Q3 2022 DDoS attacks and BGP incidents

With the end of the 2022' third quarter, we invite you to take a tour into DDoS attacks mitigation and BGP incidents statistics recorded from July to September.

Infocenters + databases + communication systems

With the end of the 2022' third quarter, we invite you to take a tour into DDoS attacks mitigation and BGP incidents statistics recorded from July to September.

There are new challenges that force IT companies to look for non-trivial approaches to solve the problems of their customers every year. And as you know LANIT-Integration is not an exception. Our team has already managed to work with many products, but we never stop discovering new ones.
In this article I would like to provide an overview of backup and recovery software from Chinese vendors and to compare these solutions with domestic ones.

The second quarter of the year has ended and, as usual, we take a look back at the mitigated DDoS attacks activity and BGP incidents that occurred between April and June 2022.

The first quarter of the year 2022 has passed; now, it is time to look at the events of Q1 in terms of mitigated DDoS activity and recorded BGP incidents.
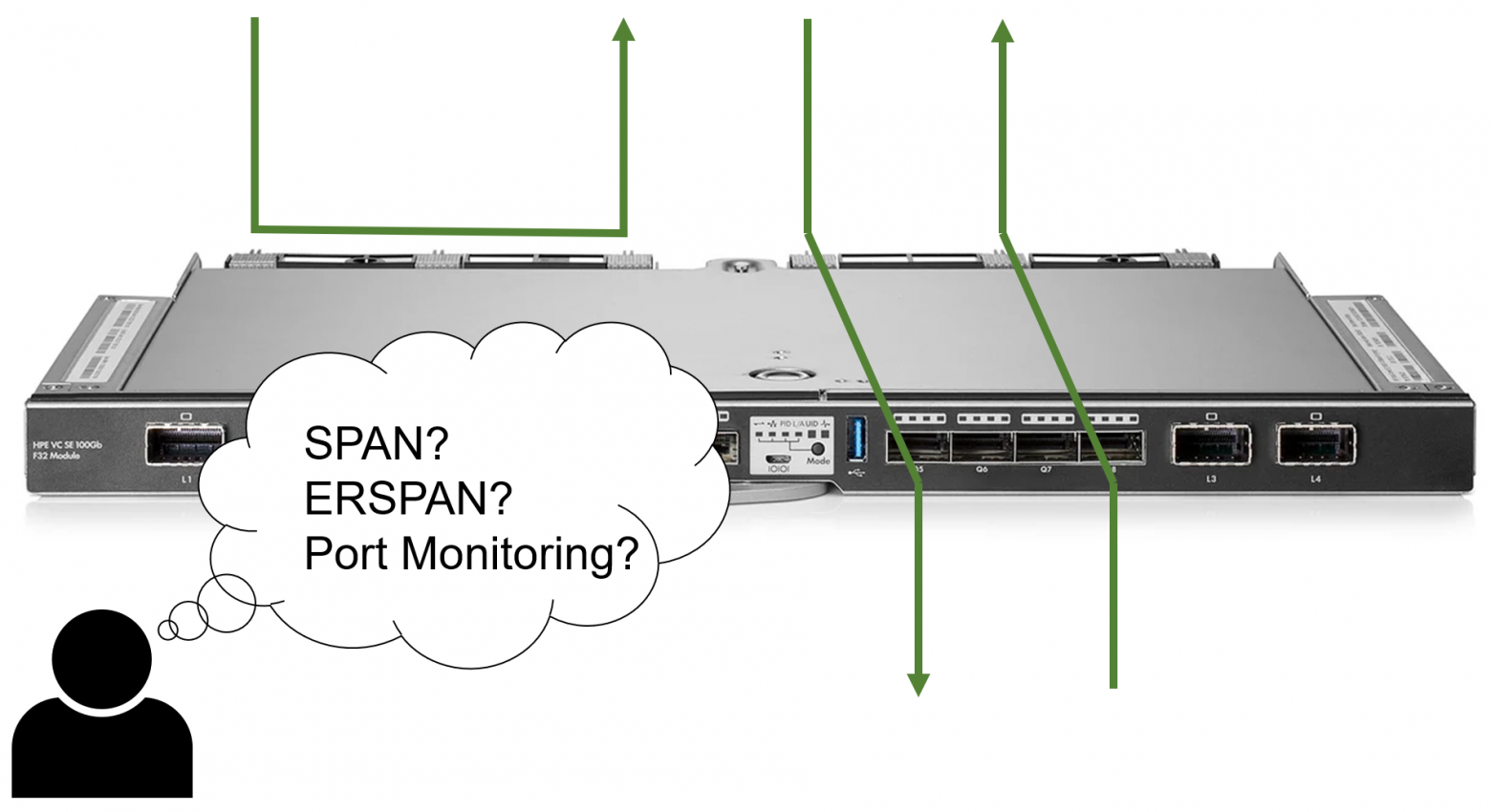
In this article I'd like to describe different traffic mirroring options for HPE Virtual Connect modules. I try to answer two questions: "What options work and why?" and "How different traffic mirroring cases can be implemented?"

