Modern applications have lots of code. And the C++ language doesn't get easier. Nowadays, code reviews are not enough to fully analyze program code. Here's where static code analysis comes in.

Information Security *
Data protection
Detecting errors in the LLVM release 13.0.0
Commercial static analyzers perform deeper and fuller code analysis compared to compilers. Let's see what PVS-Studio found in the source code of the LLVM 13.0.0 project.
CWE Top 25 2021. What is it, what is it for and how is it useful for static analysis?
For the first time PVS-Studio provided support for the CWE classification in the 6.21 release. It took place on January 15, 2018. Years have passed since then and we would like to tell you about the improvements related to the support of this classification in the latest analyzer version.

Insights Into Proactive Threat Hunting

Proactive search for complex threats seems to be a useful technology but inaccessible for many organizations. Is it really so? What do companies need to do to start Threat Hunting? What tools are needed for threat hunting? What trends in this area can be seen on the market in the coming years? These are some of the questions I would like to answer in my article today.
What is Threat Hunting?
Threat Hunting is a search for threats in a proactive mode when the information security specialist is sure that the network is compromised. He should understand how his network operates in order to be able to identify various attacks by examining the existing anomalies.
Threat Hunting is a search for threats that have already bypassed automated detection systems. Moreover, most often, you do not have signals or alerts that allow you to detect an intrusion.
From the SOC perspective, Threat Hunting is an extension of the service that allows you to counter any level of intruders, including those who use previously unknown tools and methods.
Threat Hunting can be based on some data obtained by a security specialist, or it can be based on a hypothesis. If after testing the hypothesis, the test gives a positive result, then later, it can be used to improve the processes and mechanisms of detecting threats. And also, Threat Hunting allows you to find blind spots in the security system and expand the monitoring area.
What organizations need Threat Hunting?
Proactive threat hunting is relevant to those organizations that can become the target of a complex, targeted APT attack. At the same time, given the trend towards supply chain attacks, a small company may also become a target for motivated attackers.
Mēris botnet, climbing to the record

Introduction
For the last five years, there have virtually been almost no global-scale application-layer attacks.
During this period, the industry has learned how to cope with the high bandwidth network layer attacks, including amplification-based ones. It does not mean that botnets are now harmless.
End of June 2021, Qrator Labs started to see signs of a new assaulting force on the Internet – a botnet of a new kind. That is a joint research we conducted together with Yandex to elaborate on the specifics of the DDoS attacks enabler emerging in almost real-time.
How Visual Studio 2022 ate up 100 GB of memory and what XML bombs had to do with it
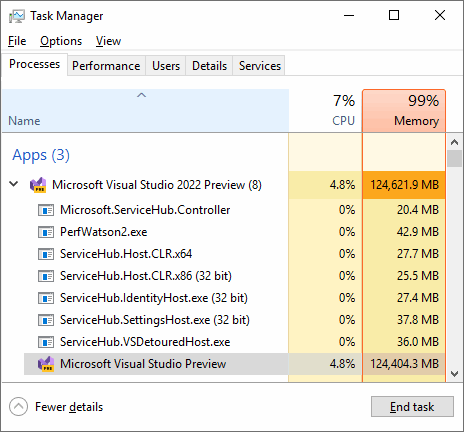
In April 2021 Microsoft announced a new version of its IDE – Visual Studio 2022 – while also announcing that the IDE would be 64-bit. We've been waiting for this for so long – no more 4 GB memory limitations! However, as it turned out, it's not all that simple...
Why do you need the MISRA Compliance report and how to generate one in PVS-Studio?

