Top 10 bugs of C++ projects found in 2018



If you have dabbled into microchip photographing before, then this article will probably not offer much to you. But if you want to get into it, but don’t know where to start, then it’s exactly for you.
Before we start, a fair warning: while the procedure is quite entertaining, at first it’ll probably be physically painful. The chemicals used during the process are toxic, so please handle them carefully – that way it’ll still hurt, but less so. Also, if you have even a slight amount of common sense, conduct the procedure in a fully-equipped chemical laboratory under supervision of trained professionals: we’ve had to deal with people who tried to do it at home immediately after reading the guide. And finally: if you don’t know whether you need to pour acid into water or water into acid without a Google search and don’t realize what this lack of knowledge will entail – stop reading this immediately and go to a chemistry 101 course in a local college or something.

There are only two hard things in Computer Science: cache invalidation
and naming things.
— Phil Karlton
We, developers, spend more time reading code than writing it. It is important for the code to be readable and clear about its intent.
Below are some advice based on my experience naming things.

We have a problem. The problem with testing. The problem with testing React components, and it is quite fundamental. It’s about the difference between unit testing and integration testing. It’s about the difference between what we call unit testing and what we call integration testing, the size and the scope.
It's not about testing itself, but about Component Architecture. About the difference between testing components, standalone libraries, and final applications.
Everyone knows how to test simple components(they are simple), probably know how to test Applications(E2E). How to test Finite and Infinite things…


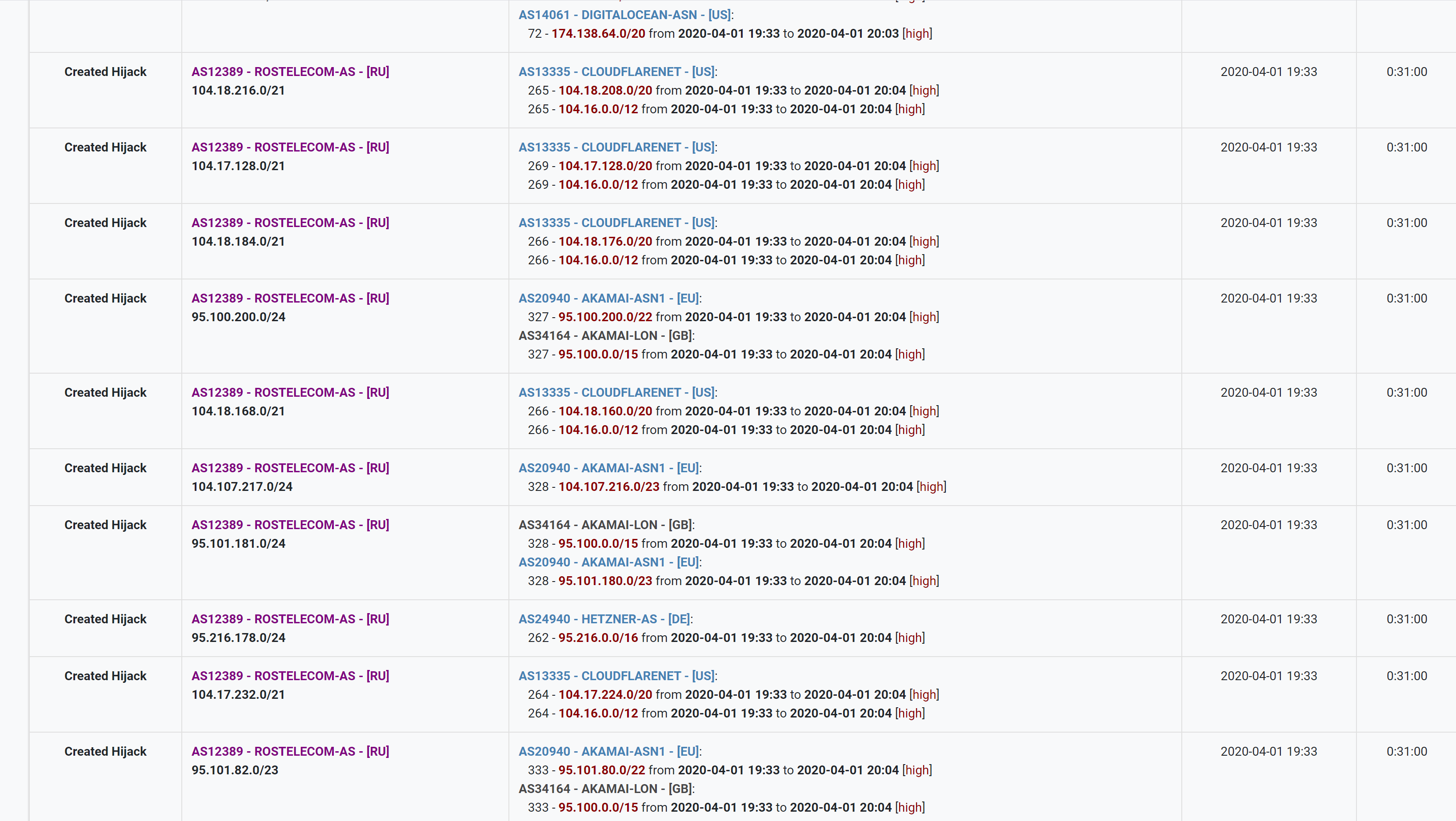

Most likely you've already heard about the famous exploit checkm8, which uses an unfixable vulnerability in the BootROM of most iDevices, including iPhone X. In this article, we'll provide a technical analysis of this exploit and figure out what causes the vulnerability.




In the beginning, there was the Word… which quickly became communication protocol in need of an upgrade.




