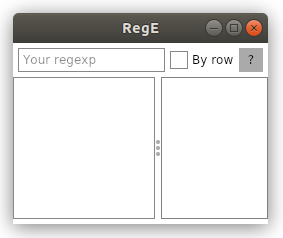
Regular Avalonia
In this article we will see how you can wrap Regex in cross-platform graphics and create a simple application for testing regular expressions.

In previous article we told a lot about security of ERP systems. Now we want to talk about ways to protect them.



Last week, Microsoft held its Build 2019 conference at the Washington State Convention Center in Seattle. Build is a large event with several thousand people from around the world attending to learn all about the current, newest, and future developer-oriented tech coming from Microsoft.
We had the pleasure of meeting so many of you at our booth and answering all your questions!

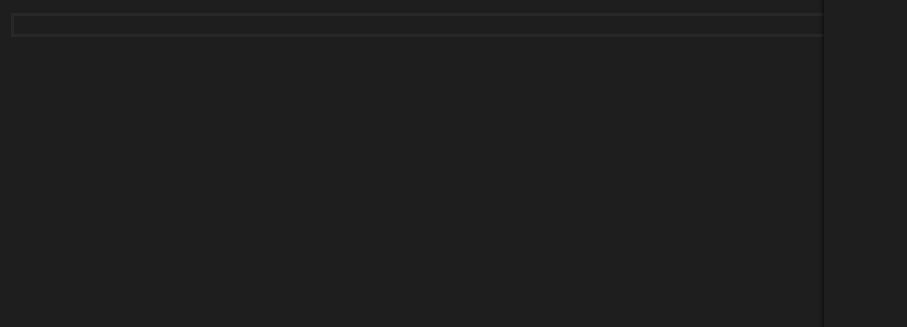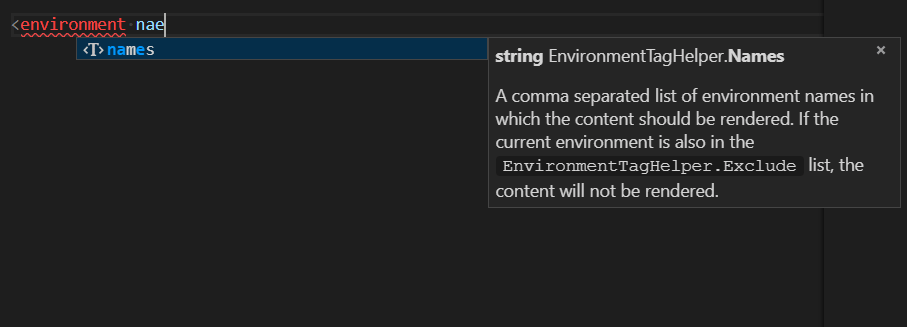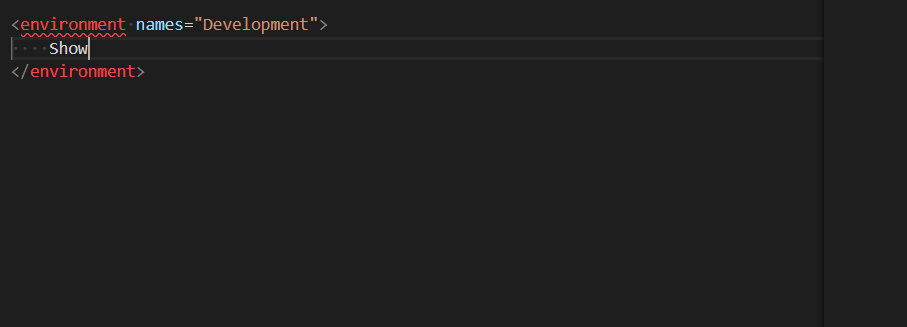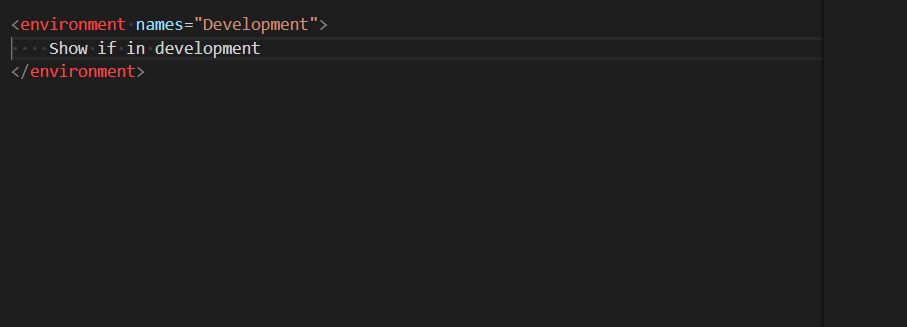
Some days ago we announced improved Razor tooling support in Visual Studio Code with the latest C# extension. This latest release includes improved Razor diagnostics and support for tag helpers and Blazor apps.
Earlier this week, we released Visual Studio 2019 version 16.1 Preview 1 (see release notes). It’s the first preview of the first update to Visual Studio 2019. If you’re not already set up to get preview releases, then please do that now. The preview channel installs side-by-side with the release channel and they don’t interfere with each other. I highly recommend all extension authors install the preview.
Got the 16.1 preview installed now then? That’s great. Here are some features in it you might find interesting.
If you use Habr, chances are, you’re conscious about privacy on the web. As governments and corporations tighten their grip on people’s online activities, the issue of keeping your browsing data to yourself becomes more and more relevant.
Numerous tech websites say VPN is no longer a geek-only thing, and regular people should use it, too (Fast Company, Mashable, PCMag). But as a tech-savvy person, you know there isn’t a service you can trust as much as the one you host and manage yourself.
With this post, you’ll deploy your own instance of Outline VPN on AWS.




 Now user visits the page and checks out the effect. It’s cool and pleasant small feature, it catches, then user discusses it with colleagues or friends and even repeats the feature. It could be this easy, if not:
Now user visits the page and checks out the effect. It’s cool and pleasant small feature, it catches, then user discusses it with colleagues or friends and even repeats the feature. It could be this easy, if not: 
 A few months ago I worked with a customer on how a team should evaluate the security of their Azure implementation. I had never done a pentest(extensive security testing)on an Azure application before, so these ideas were just the thoughts off of the top of my head at that time based on my experience in security.
A few months ago I worked with a customer on how a team should evaluate the security of their Azure implementation. I had never done a pentest(extensive security testing)on an Azure application before, so these ideas were just the thoughts off of the top of my head at that time based on my experience in security.Matt Burrough’s book, Pentesting Azure Applications, goes even deeper and it is a must-read for security experts focused in Cloud Computing, I’m reading it right now.
Below I share with you these pre-book thoughts, and will compare them in a future article with the ones I will learn — or confirm — after reading Matt's book.