What to think during NALSD interview
 So, what is the difference? How to be prepared for this interview? Let’s be non-abstract, and use an example. To be more non-abstract, let’s take something from the material world, such that you won’t be asked the exact same thing at the real interview (at least, not at the Google interview) :)
So, what is the difference? How to be prepared for this interview? Let’s be non-abstract, and use an example. To be more non-abstract, let’s take something from the material world, such that you won’t be asked the exact same thing at the real interview (at least, not at the Google interview) :)So, let’s design a public library system. For the paper books, like you have seen everywhere around. The whole text below was written all at once within around one hour, to roughly show you the areas that you should be able to cover / touch during the interview. Please excuse some disorder, that’s how I think (therefore I am).
Analysis of commits and pull requests in Travis CI, Buddy and AppVeyor using PVS-Studio
Starting from the version 7.04, the PVS-Studio analyzer for C and C++ languages on Linux and macOS provides the test feature of checking the list of specified files. Using the new mode, you can configure the analyzer to check commits and pull requests. This article covers setting up the check of certain modified files from a GitHub project in such popular CI (Continuous Integration) systems, as Travis CI, Buddy and AppVeyor.
Getting Started with the PVS-Studio Static Analyzer for C++ Development under Linux
 PVS-Studio supports analyzing projects developed in C, C++, C#, and Java. You can use the analyzer under Windows, Linux, and macOS. This small article will tell you the basics of analyzing C and C++ code in Linux environment.
PVS-Studio supports analyzing projects developed in C, C++, C#, and Java. You can use the analyzer under Windows, Linux, and macOS. This small article will tell you the basics of analyzing C and C++ code in Linux environment.Installation
There are different ways to install PVS-Studio under Linux, depending on your distro type. The most convenient and preferred method is to use the repository, since it allows auto-updating the analyzer upon releasing new versions. Another option is to use the installation package, which you can get here.
Long journey to Tox-rs. Part 1

Hi everyone!
I like Tox and respect the participants of this project and their work. In an effort to help Tox developers and users, I looked into the code and noticed potential problems that could lead to a false sense of security. Since I originally published this article in 2016 (in Russian), many improvements have been made to Tox, and I lead a team that re-wrote secure Tox software from scratch using the Rust programming language (check out Tox-rs). I DO recommend using tox in 2019. Let's take a look what actually made us rewrite Tox in Rust.
Original article of 2016
There is an unhealthy tendency to overestimate the security of E2E systems only on the basis that they are E2E. I will present objective facts supplemented with my own comments for you to draw your own conclusions.
Spoiler: The Tox developers agree with my points and my source code pull request was accepted.
TLS 1.3 enabled, and why you should do the same

As we wrote in the 2018-2019 Interconnected Networks Issues and Availability Report at the beginning of this year, TLS 1.3 arrival is inevitable. Some time ago we successfully deployed the 1.3 version of the Transport Layer Security protocol. After gathering and analyzing the data, we are now ready to highlight the most exciting parts of this transition.
As IETF TLS Working Group Chairs wrote in the article:
“In short, TLS 1.3 is poised to provide a foundation for a more secure and efficient Internet over the next 20 years and beyond.”
TLS 1.3 has arrived after 10 years of development. Qrator Labs, as well as the IT industry overall, watched the development process closely from the initial draft through each of the 28 versions while a balanced and manageable protocol was maturing that we are ready to support in 2019. The support is already evident among the market, and we want to keep pace in implementing this robust, proven security protocol.
Eric Rescorla, the lone author of TLS 1.3 and the Firefox CTO, told The Register that:
“It's a drop-in replacement for TLS 1.2, uses the same keys and certificates, and clients and servers can automatically negotiate TLS 1.3 when they both support it,” he said. “There's pretty good library support already, and Chrome and Firefox both have TLS 1.3 on by default.”
Generating multi-brand multi-platform icons with Sketch and a Node.js script — Part #2

This is the second part of a post about the creation of a pipeline that can take a Sketch file and export all the icons included in the file, in different formats, for different platforms, with the possibility of AB testing each icon.
You can read the first part of the post here.
The Sketch files, with all the icons collected, styled and properly named, were ready. Now it was time to start writing the code.
Suffice to say, the process was very much a trial and error: after the important initial code core, developed by my team lead Nikhil Verma (who set the script foundations), I went through an incremental process that required at least three phases of refactoring and quite a few revisions. For this reason, I won’t go into too much detail on how the script was developed, but rather focus on how the script works today, in its final shape.
Chronicle of Rambler Group and Nginx confrontation (updated on 23 Dec, 12 p.m.)

