Best .Net Development Tools in 2020
Here are some of the top useful tools being used by many offshore .net development teams, .net developers, individual .net programmers, etc.

The technology of creating web applications and web services


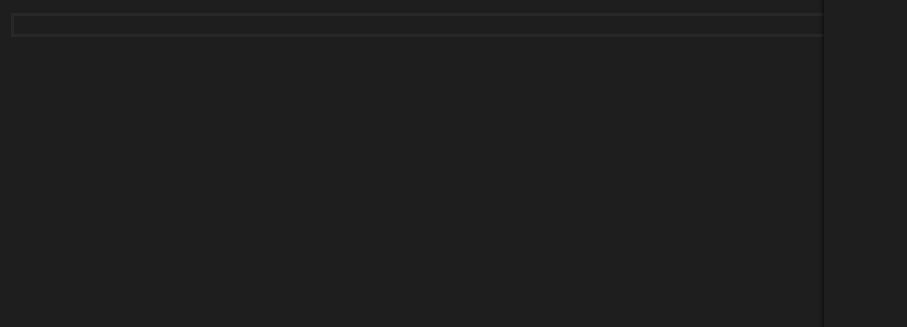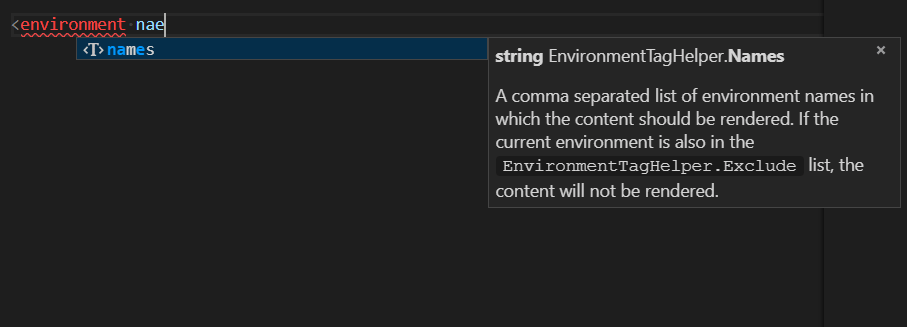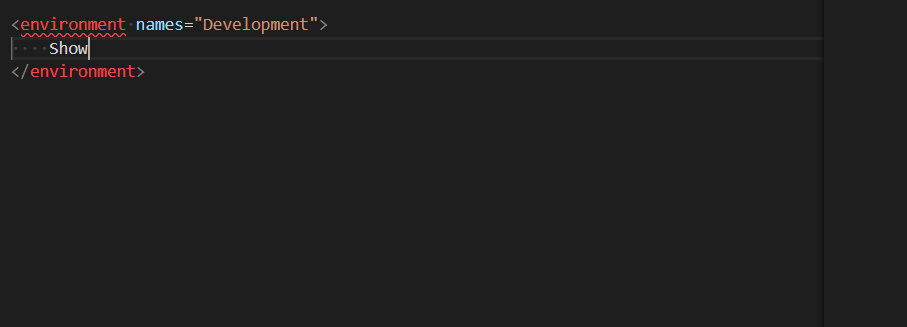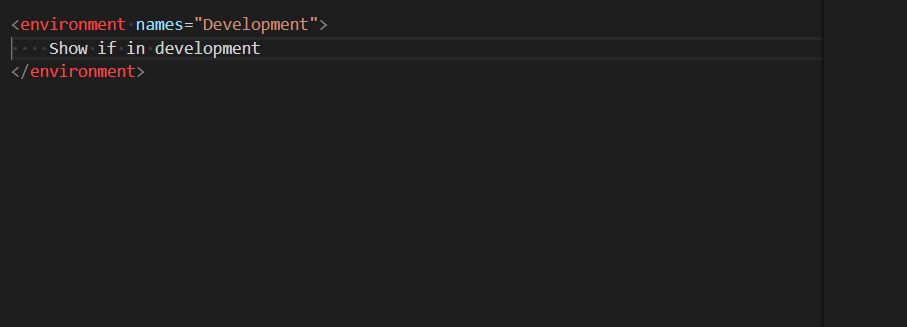
I'm putting part of older WebForms portions of my site that still run on bare metal to ASP.NET Core and Azure App Services, and while I'm doing that I realized that I want to make sure my staging sites don't get indexed by Google/Bing.
I already have a robots.txt, but I want one that's specific to production and others that are specific to development or staging. I thought about a number of ways to solve this. I could have a static robots.txt and another robots-staging.txt and conditionally copy one over the other during my Azure DevOps CI/CD pipeline.
Then I realized the simplest possible thing would be to just make robots.txt be dynamic. I thought about writing custom middleware but that sounded like a hassle and more code that needed. I wanted to see just how simple this could be.

