Last time, we discussed
object-level locks and in particular relation-level locks. In this article, we will see how row-level locks are organized in PostgreSQL and how they are used together with object-level locks. We will also talk of wait queues and of those who jumps the queue.
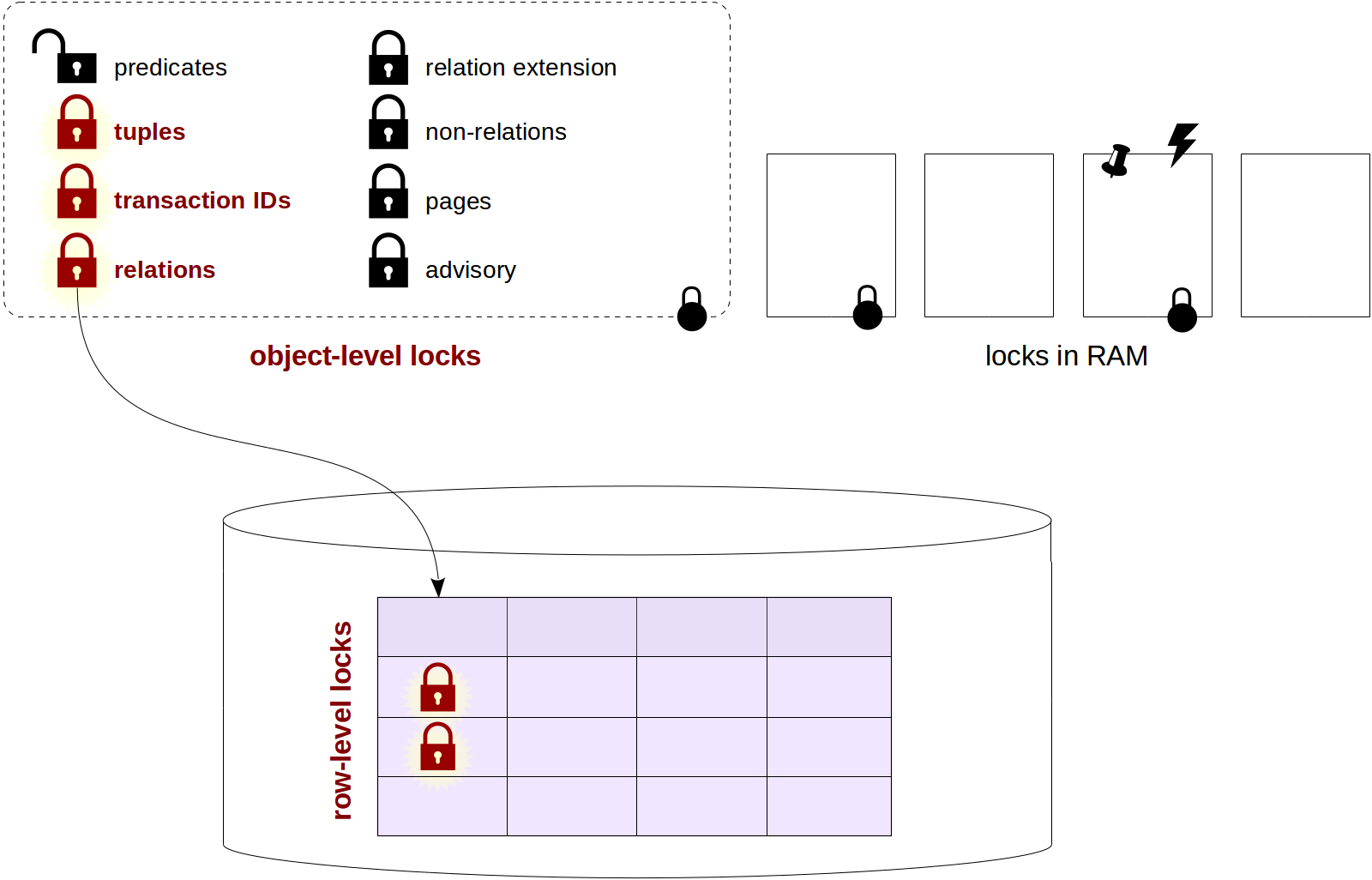
Row-level locks
Organization
Let's recall a few weighty conclusions of the previous article.
- A lock must be available somewhere in the shared memory of the server.
- The higher granularity of locks, the lower the contention among concurrent processes.
- On the other hand, the higher the granularity, the more of the memory is occupied by locks.
There is no doubt that we want a change of one row not block other rows of the same table. But we cannot afford to have its own lock for each row either.
There are different approaches to solving this problem. Some database management systems apply escalation of locks: if the number of row-level locks gets too high, they are replaced with one, more general lock (for example: a page-level or an entire table-level).
As we will see later, PostgreSQL also applies this technique, but only for predicate locks. The situation with row-level locks is different.