TL;DR: starting February 2020, DNS servers that don’t support DNS both over UDP and TCP may stop working.
 Bangkok, in general, is a strange place to stay. Of course, it is warm there, rather cheap and some might find the cuisine interesting, along with the fact that about half of the world’s population does not need to apply for a visa in advance to get there. However, you still need to get acquainted with the smells, and the city streets are casting cyberpunk scenes more than anything else.
Bangkok, in general, is a strange place to stay. Of course, it is warm there, rather cheap and some might find the cuisine interesting, along with the fact that about half of the world’s population does not need to apply for a visa in advance to get there. However, you still need to get acquainted with the smells, and the city streets are casting cyberpunk scenes more than anything else.
In particular, a photo to the left has been taken not far from the center of Thailand’ capital city, one street away from the Shangri-La hotel, where the 30th DNS-OARC organization meeting took place on May 12 and 13. It is a non-profit organization dedicated to security, stability, and overall development of the DNS — the Domain Name System.
Slides from the DNS-OARC 30 meeting are recommended for everyone interested in how the DNS works, though perhaps the most interesting is what is absent in those slides. Namely, a 45-minute round table with a discussion around the results of DNS Flag Day 2019, which occurred on February, 1, 2019.
And, the most impressive result of a round table is the decision to repeat DNS Flag Day once again.
 As shown by various studies, DNS Flag Day negative effect was negligible. Probably for someone the adaptation process could be painful, but in the end, almost all outdated DNS servers were updated and incorrectly configured firewalls fixed.
As shown by various studies, DNS Flag Day negative effect was negligible. Probably for someone the adaptation process could be painful, but in the end, almost all outdated DNS servers were updated and incorrectly configured firewalls fixed.
Accordingly to such a course of action, the DNS Flag Day organizers perceive what has happened as a great victory and, inspired by the success, are not planning to stop.
At the round table, numerous tasks were discussed that the upcoming “flag days” could help accomplish:
Ultimately, there was made a decision presented then at the RIPE 78 meeting this week. Once again: starting February 2020, DNS servers that don’t support processing both UDP-based and TCP-based DNS queries may stop working.
 The exact day, however, has not yet been determined. Most likely it would be the February, 1, the year 2020, but the exact date is still subject to change a bit. Still, according to the organizers of the DNS Flag Day 2020 (almost the same organizations and individuals as in the first Flag Day), nine months are sufficient to ensure TCP support in existing DNS installations, leaving no sense to postpone the event.
The exact day, however, has not yet been determined. Most likely it would be the February, 1, the year 2020, but the exact date is still subject to change a bit. Still, according to the organizers of the DNS Flag Day 2020 (almost the same organizations and individuals as in the first Flag Day), nine months are sufficient to ensure TCP support in existing DNS installations, leaving no sense to postpone the event.
Today, DNS over TCP is, generally, supported on the Internet.
The Domain Name System operation over TCP is needed to handle several important cases:
 On the client (stub resolver) side, DNS over TCP has been supported for quite a long time already almost everywhere, including Windows.
On the client (stub resolver) side, DNS over TCP has been supported for quite a long time already almost everywhere, including Windows.
DNS over TCP has long been, in fact, mandatory. As Mark Andrews, the Bind DNS server developer, notes, RFC 1123 (published in 1989) allows to handle DNS queries and responses over UDP only if the server operator is well aware of the consequences and is able to maintain full functionality of the DNS protocol without TCP. Nowadays, the latter is basically impossible.
Analysis of 34 million domains out of 59 TLDs makes it evident that the requirement to use TCP leads to problems for approximately 7% of domains. To compare, in November 2018 — three months before the 2019 DNS Flag Day — 5.68% of tested sites still had EDNS issues.
Of those 7%:
Flag Day organizers have reached a consensus that thousands of ISPs and DNS operators which make up the DNS community should no longer pay for workarounds to benefit a couple dozen companies that are not updating their servers.
Moreover, critical point, just like last time, is that the consequences apply not only to DNS servers' owners, but to network administrators as well, if they block access to port 53/TCP on their firewalls.
By February 2020, access via port 53/TCP to DNS servers must work.

For sure, the Flag Day organizers would update their website and add DNS Flag Day 2020 information and tools to check any domains for compliance with the 2020 requirements.
Do not forget to carry out such a check before the end of this year, to make sure that you would have no issues.
The DNS Flag Day 2020 was discussed during the RIPE 78 meeting in Reykjavík, here are the slides, here's the video.
You can also follow what’s going on with Twitter.