2021 was an action-packed year for Qrator Labs.
It started with the official celebration of our tenth year anniversary, continued with massive routing incidents, and ended with the infamous Meris botnet we reported back in September.
Now it is time to look at the events of the last quarter of 2021. There are interesting details in the BGP section, like the new records in route leaks and hijacking ASes, but first things first, as we start with the DDoS attacks statistics.
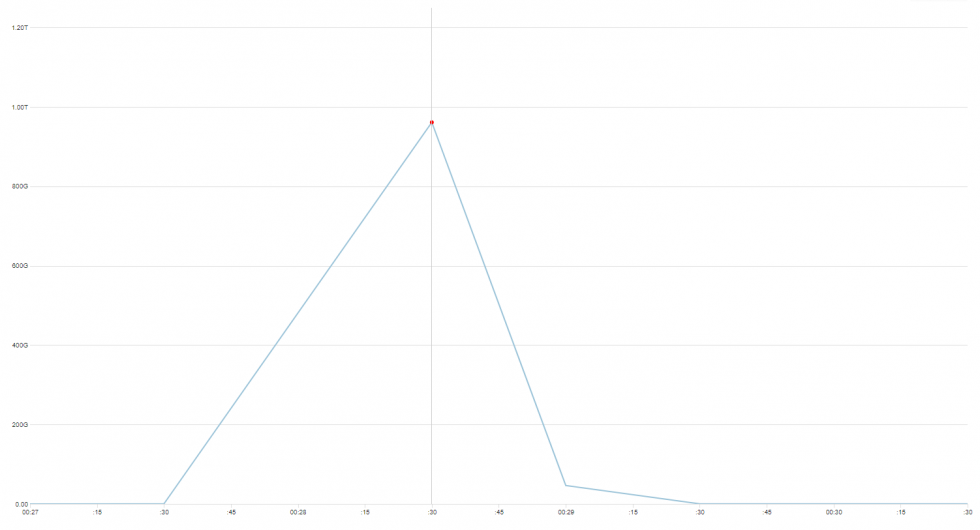
DDoS attacks send ripples on the ocean of the Internet, produced by creations of various sizes - botnets. Some of them feed at the top of the ocean, but there also exists a category of huge, deep water monstrosities that are rare and dangerous enough they could be seen only once in a very long time.
November 2021 we encountered, and mitigated, several attacks from a botnet, that seems to be unrelated to one described and/or well-known, like variants of Mirai, Bashlite, Hajime or Brickerbot.
Although our findings are reminiscent of Mirai, we suppose this botnet is not based purely on propagating Linux malware, but a combination of brute forcing and exploiting already patched CVEs in unpatched devices to grow the size of it. Either way, to confirm how exactly this botnet operates, we need to have a sample device to analyze, which isn’t our area of expertise.
This time, we won’t give it a name. It is not 100% clear what we are looking at, what are the exact characteristics of it, and how big this thing actually is. But there are some numbers, and where possible, we have made additional reconnaissance in order to better understand what we’re dealing with.
But let us first show you the data we’ve gathered, and leave conclusions closer to the end of this post.
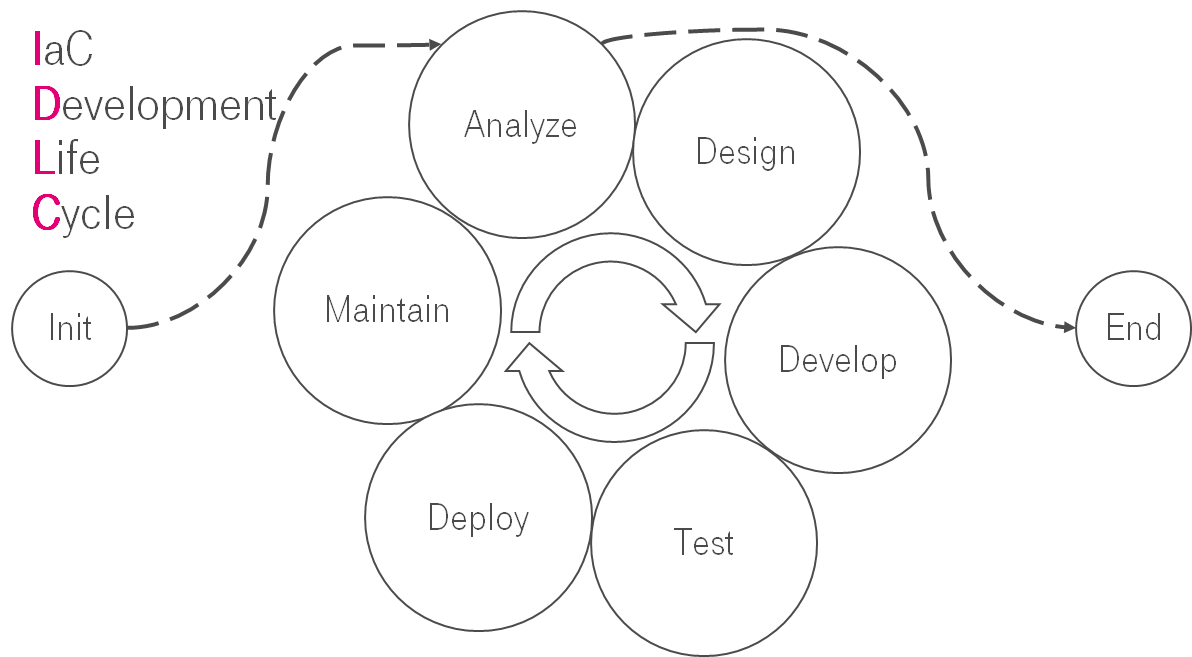
This is the translation of my speech at T-Meetup: DevOps Life Cycle.
I believe that you have heard about SDLC (Systems development life cycle). Is it possible that the same things are applicable for the IaC?

