Notifications: action required for take profit / stop loss. In case your Broker doesn't support those orders
update:2019-03-22, the Broker published platform 3.0.0 (a major update) in Google Play. The changelog features take profit/stop loss orders

Why do so many programmers hate UI work? Because it is tedious. Especially, for the Web, but other types of UI are only slightly easier. Layouts, margins, paddings — neverending stream of little tweaks to make it look OK on all sane environments, and somehow this freaking button sometimes overlaps that input field. Rrrr! And yes, it should not hang on button clicks, which means a lot of asynchronous programming, which is a nightmare.
And don’t even speak about aesthetics and usability! Choose right colours, element sizes and locations, find/draw images and put them where they fit, think about user workflows — isn’t it a designers’ or Ux specialists’ job?! Leave me alone, I’m a programmer. I work with backend layers, where everything is straightforward and linear, there are no buttloads of different environments to adjust to, and design is guided by mere logic without pesky fussing with ‘user friendliness’ and ’beauty’!

41 TB/day from Oracle to Postgres Pro without stopping the source system — not theory, but numbers from our latest tests. We broke the migration into three stages: fast initial load, CDC from redo logs, and validation, and wrapped them into ProGate. In this article, we’ll explain how the pipeline works, why we chose Go, and where the bottlenecks hide.

Why does even the most powerful LLM sometimes produce meaningless phrases and contradictions? It all comes down to the exponential growth of possibilities (N^M) and the free copying of human errors. Read the article to learn how we use formal grammars to turn chaotic generation into controlled synthesis, strengthening the role of semantics and enforcing structural rules.

We append the following metrics to the T-SQL procedure statements: execution count (x), CPU time in milliseconds (c), duration in microseconds (d), number of reads (r), number of writes (w), and @@rowcount value (n). You can display these as absolute values or percentages.

Hi to everyone!
I'm new here. Someone told me that Habr is like russian reddit for developers (and maybe not). And I'm here today to share my story and get opinions from you, part of this community.
In August 2024 I visited Moscow, and got Russian starter pack, even if foregneir :-)
Will be useful later because I'm moving here, Русский язык coming soon, извините!
So let's start with getting a new bank account, make a new mobile number and start to register to some essential service platforms like Metro, Gorod, ВВ, Perekrostak and Yandex for delivery and taxis. And in every service I found something strange. A certain "Ivan" (I've changed the name for privacy) is present in all my accounts where I try to register.
That's it! The phone number that my bank gave me was just.... recyled! So I could start to get personal data through all these existing account on this new phone number of mine but the most shocking thing occured today!
Alarm on 9:00, I woke up and I got a message by Yandex:

If your code has many nested executions of stored procedures, you can benefit from building popular "flame diagram" of the execution time which is de facto standard for performance profiling.

Postgres Pro Enterprise 17 introduces major improvements in performance and scalability. The key feature of this new release is the proxima extension, which combines connection pooling, proxying, and load balancing within the database core. Developers also gain improved tools for managing message queues, optimizing queries, enhancing security, and utilizing smart data storage. Want to know how these and other features can impact your applications and simplify database administration?
This article provides a brief overview of the release, accompanied by the links to more detailed information.

In the world of blockchain, where the word "gas" is most often associated not with gas stations, but with fees for transactions in Ethereum, the search for ways to minimize these costs is becoming increasingly relevant. Less heartache for an empty wallet and more time to solve really important issues... for example, what to cook for lunch =)
Similar to the epic Batman vs Superman battle, compare GSN and Account Abstraction. As in any superhero story, each of them has its own unique abilities and disadvantages, which we will look at in detail.

Wilhelm Röntgen discovered X-ray November 8th 1895, when he did experiments with cathode rays in a vacuum tube. To capture and save images of the shadows from the X-rays, he used ordinary photoplates. Fortunately, sensitive to visible light silver based photoemulsions turned out to be sensitive to the X-ray too. These photoplates became the first X-ray detectors.
More than 100 years of scientific progress led to the creation of a number of various detectors for recording X-ray images. Developments of the microelectronics and semiconductor manufacturing technologies are crucial for development of the modern X-ray detectors. These detectors can transform the energy of the X-ray photon directly to the electrical signal. They allow capturing detailed, digital, high-resolution X-ray images.
Digital images are easy to work with. For example one can merge multiple macro images into an image of the whole object and represent monochrome images in false colors like Simon Procz did with this X-ray image of a flower he did in 2012.