DNS Flag Day 2021 will most likely be planned on a similar schedule, starting with the DNS-OARC 32 in the spring of the year 2020. Applications for workarounds and fixes, which should have been buried long ago, are accepted and collected on GitHub.
 Bangkok, in general, is a strange place to stay. Of course, it is warm there, rather cheap and some might find the cuisine interesting, along with the fact that about half of the world’s population does not need to apply for a visa in advance to get there. However, you still need to get acquainted with the smells, and the city streets are casting cyberpunk scenes more than anything else.
Bangkok, in general, is a strange place to stay. Of course, it is warm there, rather cheap and some might find the cuisine interesting, along with the fact that about half of the world’s population does not need to apply for a visa in advance to get there. However, you still need to get acquainted with the smells, and the city streets are casting cyberpunk scenes more than anything else.In particular, a photo to the left has been taken not far from the center of Thailand’ capital city, one street away from the Shangri-La hotel, where the 30th DNS-OARC organization meeting took place on May 12 and 13. It is a non-profit organization dedicated to security, stability, and overall development of the DNS — the Domain Name System.
Slides from the DNS-OARC 30 meeting are recommended for everyone interested in how the DNS works, though perhaps the most interesting is what is absent in those slides. Namely, a 45-minute round table with a discussion around the results of DNS Flag Day 2019, which occurred on February, 1, 2019.
And, the most impressive result of a round table is the decision to repeat DNS Flag Day once again.
Problems, officer?
 As shown by various studies, DNS Flag Day negative effect was negligible. Probably for someone the adaptation process could be painful, but in the end, almost all outdated DNS servers were updated and incorrectly configured firewalls fixed.
As shown by various studies, DNS Flag Day negative effect was negligible. Probably for someone the adaptation process could be painful, but in the end, almost all outdated DNS servers were updated and incorrectly configured firewalls fixed.Accordingly to such a course of action, the DNS Flag Day organizers perceive what has happened as a great victory and, inspired by the success, are not planning to stop.
At the round table, numerous tasks were discussed that the upcoming “flag days” could help accomplish:
- Support for EDNS version negotiation on public DNS servers;
- Support for RaNdOmIzAtIoN of capital and lowercase letters in DNS queries to increase entropy contained in the requests and responses;
- DNS over TCP support on DNS servers (both authoritative and recursive);
- Implementation of RFC 8020, which instructs recursive resolvers to stop quering a domain and all of its subdomains if they receive an NXDOMAIN-type response;
- IPv6 support etc.
Ultimately, there was made a decision presented then at the RIPE 78 meeting this week. Once again: starting February 2020, DNS servers that don’t support processing both UDP-based and TCP-based DNS queries may stop working.
 The exact day, however, has not yet been determined. Most likely it would be the February, 1, the year 2020, but the exact date is still subject to change a bit. Still, according to the organizers of the DNS Flag Day 2020 (almost the same organizations and individuals as in the first Flag Day), nine months are sufficient to ensure TCP support in existing DNS installations, leaving no sense to postpone the event.
The exact day, however, has not yet been determined. Most likely it would be the February, 1, the year 2020, but the exact date is still subject to change a bit. Still, according to the organizers of the DNS Flag Day 2020 (almost the same organizations and individuals as in the first Flag Day), nine months are sufficient to ensure TCP support in existing DNS installations, leaving no sense to postpone the event.Over TCP
Today, DNS over TCP is, generally, supported on the Internet.
The Domain Name System operation over TCP is needed to handle several important cases:
- Delivery of responses with sizes exceeding path MTU, without using generally unreliable IP fragmentation;
- DNSSEC support;
- Fighting DDoS attacks;
- Etc.
 On the client (stub resolver) side, DNS over TCP has been supported for quite a long time already almost everywhere, including Windows.
On the client (stub resolver) side, DNS over TCP has been supported for quite a long time already almost everywhere, including Windows.DNS over TCP has long been, in fact, mandatory. As Mark Andrews, the Bind DNS server developer, notes, RFC 1123 (published in 1989) allows to handle DNS queries and responses over UDP only if the server operator is well aware of the consequences and is able to maintain full functionality of the DNS protocol without TCP. Nowadays, the latter is basically impossible.
