I'm seeking anyone who is skilled enough to develop a simple Python script using TDLib, Telegram API, and JSON manipulation to make it possible to perform simple tasks listed below:
1. Import Telegram chat JSON backup back to Telegram similar to what these scripts are doing github.com/alexlyzhov/telegram-import
github.com/Suberbia/UltimateChatRestorer
github.com/mygrexit/UltimateChatRestorerForGroupchats
but for any chat (not only to «saved messages») including group chats (not only 1 to 1 chats) and improve the code to make it work faster, more reliable, write log file, allow continuing from the stop point in case of errors and keep all the original chat data including formatting and everything that telegram can handle.
Some kinda combine all the script in one universal, flexible, high quality tool.
The most important aspect of the whole task is that the imported messages have to keep not only the formatting, but its original date and time when they were actually sent. Like it is done in the original telegram tool for importing history from some other apps — telegram.org/blog/move-history
2. Make it very simple to use. Perfect solution will be: Download, put the script next to JSON backup and run it in the interactive mode or with some specific options. Let the script ask for all the credentials and briefly explain where to get them. If possible, keep all the job on one device with no need of transferring the WA format zip file to the phone for importing. If not possible, make it an android app which will get the JSON, process it and feed the result to the Telegram app for import.
This is the basic I'm going to pay for.








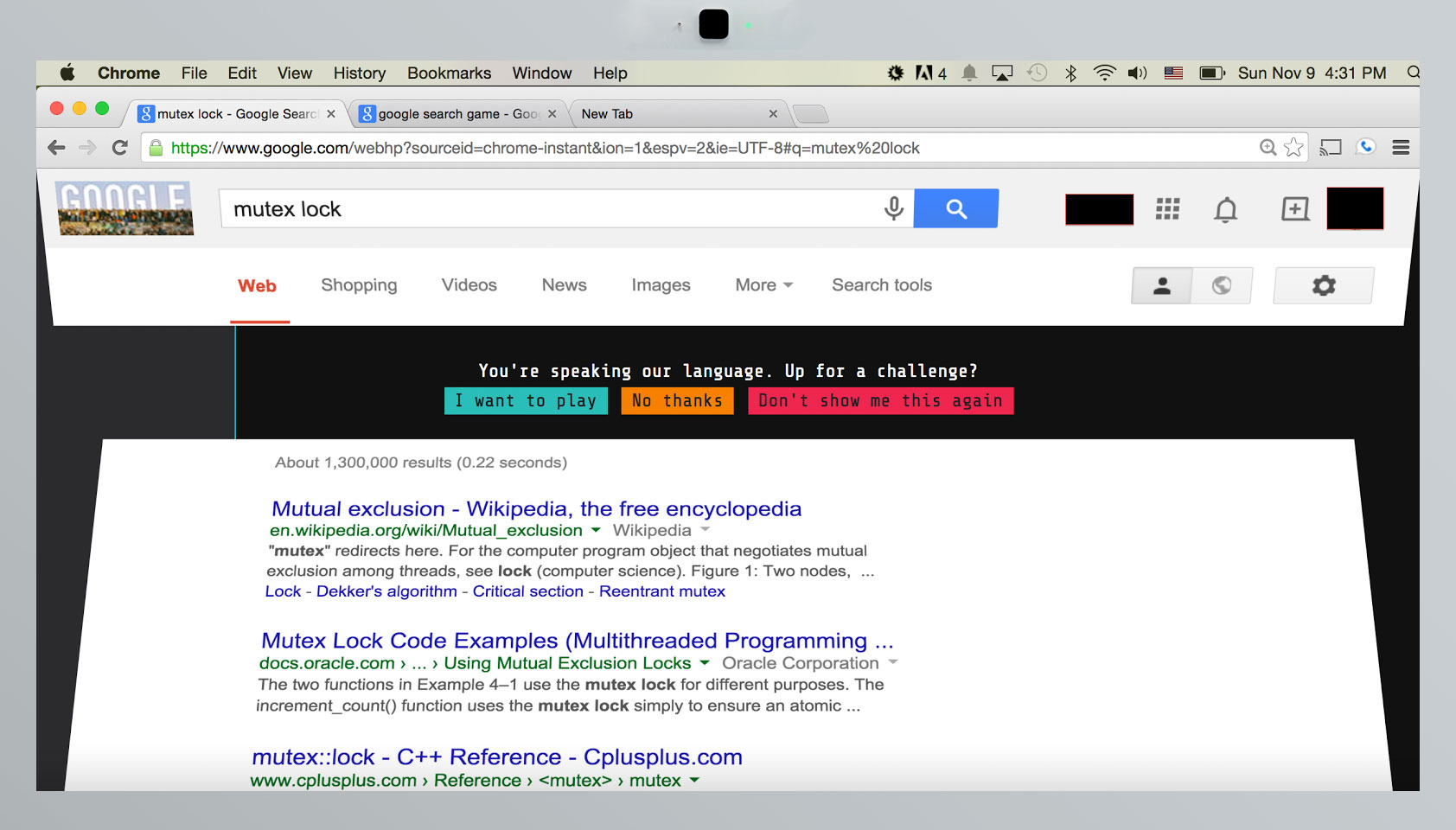
 Google loves easter eggs. It loves them so much, in fact, that you could find them in virtually every product of theirs. The tradition of Android easter eggs began in the very earliest versions of the OS (I think everyone there knows what happens when you go into the general settings and tap the version number a few times).
Google loves easter eggs. It loves them so much, in fact, that you could find them in virtually every product of theirs. The tradition of Android easter eggs began in the very earliest versions of the OS (I think everyone there knows what happens when you go into the general settings and tap the version number a few times).