The search for a suitable storage platform: GlusterFS vs. Ceph vs. Virtuozzo Storage
This article outlines the key features and differences of such software-defined storage (SDS) solutions as GlusterFS, Ceph, and Virtuozzo Storage. Its goal is to help you find a suitable storage platform.
Gluster
Let’s start with GlusterFS that is often used as storage for virtual environments in open-source-based hyper-converged products with SDS. It is also offered by Red Hat alongside Ceph.
GlusterFS employs a stack of translators, services that handle file distribution and other tasks. It also uses services like Brick that handle disks and Volume that handle pools of bricks. Next, the DHT (distributed hash table) service distributes files into groups based on hashes.
Note: We’ll skip the sharding service due to issues related to it, which are described in linked articles.
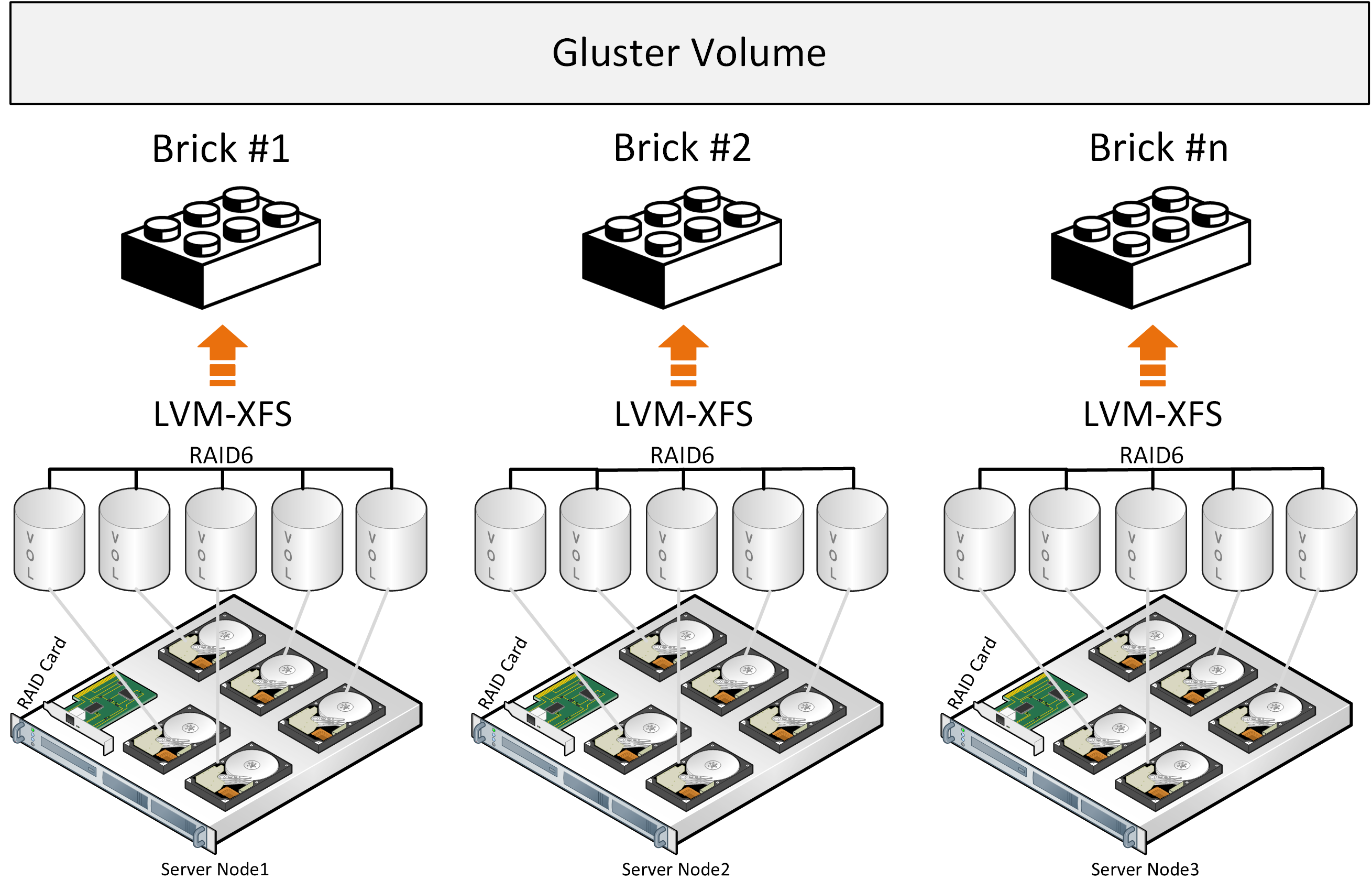
When a file is written onto GlusterFS storage, it is placed on a brick in one piece and copied to another brick on another server. The next file will be placed on two or more other bricks. This works well if the files are of about the same size and the volume consists of a single group of bricks. Otherwise the following issues may arise:



 Bangkok, in general, is a strange place to stay. Of course, it is warm there, rather cheap and some might find the cuisine interesting, along with the fact that about half of the world’s population
Bangkok, in general, is a strange place to stay. Of course, it is warm there, rather cheap and some might find the cuisine interesting, along with the fact that about half of the world’s population