Hey! My name's Kirill Ziborov and I'm a member of the Distributed System Security team at Positive Technologies. In this article, I'll be continuing the discussion of methods and tools for the formal verification of smart contracts and their practical application to prevent vulnerabilities. The main focus will be on the deductive verification method, or more precisely, the ConCert framework for testing and verifying smart contracts.
Secret Management and Why It’s Important
Hi! My name is Evgeny, and I work as a Lead DevOps at Exante. In this article, I will discuss the practical experience of setting up a high-availability HashiCorp Vault with a GCP storage backend and auto unseal in Kubernetes (K8s).
Our infrastructure used to consist of thousands of virtual and physical machines hosting our legacy services. Configuration files, including plain-text secrets, were distributed across these machines, both manually and with the help of Chef.
We decided to change the company’s strategy for several reasons: to accelerate code delivery processes, ensure continuous delivery, securely store secrets, and speed up the deployment of new applications and environments.
We decided to transition our product to a cloud-native model, which required us to change our approach to development and infrastructure. This involved refactoring our legacy services, adopting a microservices architecture, deploying services in cloud-based Kubernetes (K8s), and utilizing managed resources like Redis and PostgreSQL.
In our situation, everything needed to change—from applications and infrastructure to how we distribute configs and secrets. We chose Google as our cloud provider and HashiCorp Vault for secret storage. We've since made significant progress on this journey.
Why HashiCorp Vault?
There were several reasons:

Riverpod is a powerful library that I like to think of as the Swiss Army knife of Flutter development. It offers elegant solutions for both state management and dependency injection, giving you the freedom to "cook" your app architecture just the way you like it.

It's been a while since my last appearance, but I'm excited to be back and to share something truly special with you. In this article, we'll explore my top 10 Google Sheets features that are guaranteed to boost your productivity, speed up your workflow, and make your data handling more efficient. So, without further ado, let's dive into these game-changing tools!
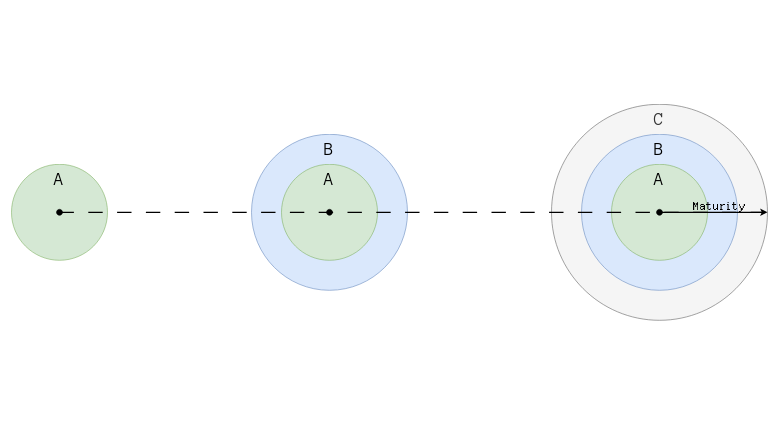
Modern product development demands more and more sophisticated designs. This in turn leads to the increased complexity of both demand and implementation. Business is flooding the architecture and development teams with the new and changed requirements. Development teams are struggling to understand what the business demand is and find the best product increment strategy. One of the widely adopted conversational methods is the Use-Cases. This guide is intended to shed light on the process of the requirements development and maturing.
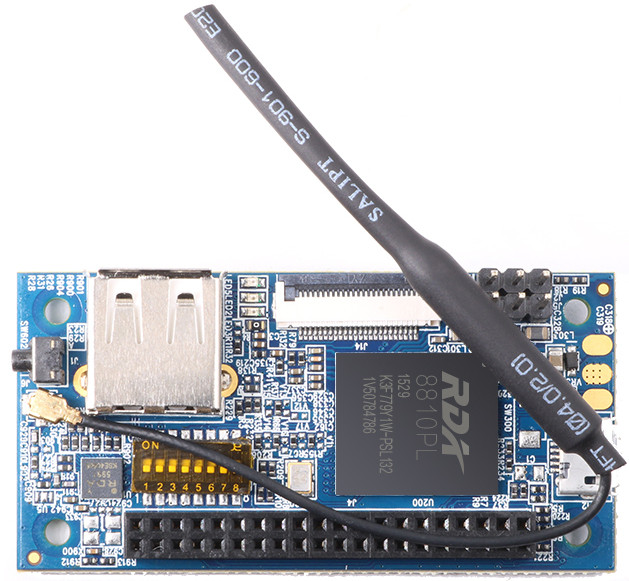
Hellow my name is Dmitry. Once I bought "Orange PI i96", but unfortunately producer not update it firmvere very long. Last firmwere kernel version is 3.10.62 but kernel current at time this article writing (russian version) is 6.5.1. And so I decide build my own firmware from scratch, and do it from sourse completely.

