New action to disrupt world’s largest online criminal network

Today, Microsoft and partners across 35 countries took coordinated legal and technical steps to disrupt one of the world’s most prolific botnets, called Necurs, which has infected more than nine million computers globally. This disruption is the result of eight years of tracking and planning and will help ensure the criminals behind this network are no longer able to use key elements of its infrastructure to execute cyberattacks.
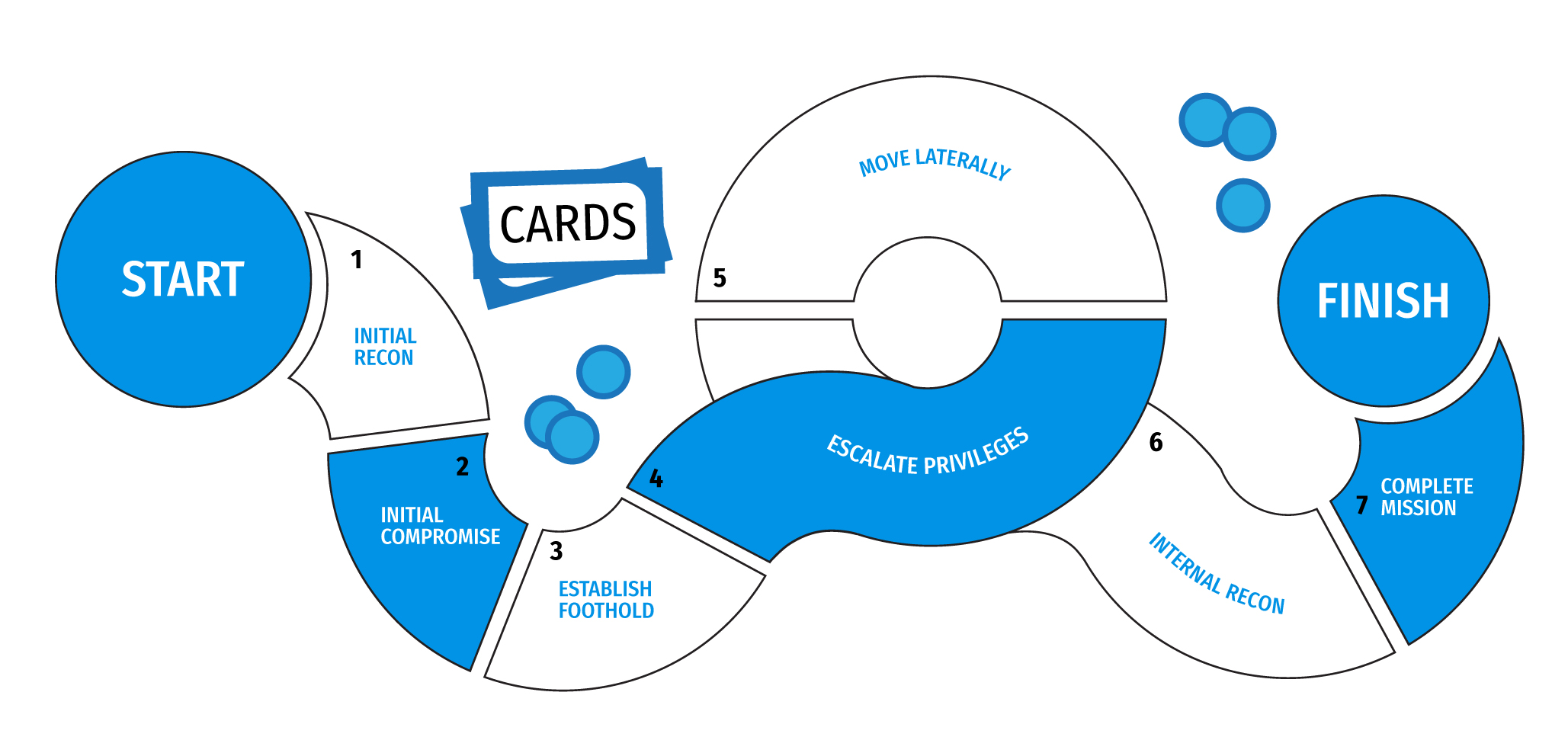
A botnet is a network of computers that a cybercriminal has infected with malicious software, or malware. Once infected, criminals can control those computers remotely and use them to commit crimes. Microsoft’s Digital Crimes Unit, BitSight and others in the security community first observed the Necurs botnet in 2012 and have seen it distribute several forms of malware, including the GameOver Zeus banking trojan.