The third quarter of 2021 brought a massive upheaval in the scale and intensity of DDoS attacks worldwide.
It all led to September when together with Yandex, we uncovered one of the most devastating botnets since the Mirai and named it Meris, as it was held accountable for a series of attacks with a very high RPS rate. And as those attacks were aimed all over the world, our quarterly statistics also changed.
This quarter, we've also prepared for your consideration a slice of statistics on the application layer (L7) DDoS attacks. Without further ado, let us elaborate on the details of DDoS attacks statistics and BGP incidents for Q3, 2021.

Introduction
For the last five years, there have virtually been almost no global-scale application-layer attacks.
During this period, the industry has learned how to cope with the high bandwidth network layer attacks, including amplification-based ones. It does not mean that botnets are now harmless.
End of June 2021, Qrator Labs started to see signs of a new assaulting force on the Internet – a botnet of a new kind. That is a joint research we conducted together with Yandex to elaborate on the specifics of the DDoS attacks enabler emerging in almost real-time.

This article continues the series of articles on load tests. Today we will analyze the testing methodology and answer the question: "How many IP cameras can be connected to a WebRTC server?"

Do you remember how just a few years ago it was a disaster to lose a camera at the end of a vacation? All memorable pictures and videos then disappeared along with the lost device. Probably, this fact prompted the great minds to invent cloud storage, so that the safety of records no longer depends on the presence of the devices on which these records are made.

We continue to review variants of load tests. In this article we will go over the testing methodology and conduct a load test that we will use to try and determine the number of users that could watch and stream at the same time, meaning the users will simultaneously publish and view the streams.

This article is a continuation of our series of write-ups about load tests for our server. We have already discussed how to compile metrics and how to use them to choose the equipment, and we also provided an overview of various load testing methods. Today we shall look at how the server handles stream mixing.
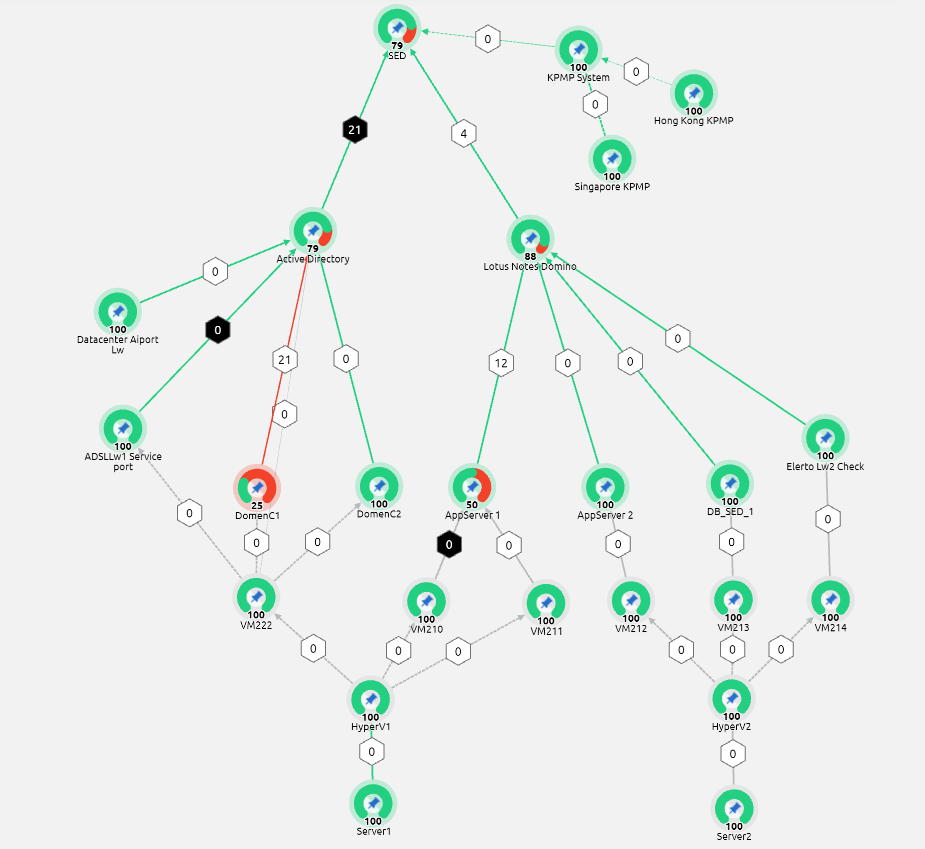

