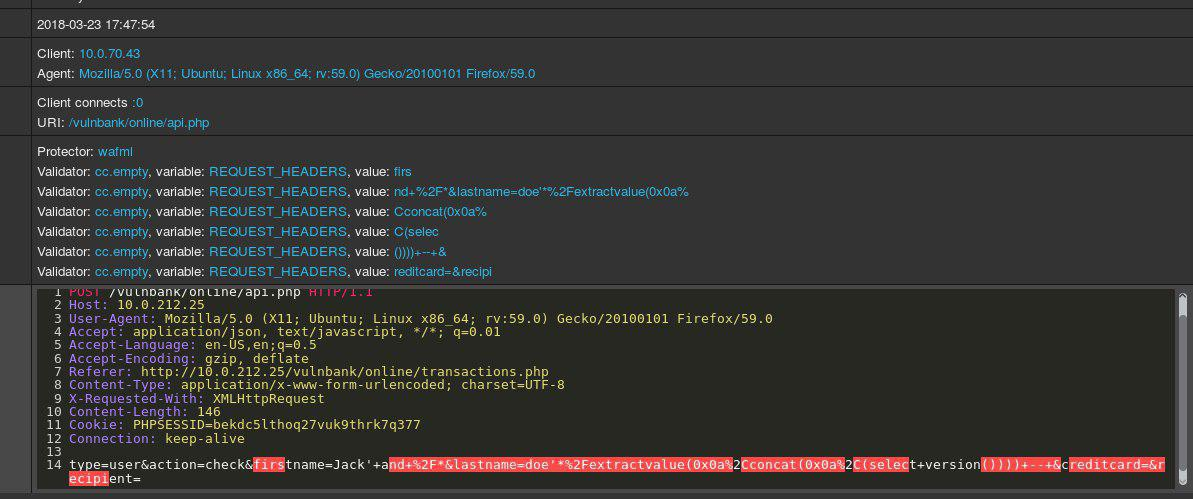
BGP perforating wound
Those routes were taken from the transit provider RETN (AS9002) and further announced to NTEC’s provider — RU-telecom’s AS205540, which, in its turn, accepted all of them, spreading the leak.


Data protection




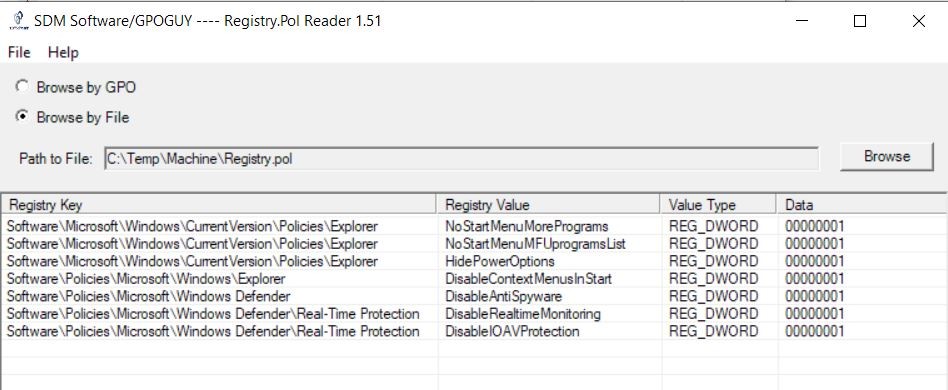
A completely routine tech support ticket has uncovered unexpected bans of IP addresses of Protonmail — a very useful service for people valuing their Internet freedoms — in several regions of Russia. I seriously didn’t want to sensationalize the headline, but the story is so strange and inexplicable I couldn’t resist.
Disclaimer: the situation is still developing. There might not be anything malicious, but most likely there is. I will update the post once new information comes through.
MTS and Rostelecom — two of the biggest Russian ISPs — started to block traffic to SMTP servers of the encrypted email service Protonmail according to an FSB request, with no regard for the official government registry of restricted websites. It seems like it’s been happening for a while, but no one paid special attention to it. Until now.
All involved parties have received relevant requests for information which they’re obligated to reply.
UPD: MTS has provided a scan of the FSB letter, which is the basis for restricting the access. Justification: the ongoing Universiade in Krasnoyarsk and “phone terrorism”. It’s supposed to prevent ProtonMail emails from going to emergency addresses of security services and schools.
UPD: Protonmail was surprised by “these strange Russians” and their methods for battling fraud abuse, as well as suggested a more effective way to do it — via abuse mailbox.
UPD: FSB’s justification doesn’t appear to be true: the bans broke ProtonMail’s incoming mail, rather than outgoing.
UPD: Protonmail shrugged and changed the IP addresses of their MXs taking them out of the blocking after that particular FSB letter. What will happen next is open ended question.
UPD: Apparently, such letter was not the only one and there is still a set of IP addresses of VOIP-services which are blocked without appropriate records in the official registry of restricted websites.