In today's rapidly advancing technological landscape, natural language processing and comprehension have become essential components of everyday life. Leading the charge in this arena is OpenAI's ChatGPT API, renowned for its exceptional ability to understand and interact with human language. Imagine elevating ChatGPT's functionality to new heights, enabling it to carry out specific tasks based on commands given in natural language. This article aims to shed light on the potential of incorporating function calling into the ChatGPT API, thereby enhancing its utility. I will illustrate through practical examples how such extensions can unlock a myriad of opportunities and applications.

The meetup on January 14 at Hacker Dojo in Mountain View, California, went well, although not as planned - we spent almost all the time talking instead of doing hands-on exercises. The room we booked can fit 30 people and approximately 30 people did show up. The quality of participants was high: approximately half were familiar with hardware description languages and another half came from various software topics. 12 people filled out the questionnaire despite the fact that I forgot to bring 30 pens.
The discussion during and after the presentation was focused and very meaningful: microarchitecture and education, EDA infrastructure / build scripts, open-source ASIC design tools, the economics of ASIC design and manufacturing, high-level synthesis, transaction-level modeling, ASIC prototyping using FPGA boards, FPGA embedded in ASIC (Menta), new FPGA manufacturers (Gowin) and new design languages - Chisel and SpinalHDL.
Four persons came to me after the meeting to discuss their participation in working on open-source portable SystemVerilog examples, and another seven expressed this intention in the questionnaire. So we are meeting again in Hacker Dojo on Sunday, January 21, at 2 PM, this time not in the classroom area, but in the common shared area.
Generally, I am thinking of having regular meetings, probably on a weekly basis for a small team of developers of the educational materials and on a monthly basis for a wider audience, discussing various design and verification topics.
There were two correspondents of Slavic Sacramento who recorded the video of the presentation. They are going to make it available soon.
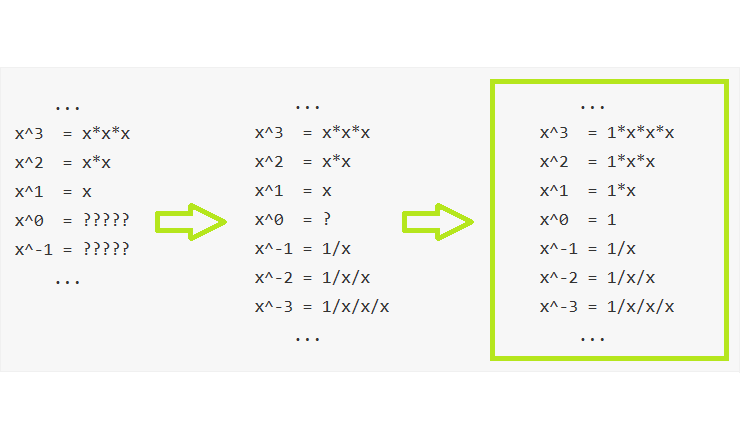
The traditional definition for the operation of exponentiation to a natural power (or a positive integer) had introduced approximately as follows:
Exponentiation is an arithmetic operation originally defined as the result of multiple multiplications a number by itself.
But the more precise formulation is still different:
Raising a number X to an integer power N is an arithmetic operation defined as the result of multiple [N by mod times] multiplications or divisions one by number X.