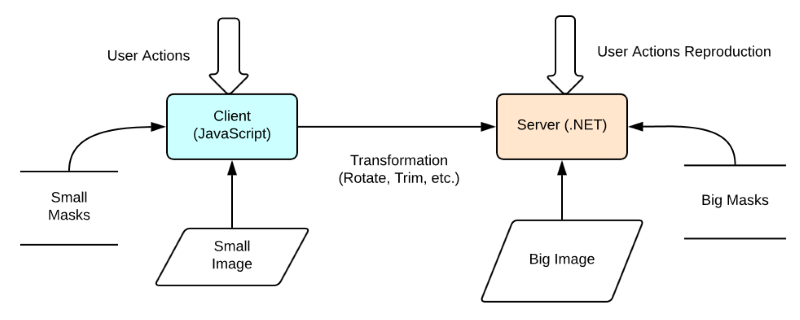
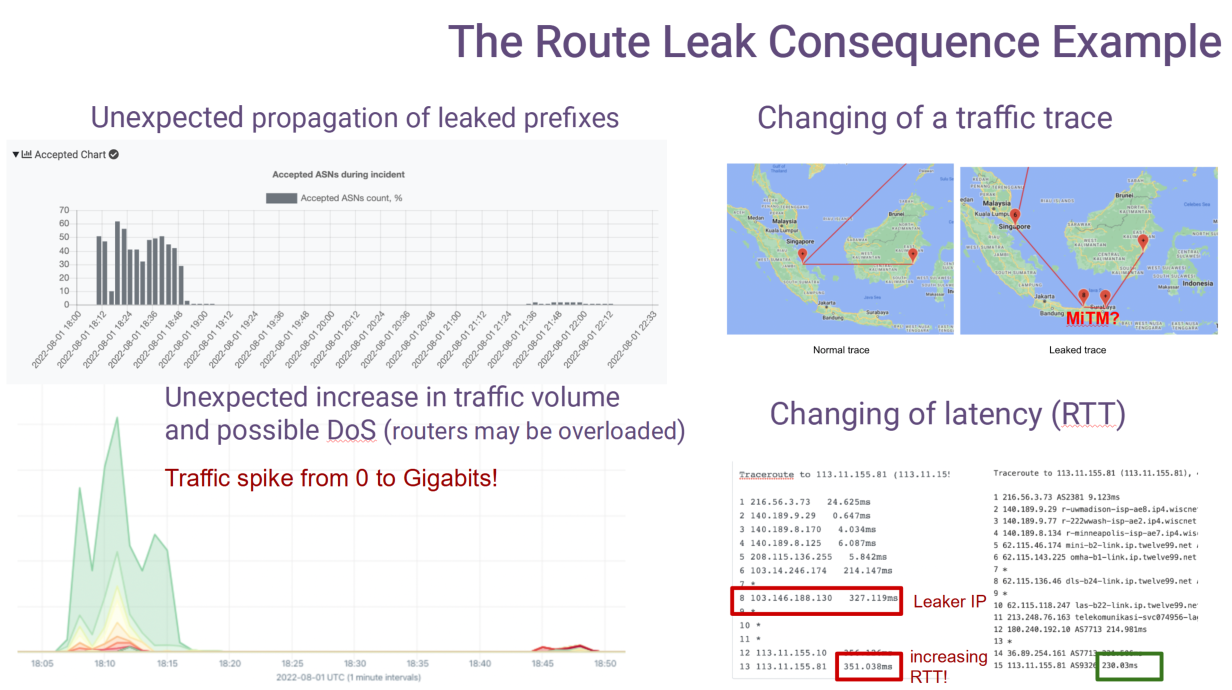
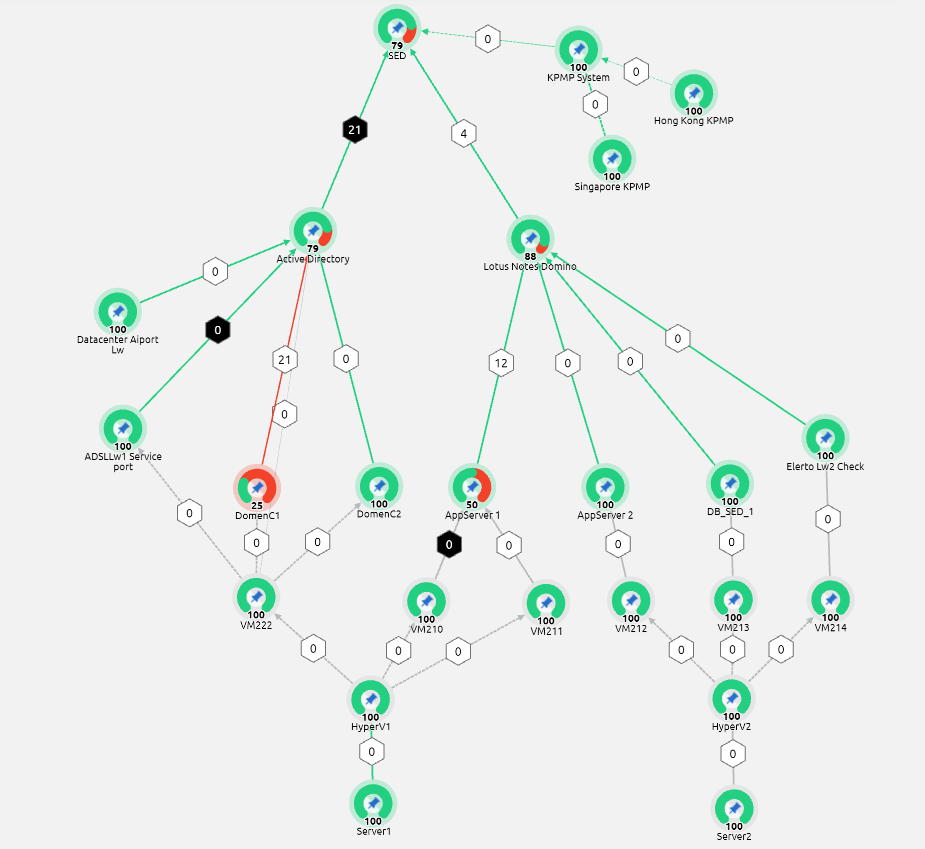
• Acquisition.
• Activation.
• Retention.
• Revenue.
• Referral.
AARRR (also called the Pirate Metrics) describes the sales funnel. At the top of the funnel are visitors who only saw your application, or just downloaded it and still do not know how they will interact with it. Next, visitors are registered — of course, if it is provided by the functionality of the application.
Now they (you can start calling them users) reach the moment when they have to understand the value of the product and decide to remain its user, i.e. start buying some services, recommend the application to your friends and, in general, constantly return to the application for any purpose, or delete it from mobile device.
You will not have another chance to impress the user!
The AARRR framework forces developers to measure their sales funnel numerically. At every stage.

 This chapter was translated from Russian jointly by author and by
This chapter was translated from Russian jointly by author and by