Frontend Weekly Digest (4 – 10 Mar 2019)



Google and Facebook are the computerized behemoths who dependably contend. Their answers for designers Angular and React appear matches as well. Demand helps look at both. The article was initially posted here
Toward the start of its advancement, SPA web stages did not have an adaptable however basic framework for making the ventures that could revise and, now and again, supplant both portable and work area applications. Around then, a client whose issue was very basic needed to discover an application equipped for tackling the issue. Over the span of time, the advancements continued pushing ahead making web administrations gain ubiquity since the last had no should be introduced. What was required is simply to visit a site for getting to some administration. Already, such errands could be tackled through sites written in either ActionScript or Java. Nonetheless, those frameworks required to introduce either Flash or Java being in the meantime a long way from the speed expected by the clients.@Angular
By then, JavaScript advanced adequately to desert its adversaries because of a fast, improvement straightforwardness, and ceaseless help of the programs' engineers. The period of JavaScript began inciting such definition as SPA (Single Page Application) which gave another way to deal with the advancement of web stages. Not at all like its precursor MPA (Multi-Page Application), SPA permitted a web administration to work a lot quicker just as to give it an increasingly refined usefulness fit for changing progressively as per clients' needs. The greatest disadvantage was in unadulterated JavaScript which couldn't give a quick improvement when even a crude SPA web administration required a ton of time to be made. That is the reason Google chosen to help the methodology with a system that could enable different organizations to create muddled web administrations without investing a lot of energy for it.
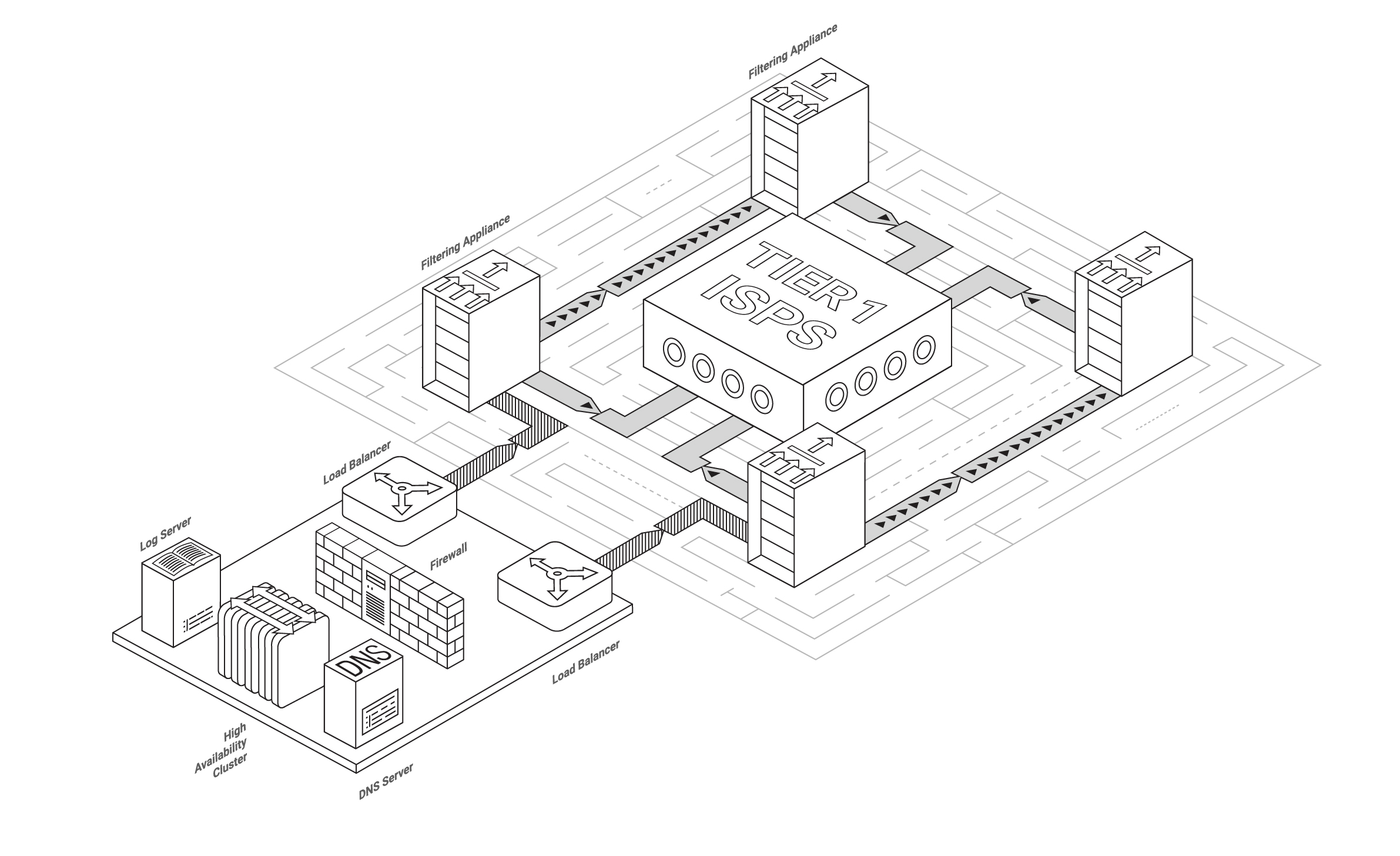
Some time ago among security researchers, it was very “fashionable” to find improperly configured AWS cloud storages with various kinds of confidential information. At that time, I even published a small note about how Amazon S3 open cloud storage is discovered.
However, time passes and the focus in research has shifted to the search for unsecured and exposed public domain databases. More than half of the known cases of large data leaks over the past year are leaks from open databases.

