In today's fast-paced world of software development, integrating third-party APIs and services is a common practice. These integrations can enhance functionality, improve user experience, and provide additional features that would be time-consuming and costly to develop in-house. However, ensuring these integrations work seamlessly with your software is crucial, and this is where the importance of a test environment, or sandbox, comes into play.
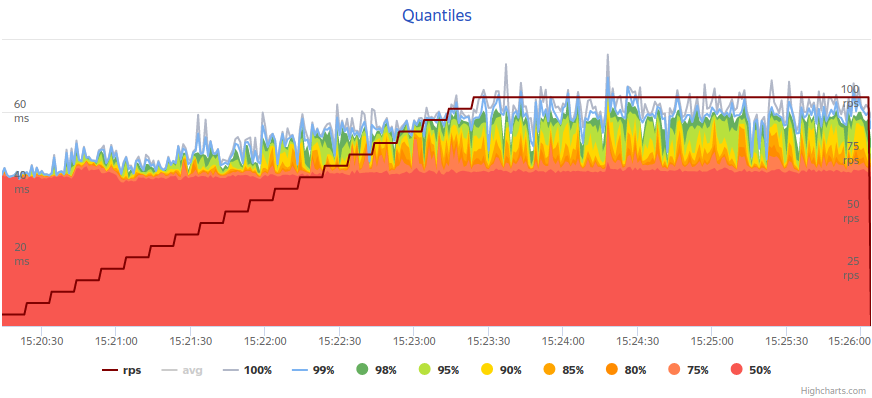
A sandbox environment allows developers to test the integration between their software and third-party services without risking the stability and security of the production environment. This controlled setting enables thorough testing, helping to uncover issues before they affect end-users. By covering as many test cases as possible, developers can ensure robust and reliable integrations.
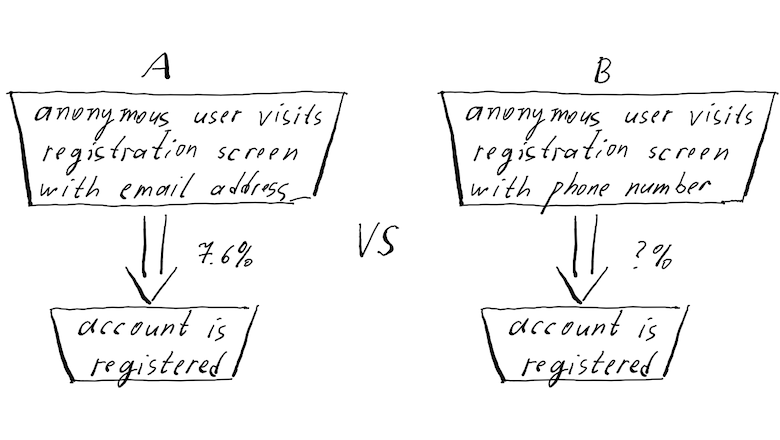
But what if your third-party provider, such as a bank or government e-system, does not offer a sandbox environment? This scenario can pose significant challenges, but there are several strategies you can employ to mitigate these issues.