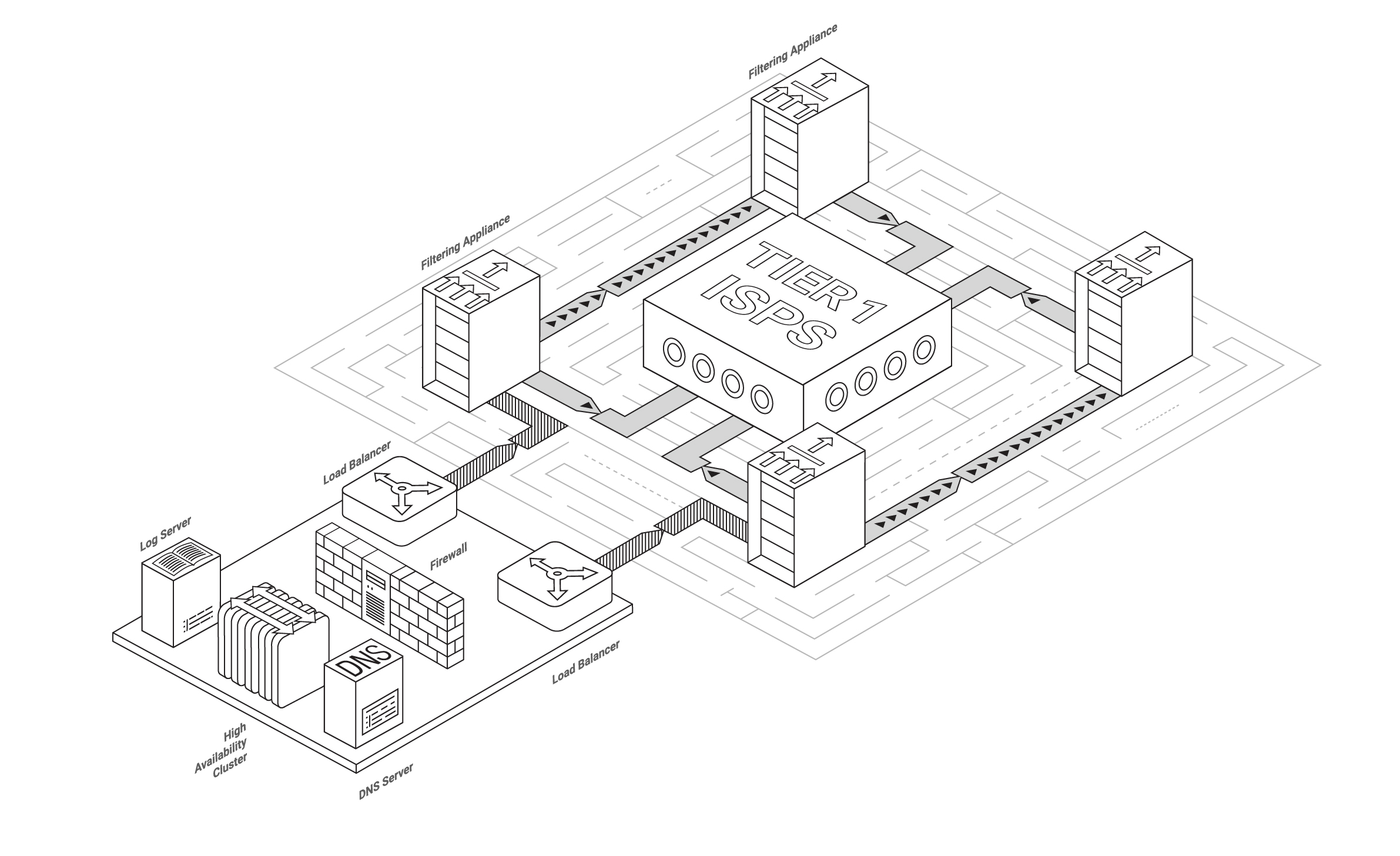
By the beginning of 2021, Qrator Labs filtering network expands to 14 scrubbing centers and a total of 3 Tbps filtering bandwidth capacity, with the San Paolo scrubbing facility fully operational in early 2021;
New partner services fully integrated into Qrator Labs infrastructure and customer dashboard throughout 2020: SolidWall WAF and RuGeeks CDN;
Upgraded filtering logic allows Qrator Labs to serve even bigger infrastructures with full-scale cybersecurity protection and DDoS attacks mitigation;
The newest AMD processors are now widely used by Qrator Labs in packet processing.
DDoS attacks were on the rise during 2020, with the most relentless attacks described as short and overwhelmingly intensive.
However, BGP incidents were an area where it was evident that some change was and still is needed, as there was a significant amount of devastating hijacks and route leaks.
In 2020, we began providing our services in Singapore under a new partnership and opened a new scrubbing center in Dubai, where our fully functioning branch is staffed by the best professionals to serve local customers.