The most common OAuth 2.0 Hacks
OAuth 2 overview
This article assumes that readers are familiar with OAuth 2. However, below a brief description of it is presented below.
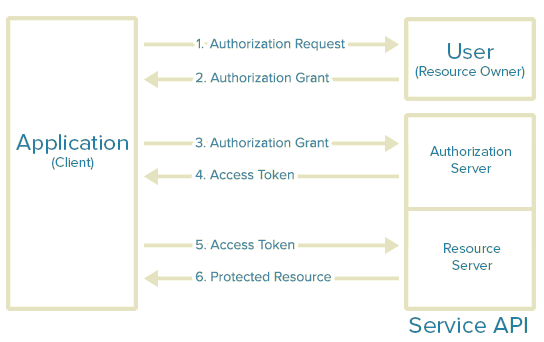
- The application requests authorization to access service resources from the user. The application needs to provide the client ID, client secret, redirect URI and the required scopes.
- If the user authorizes the request, the application receives an authorization grant
- The application requests an access token from the authorization server by presenting authentication of its own identity, and the authorization grant
- If the application identity is authenticated and the authorization grant is valid, the authorization server issues the access and refresh (if required) token to the application. Authorization is complete.
- The application requests the resource from the resource server and presents the access token for authentication
- If the access token is valid, the resource server serves the resource to the application
The are some main Pros and Cons in OAuth 2.0
- OAuth 2.0 is easier to use and implement (compared to OAuth 1.0)
- Wide spread and continuing growing
- Short lived Tokens
- Encapsulated Tokens
— No signature (relies solely on SSL/TLS ), Bearer Tokens
— No built-in security
— Can be dangerous if used from not experienced people
— Too many compromises. Working group did not make clear decisions
— Mobile integration (web views)
— Oauth 2.0 spec is not a protocol, it is rather a framework — RFC 6749
 Sometimes people ask the question, which addresses a certain topic but is actually about another thing. As the saying goes, a competently asked question contains half the answer.
Sometimes people ask the question, which addresses a certain topic but is actually about another thing. As the saying goes, a competently asked question contains half the answer.