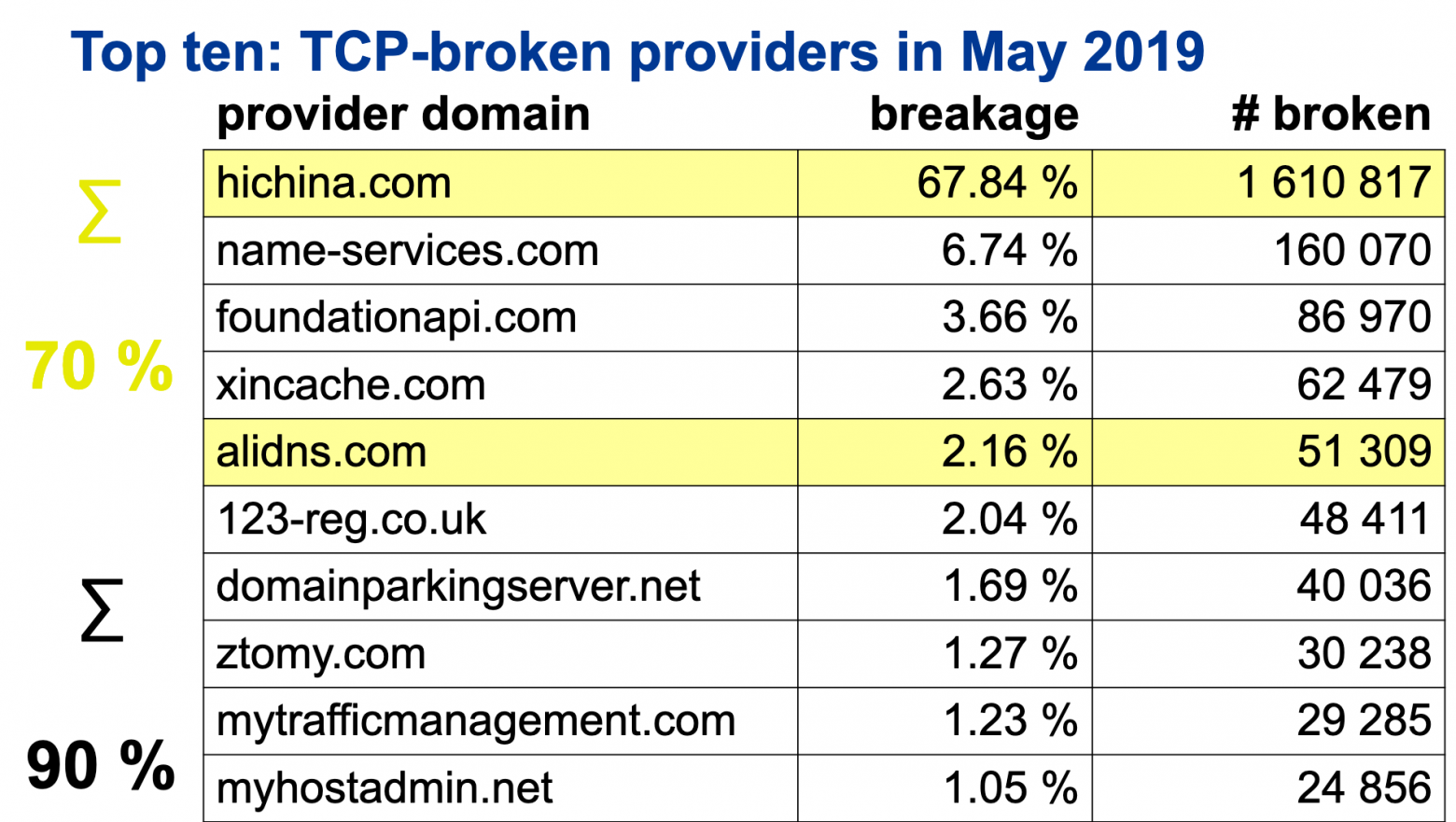
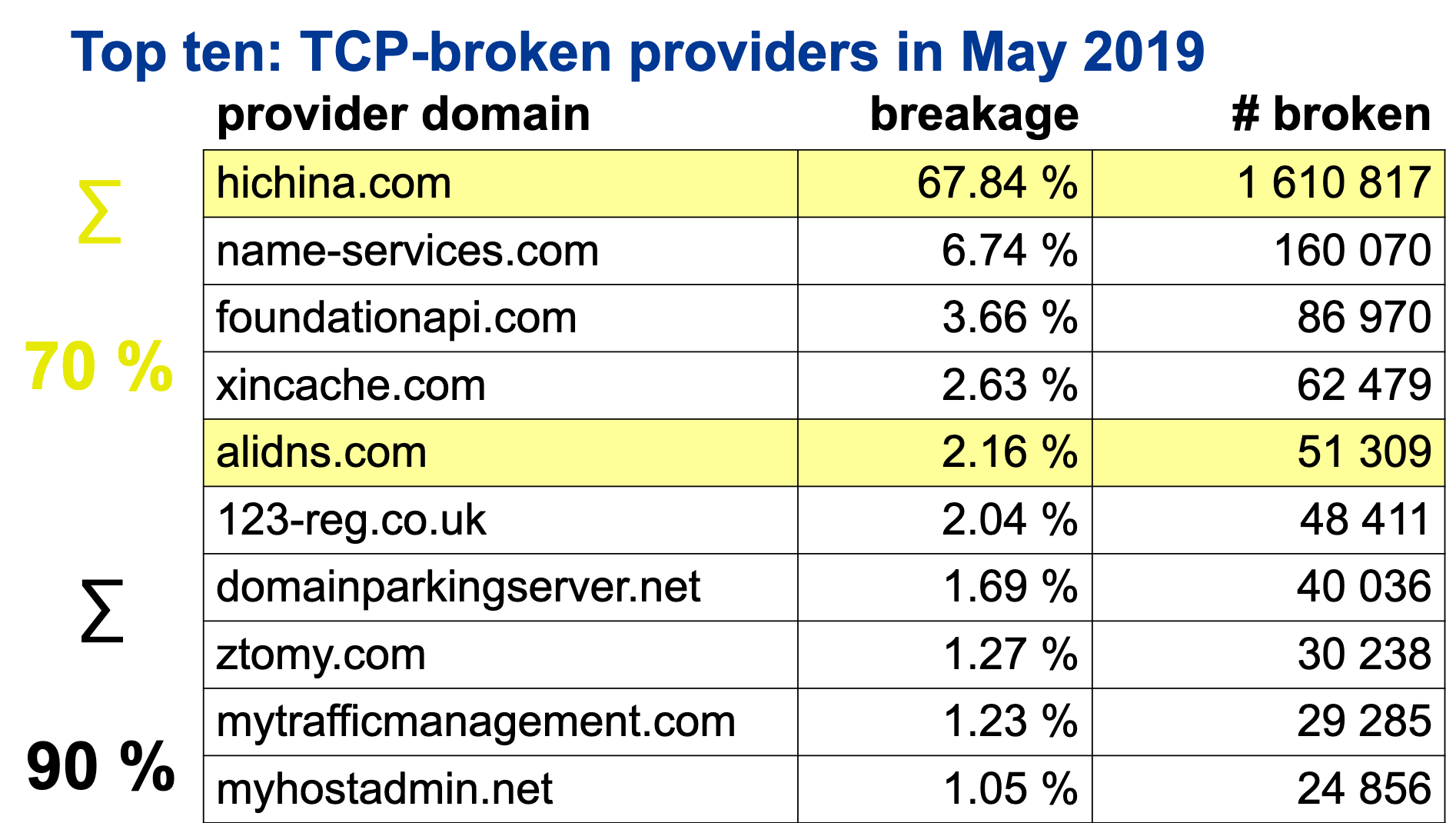
Analysis of 34 million domains out of 59 TLDs makes it evident that the requirement to use TCP leads to problems for approximately 7% of domains. To compare, in November 2018 — three months before the 2019 DNS Flag Day — 5.68% of tested sites still had EDNS issues.
Of those 7%:
- 90% of the issues are associated with the work of authoritative servers of 10 companies;
- 68% of the issue is locked on the servers of a single company — the Chinese ISP Hichina;
- Together with other Chinese providers — the AliDNS and Xinnet, this share rises to 72%;
- Half of the names on the list also had issues with EDNS in November 2018, though resolved them successfully just about the time.
Flag Day organizers have reached a consensus that thousands of ISPs and DNS operators which make up the DNS community should no longer pay for workarounds to benefit a couple dozen companies that are not updating their servers.
Moreover, critical point, just like last time, is that the consequences apply not only to DNS servers' owners, but to network administrators as well, if they block access to port 53/TCP on their firewalls.
By February 2020, access via port 53/TCP to DNS servers must work.

What's next?
For sure, the Flag Day organizers would update their website and add DNS Flag Day 2020 information and tools to check any domains for compliance with the 2020 requirements.
Do not forget to carry out such a check before the end of this year, to make sure that you would have no issues.
The DNS Flag Day 2020 was discussed during the RIPE 78 meeting in Reykjavík, here are the slides, here's the video.
You can also follow what’s going on with Twitter.
DNS Flag Day 2021 will most likely be planned on a similar schedule, starting with the DNS-OARC 32 in the spring of the year 2020. Applications for workarounds and fixes, which should have been buried long ago, are accepted and collected on GitHub.