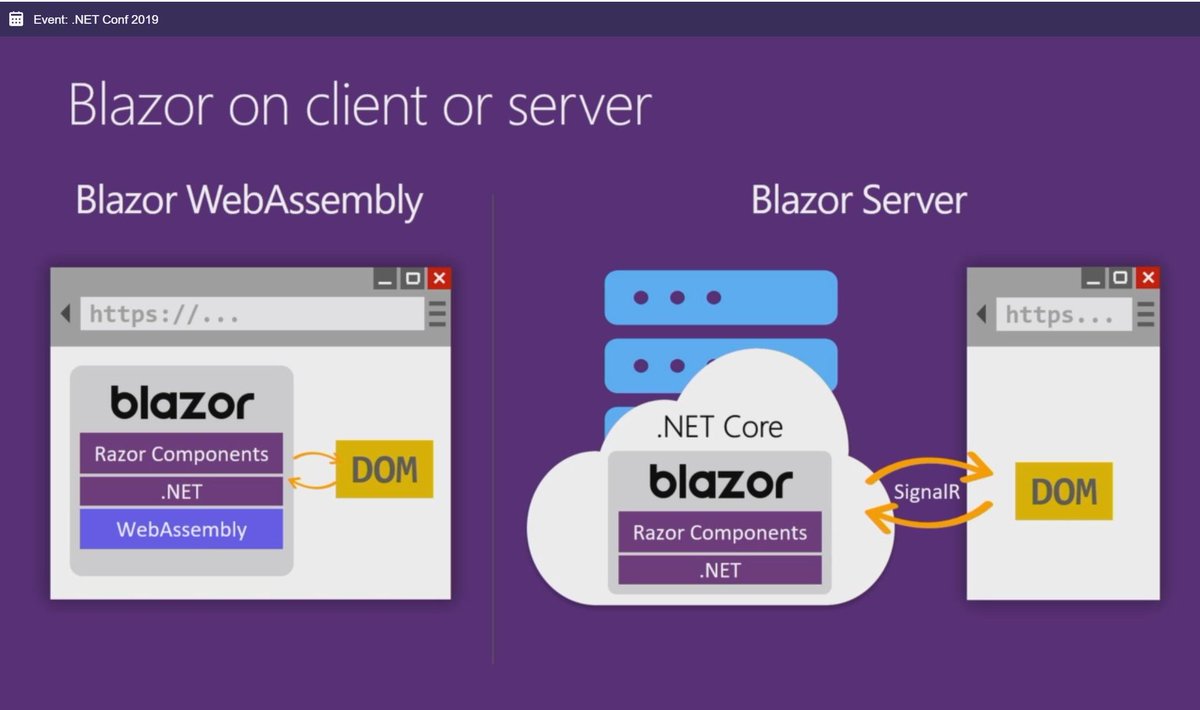
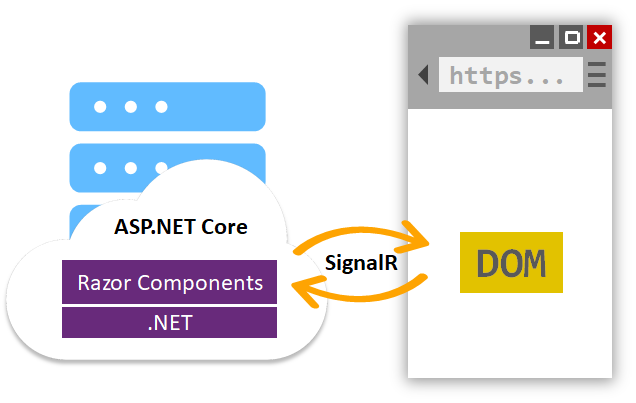
With this newest Blazor release we’re pleased to announce that Blazor is now in official preview! Blazor is no longer experimental and we are committing to ship it as a supported web UI framework including support for running client-side in the browser on WebAssembly.
A little over a year ago we started the Blazor experimental project with the goal of building a client web UI framework based on .NET and WebAssembly. At the time Blazor was little more than a prototype and there were lots of open questions about the viability of running .NET in the browser. Since then we’ve shipped nine experimental Blazor releases addressing a variety of concerns including component model, data binding, event handling, routing, layouts, app size, hosting models, debugging, and tooling. We’re now at the point where we think Blazor is ready to take its next step.

Some days ago we announced improved Razor tooling support in Visual Studio Code with the latest C# extension. This latest release includes improved Razor diagnostics and support for tag helpers and Blazor apps.
We are now publishing .NET Core container images to Microsoft Container Registry (MCR). We have also made other changes to the images we publish, described in this post.
Important: You will need to change FROM statements in Dockerfile files and docker pull commands as a result of these changes. 3.0 references need to be changed now. Most 1.x and 2.x usages can be changed over time. The new tag scheme is decribed in this post and are provided at the microsoft-dotnet-core repo, our new home on Docker Hub.
Summary of changes:

Blazor 0.9.0 is now available! This release updates Blazor with the Razor Components improvements in .NET Core 3.0 Preview 3.
New Razor Component improvements now available to Blazor apps:


Blazor 0.8.0 is now available! This release updates Blazor to use Razor Components in .NET Core 3.0 and adds some critical bug fixes.
To get started with Blazor 0.8.0 install the following:
The Blazor templates on the command-line:
dotnet new -i Microsoft.AspNetCore.Blazor.Templates::0.8.0-preview-19104-04You can find getting started instructions, docs, and tutorials for Blazor at https://blazor.net.
We love our .NET community that is filled with amazing developers writing fantastic blogs, libraries, presentations, and pull requests every week. We are always looking for ways to highlight this amazing work, and for over 4 years the ASP.NET team here at Microsoft has been hosting their ASP.NET Community Standups live on YouTube and now Twitch.
During the stream, they show off the latest and greatest community contributions along with all of the great open source work that the teams have been doing. As the .NET community expands so should the community standups, which is why we are pleased to introduce the expansion of their community standups that we officially call the “.NET Community Standup” series. These community standups span multiple teams and products in the world of .NET and show off the amazing work the community is doing.