If you are strongly interested in MISRA and would like to understand whether your project meets one of the MISRA association's standards, there is a solution. It's name is MISRA Compliance. PVS-Studio has recently learned how to generate the MISRA Compliance report. This article describes how you can use this feature. This can make somebody's life better.
Easy Two Factor Authentication (2FA) with Google Authenticator

With this API implementing two factor authentication (2FA) is easier than ever. Just in 5 minutes I’ll guide you how to generate and validate time-based one-time passwords (TOTP) for second factor authentication (2FA) in fast and secure manner.
XSS: attack, defense — and C# programming

XSS - or cross-site scripting - is one of the most common vulnerabilities in web applications. It has been on the OWASP Top 10 list (the list of the most critical security risks to web applications) for a while now. So let's figure out together how your browser can acquire and execute a script from a third-party website, and what this may lead to (spoiler: your cookies could get stolen, for example). And while we're at it, we'll talk about ways you can protect yourself from XSS.
Private party protocol: how to distinguish friends and foes using cryptographic tools

ENCRY presents a new interactive identification protocol aimed at controlling the access of selected users to various resources.
Close your eyes and imagine Nice, a luxurious estate whose extravagant owner throws epic parties with jazz and fireworks every weekend.
To attend such a party is a lot of the elite. Invitations are sent out in advance, and guests do not know the names of other invited persons. The owner of the estate, the mysterious Jay Gatsby, an eager luxury-lover, values privacy so much that he is not ready to entrust the list of invitees to anyone, not even his buttress. Moreover, the owner of the estate would like the guests not to reveal their names when entering the property. After all, there may be the mayor of the city, or the chief prosecutor among them, and they would like to keep their visit secret. Unfortunately, the owner of the estate himself is so busy that he cannot independently check each guest at the entrance, especially since there are several access roads to his house. How could he solve this problem?
Building an Arduino based RFID Emulator
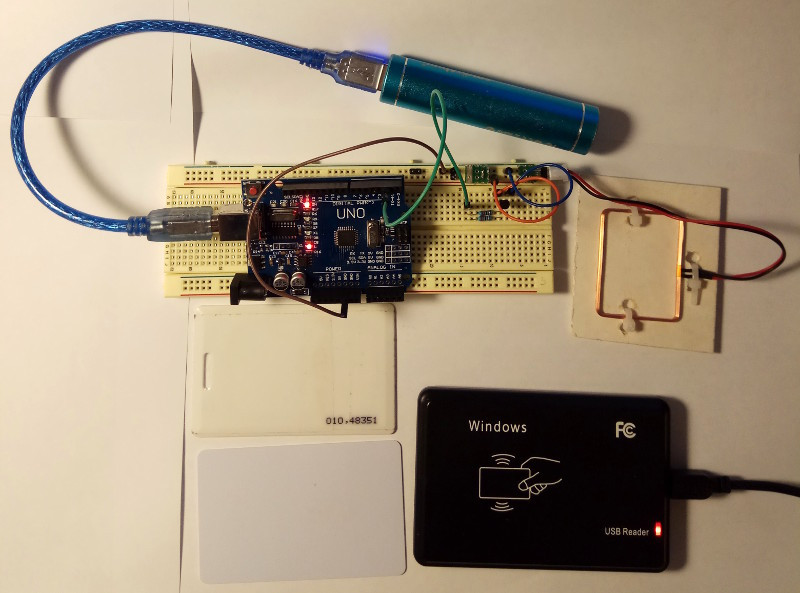
This project is aimed at creating an experimental device for emulating RFID labels of three widely available components. I simplified the explanation of the process so that it could be easily replicated. I also developed some helpful ideas along the way, including writing a special program for converting a serial number into the transmitted data, which will definitely prove useful.
OWASP, Vulnerabilities, and Taint Analysis in PVS-Studio for C#. Stir, but Don't Shake

We continue to develop PVS-Studio as a SAST solution. Thus, one of our major goals is expanding OWASP coverage. You might ask, what's the use when there's no taint analysis? That's exactly what we thought — and decided to implement taint analysis in the C# analyzer. Curious about what we accomplished? Read on!
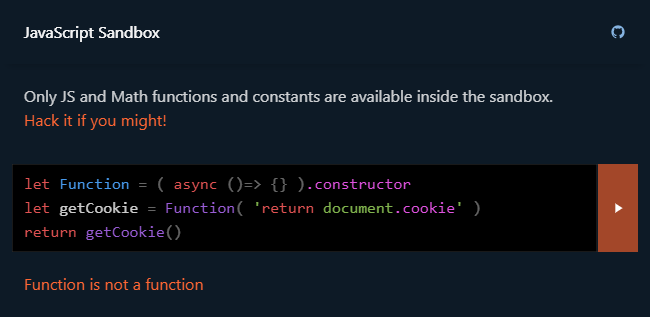
$mol_func_sandbox: hack me if you might!.
Hello, I'm Jin, and I… want to play a game with you. Its rules are very simple, but breaking them… will lead you to victory. Feel like a hacker getting out of the JavaScript sandbox in order to read cookies, mine bitcoins, make a deface, or something else interesting.
And then I'll tell you how the sandbox works and give you some ideas for hacking.
Q1 2021 DDoS attacks and BGP incidents