In the previous article we went over a load test whose data could be used to choose a load-appropriate server. In the course of the testing, we would publish a stream on one WCS, and we would pick up that stream several times using a second WCS. The acquired results could be used as a basis for decisions on server operability.
Some would (justly) have concerns regarding the possible biases in such a test — after all, one of our servers was used to test another one of our servers. Could it be that we were using a specially optimized code that skewed the results in our favor?
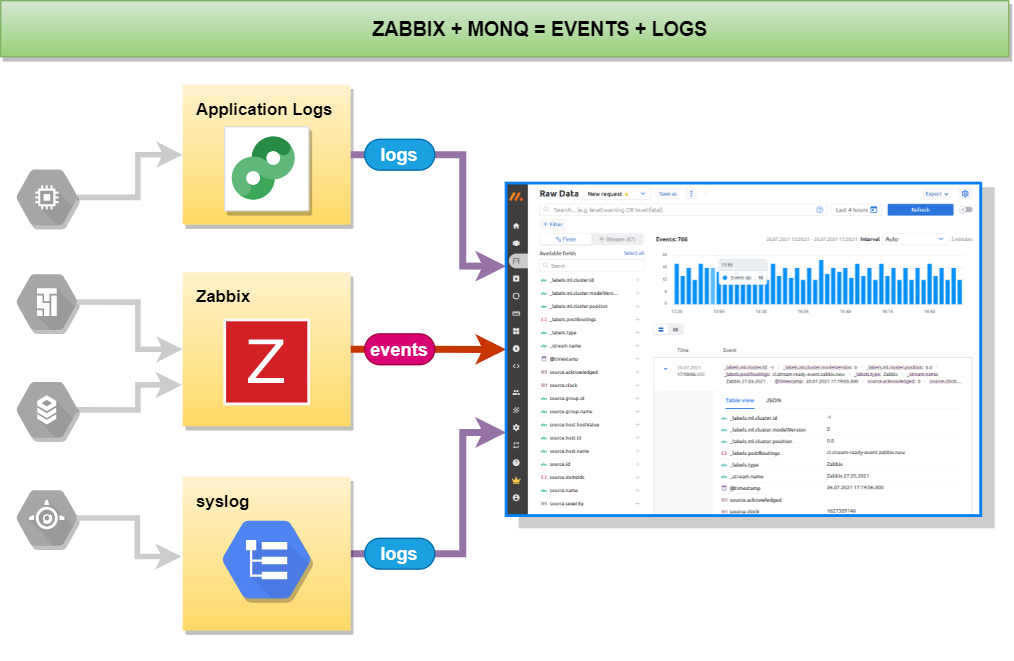
If you use Zabbix to monitor your infrastructure objects but have not previously thought about collecting and storing logs from these objects then this article is for you.

In any project, a great deal of importance is placed on the selection of server hardware and WebRTC streaming is no exception. One of the key principles of such a selection is balance – the hardware should be powerful enough to handle the streams with no drops in quality, but not too powerful so as to waste resources. So, how does one choose the right server?

Monitoring systems are a vital tool for any system administrator, because they can be used to extract specific information from services, such that:

This article is aimed to describe FreeBSD OS as a platform to launch cloud guest OSes with simple API capabilities, using MyBee and DevOPS I really like!