Today we will try to figure out how such databases are discovered by security researchers...


I made the “electric” designer of… cardboard. Alas, the project still remains at the prototype stage, not developing into an industrial “physical” look and is waiting for its time (and investor).
But I decided to go further — once we started making cardboard, we’ll bring the situation to its logical conclusion — we’ll make a complete cardboard board game, but with an electric setting and a learning effect. There were a lot of options — starting from a simple “walker” and ending with Ameritrash from a zombie with electron movement and vicious short circuits and swollen capacitors.
As a result, I decided to dwell on a logical abstract, since the schematics of electrical circuits are very suitable for it. Said and done — as a result of the first iteration, the game “Circuit” was born.


postgres=# select amname from pg_am;
amname
--------
btree
hash
gist
gin
spgist
brin
(6 rows)

Create your first intelligent bot with Microsoft AI
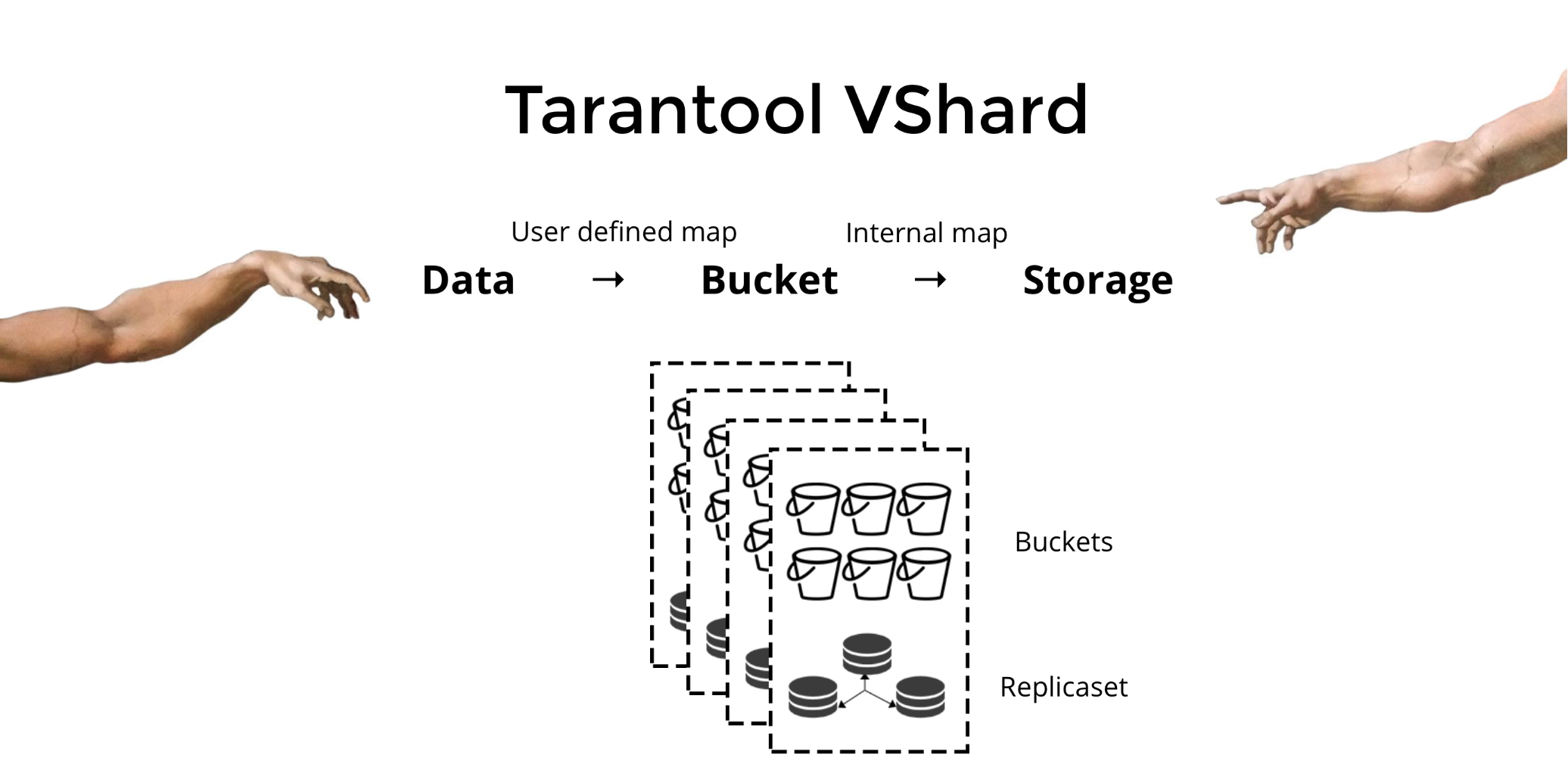
Artificial intelligence (AI) is accelerating the digital transformation for every industry, with examples spanning manufacturing, retail, finance, healthcare, and many others. At this rate, every industry will be able to use AI to amplify human ingenuity. In this e-book, Anand Raman and Wee Hyong Tok from Microsoft provide a comprehensive roadmap for developers to build their first AI-infused application.
Using a Conference Buddy as an example, you’ll learn the key ingredients needed to develop an intelligent chatbot that helps conference participants interact with speakers. This e-book provides a gentle introduction to the tools, infrastructure, and services on the Microsoft AI Platform, and teaches you how to create powerful, intelligent applications.

If someone of you has tried create angular libraries, he may face the issue with lazy loading Feature Module from node_modules. Let's dive deeper and go thru the dark water.

Discovering git vendor extension.
Cross-post from my medium blog: https://medium.com/opsops/git-vendor-295db4bcec3a
I would like to introduce the proper way to handle vendoring of git repositories.
Vendoring is a way to integrate other’s work into your own. It’s the opposite of ‘linking’ against third-party library. Instead of having that library as a dependency, application uses this library as a part of own source code and keep that code ‘inside’ itself.
Normally, vendoring is done by language tooling: bundler, cargo, pip, etc. But sometimes you need to vendor something not covered by any existing toolset, or something multi-language, that it’s impossible to find the ‘core’ language tool for that.
The solution for this situation is vendoring on a git level. You have your own git repository (I call it ‘destination repo’), and you want to incorporate some other repository (I call it ‘source repo’) as a directory into your (destination repo).
The things you expect from a well-designed vendoring system (regardless of Git it is or not):