The year 2021 started on such a high note for Qrator Labs: on January 19, our company celebrated its 10th anniversary. Shortly after, in February, our network mitigated quite an impressive 750 Gbps DDoS attack based on old and well known DNS amplification. Furthermore, there is a constant flow of BGP incidents; some are becoming global routing anomalies. We started reporting in our newly made Twitter account for Qrator.Radar.
Nevertheless, with the first quarter of the year being over, we can take a closer look at DDoS attacks statistics and BGP incidents for January - March 2021.
PVS-Studio Learns What strlen is All About

Somehow, it so happens that we write about our diagnostics, but barely touch upon the subject of how we enhance the analyzer's internal mechanics. So, for a change, today we'll talk about a new useful upgrade for our data flow analysis.
Qrator Labs' Value Partnership Programs

Why is it valuable to get into the Qrator Labs partnership program?
In Qrator Labs, we firmly believe that working together brings a better result. Which is the reason why, for years, we were trying to find meaningful partnerships with all kinds of companies. They either seek to provide their existing customers with the top-notch DDoS mitigation technology developed at Qrator Labs with many additional ecosystem solutions or want to succeed the other way around. By getting their product available for Qrator Labs' customers by integrating into the Qrator anycast filtering network.
GDB Tutorial for Reverse Engineers: Breakpoints, Modifying Memory and Printing its Contents

GDB is THE debugger for Linux programs. It’s super powerful. But its user-friendliness or lack thereof can actually make you throw your PC out of the window. But what’s important to understand about GDB is that GDB is not simply a tool, it’s a debugging framework for you to build upon. In this article, I’m gonna walk you through GDB setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow.
How to Start Reverse Engineering in 2021
Reverse engineering might seem so complex, that not everyone has the bravery required to tackle it. But is it really that hard? Today we are gonna dive into the process of learning how to reverse engineer.
First of all, try to answer yourself, what are you hoping to achieve with reverse engineering? Because reverse engineering is a tool. And you should choose the right tool for your task. So when reverse engineering might be useful?
2020 Network Security and Availability Report

By the beginning of 2021, Qrator Labs filtering network expands to 14 scrubbing centers and a total of 3 Tbps filtering bandwidth capacity, with the San Paolo scrubbing facility fully operational in early 2021;
New partner services fully integrated into Qrator Labs infrastructure and customer dashboard throughout 2020: SolidWall WAF and RuGeeks CDN;
Upgraded filtering logic allows Qrator Labs to serve even bigger infrastructures with full-scale cybersecurity protection and DDoS attacks mitigation;
The newest AMD processors are now widely used by Qrator Labs in packet processing.
DDoS attacks were on the rise during 2020, with the most relentless attacks described as short and overwhelmingly intensive.
However, BGP incidents were an area where it was evident that some change was and still is needed, as there was a significant amount of devastating hijacks and route leaks.
In 2020, we began providing our services in Singapore under a new partnership and opened a new scrubbing center in Dubai, where our fully functioning branch is staffed by the best professionals to serve local customers.
Example of How New Diagnostics Appear in PVS-Studio
Users sometimes ask how new diagnostics appear in the PVS-Studio static analyzer. We answer that we draw inspiration from a variety of sources: books, coding standards, our own mistakes, our users' emails, and others. Recently we came up with an interesting idea of a new diagnostic. Today we decided to tell the story of how it happened.
Authors' contribution
alizar 21560.3ptsecurity 10358.7marks 9200.7GlobalSign_admin 6284.9LukaSafonov 6213.4ValdikSS 5478.6Kaspersky_Lab 5352.9ru_vds 3411.4esetnod32 3275.0zhovner 2947.0