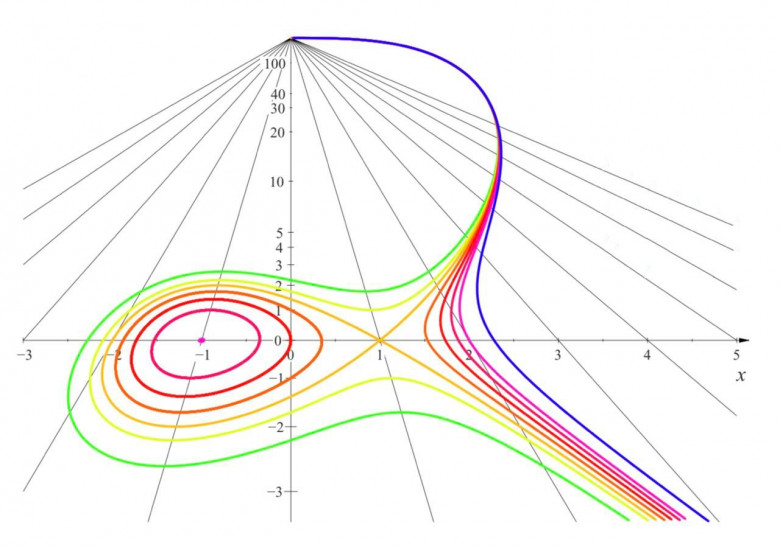
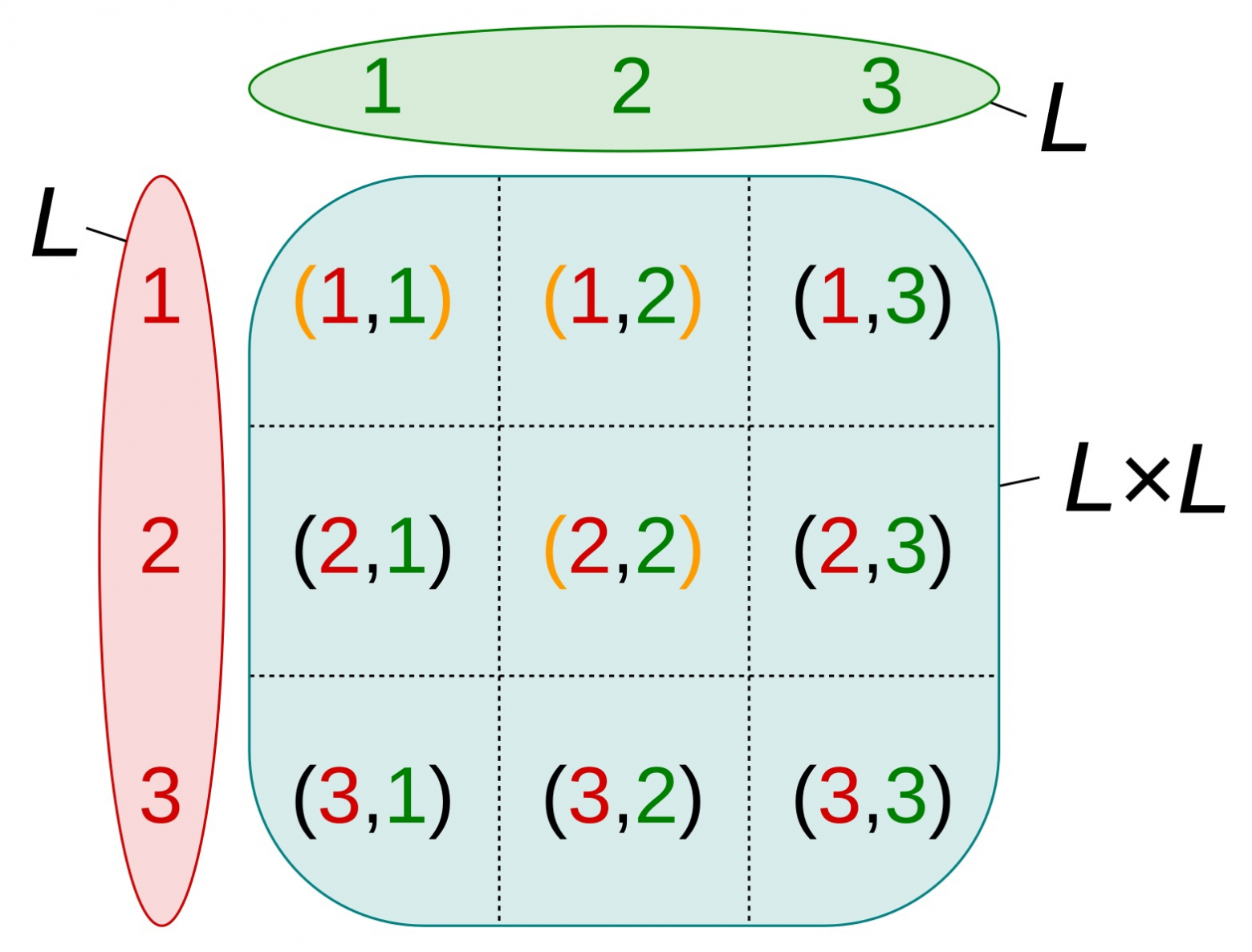
Notes on the Forgotten Nature of Zen Koans
I don’t know how koans were perceived when they sounded like thunder. Perhaps not at all as they are analyzed by modern philosophers. Perhaps koans were not analyzed, but lived. And it is impossible to transmit a lived experience across centuries. It is an individual experience. Well then, perhaps we have lost the essence of koans. Or perhaps we never knew it. In that case, I can very well allow myself to present koans as I see them.