Some time ago among security researchers, it was very “fashionable” to find improperly configured AWS cloud storages with various kinds of confidential information. At that time, I even published a small note about how Amazon S3 open cloud storage is discovered.
However, time passes and the focus in research has shifted to the search for unsecured and exposed public domain databases. More than half of the known cases of large data leaks over the past year are leaks from open databases.

Today we will try to figure out how such databases are discovered by security researchers...
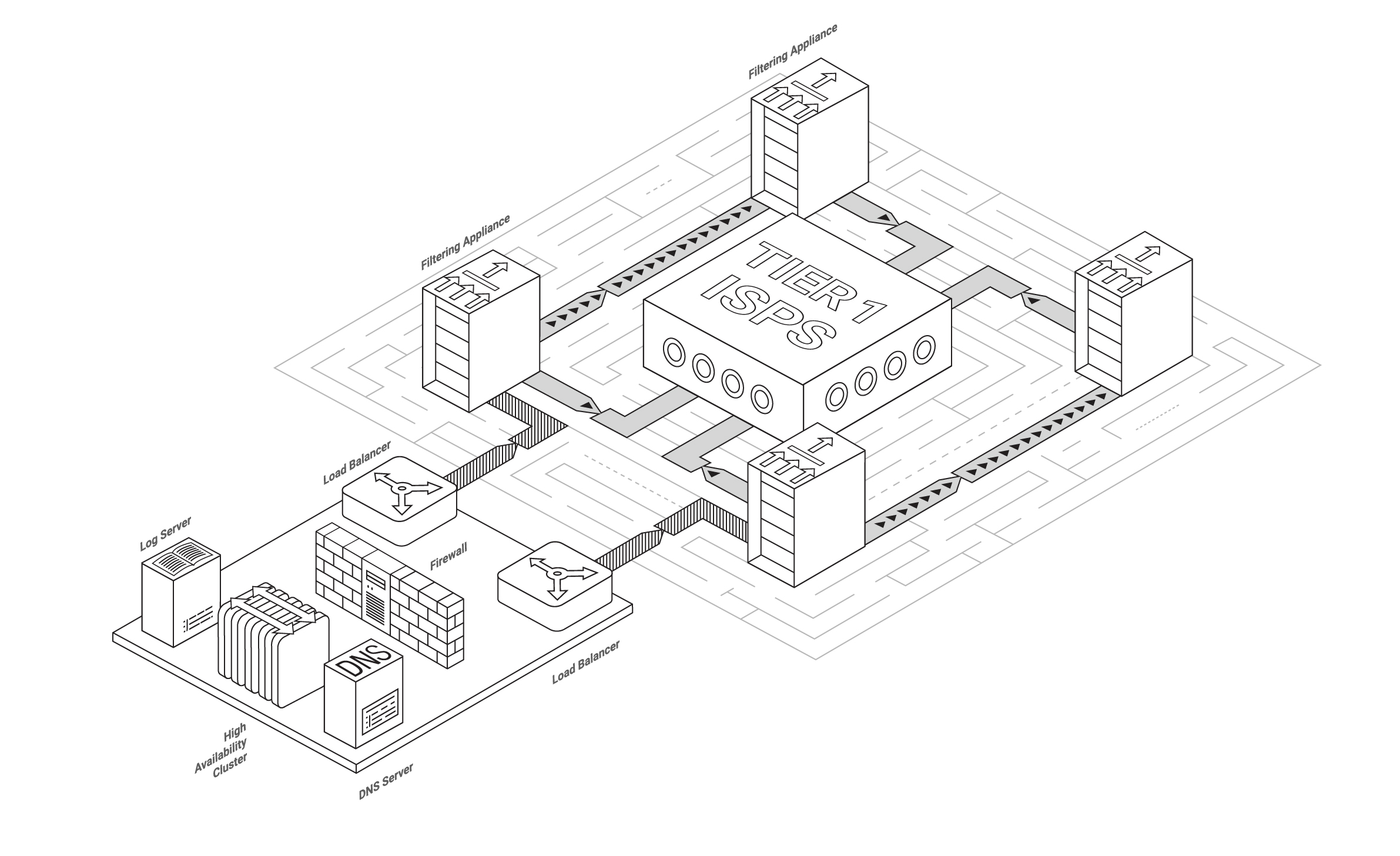
People are resorting to blockchain for all kinds of reasons these days. Ever since I started doing smart contract security audits in mid-2017, I’ve seen it all. A special category of cases is ‘blockchain use’ that seems logical and beneficial, but actually contains a problem that then spreads from one startup to another. I am going to give some examples of such problems and ineffective solutions so that you (developer/customer/investor) know what to do when somebody offers you to use blockchain this way.
Let’s say you ordered some goods, and a carrier guarantees to maintain certain transportation conditions, such as keeping your goods cold. A proposed solution is to install a sensor in a truck that will monitor fridge temperature and regularly transmit the data to the blockchain. This way, you can make sure that the promised conditions are met along the entire route.