On December 12, it became known from Nginx's employee Twitter that the company's office was searched due to the criminal case under Article 146 of the Criminal Code of the Russian Federation 'Violation of Author's and Neighboring Rights'. The claim belong to Rambler Group was, although formally the complaintant is Lynwood Investments CY Ltd, to which the rights were transferred. The last-mentioned is related to the co-owner of Rambler Group, Alexander Mamut.
The point of the claim: Igor started working on Nginx as an employee of Rambler and only after the tool became popular he founded a separate company and attracted investments.
Here is how the events unfolded.
Bluetooth stack modifications to improve audio quality on headphones without AAC, aptX, or LDAC codecs
Some wireless headphone users note low sound quality and lack of high frequencies when using the standard Bluetooth SBC codec, which is supported by all headphones and other Bluetooth audio devices. A common recommendation to get better sound quality is to buy devices and headphones with aptX or LDAC codecs support. These codecs require licensing fees, that's why devices with them are more expensive.
It turns out that the low quality of SBC is caused by artificial limitations of all current Bluetooth stacks and headphones' configuration, and this limitation can be circumvented on any existing device with software modification only.
Monitoring System for Windows servers on pure SQL, and how I had secretly dragged it into the Production
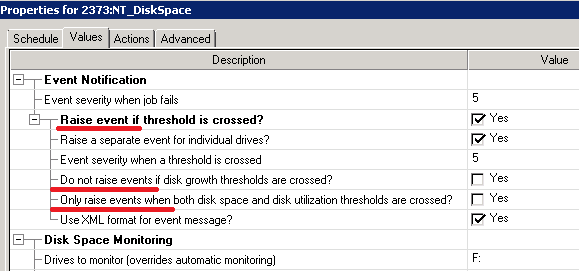
One of my new tasks was to support NetIQ. The person, who worked with NetIQ before, said a lot about his experience with NetIQ, unfortunately, if I try to put it here it would be just a long line of ‘****’ characters. Soon I realized why. Steve Jobs is probably spinning in his grave looking at the interface like this:
Writing yet another Kubernetes templating tool

If you are working with Kubernetes environment then you probably make use of several existing templating tools, some of them being a part of package managers such as Helm or Ksonnet, or just templating languages (Jinja2, Go template etc.). All of them have their own drawbacks as well as advantages and we are going to go through them and write our own tool that will try to combine the best features.
IIoT platform databases – How Mail.ru Cloud Solutions deals with petabytes of data coming from a multitude of devices

Hello, my name is Andrey Sergeyev and I work as a Head of IoT Solution Development at Mail.ru Cloud Solutions. We all know there is no such thing as a universal database. Especially when the task is to build an IoT platform that would be capable of processing millions of events from various sensors in near real-time.
Our product Mail.ru IoT Platform started as a Tarantool-based prototype. I’m going to tell you about our journey, the problems we faced and the solutions we found. I will also show you a current architecture for the modern Industrial Internet of Things platform. In this article we will look into:
- our requirements for the database, universal solutions, and the CAP theorem
- whether the database + application server in one approach is a silver bullet
- the evolution of the platform and the databases used in it
- the number of Tarantools we use and how we came to this
Checking rdesktop and xrdp with PVS-Studio

This is the second post in our series of articles about the results of checking open-source software working with the RDP protocol. Today we are going to take a look at the rdesktop client and xrdp server.
Bad news, everyone! New hijack attack in the wild
With this article, we want to show an example of the attack where not only the true attacker was under the question, but the whole list of affected prefixes. Moreover, it again raises concerns about the possible motives for the future attack of this type.
Understanding the POCSAG paging protocol

For people, who owned a pager before, and want to know how it works, this article will be useful.
11 Kubernetes implementation mistakes – and how to avoid them

I manage a team that designs and introduces in-house Kubernetes aaS at Mail.ru Cloud Solutions. And we often see a lack of understanding as to this technology, so I’d like to talk about common strategic mistakes at Kubernetes implementation in major projects.
Most of the problems arise because the technology is quite sophisticated. There are unobvious implementation and operation challenges, as well as poorly used advantages, all of those resulting in money loss. Another issue is the global lack of knowledge and experience with Kubernetes. Learning its use by the book can be tricky, and hiring qualified staff can be challenging. All the hype complicates Kubernetes-related decision making. Curiously enough, Kubernetes is often implemented rather formally – just for it to be there and make their lives better in some way.
Hopefully, this post will help you to make a decision you will feel proud of later (and won’t regret or feel like building a time machine to undo it).
Linux Switchdev the Mellanox way
This is a transcription of a talk that was presented at CSNOG 2020 — video is at the end of the page
Greetings! My name is Alexander Zubkov. I work at Qrator Labs, where we protect our customers against DDoS attacks and provide BGP analytics.
We started using Mellanox switches around 2 or 3 years ago. At the time we got acquainted with Switchdev in Linux and today I want to share with you our experience.
PVS-Studio in the Clouds — Running the Analysis on Travis CI

Practicalities of deploying dockerized ASP.NET Core application to Heroku
Intro
.NET is a relative newcomer in the open-source world, and its popularity is nowhere near mainstream platforms like Node.js. So you can imagine there're few tutorials that deal with .NET and frameworks such as ASP.NET on Heroku. And those that do, probably won't use containers.
Do you see C#/.NET here? Yes, me neither.
Eliminating opportunities for traffic hijacking
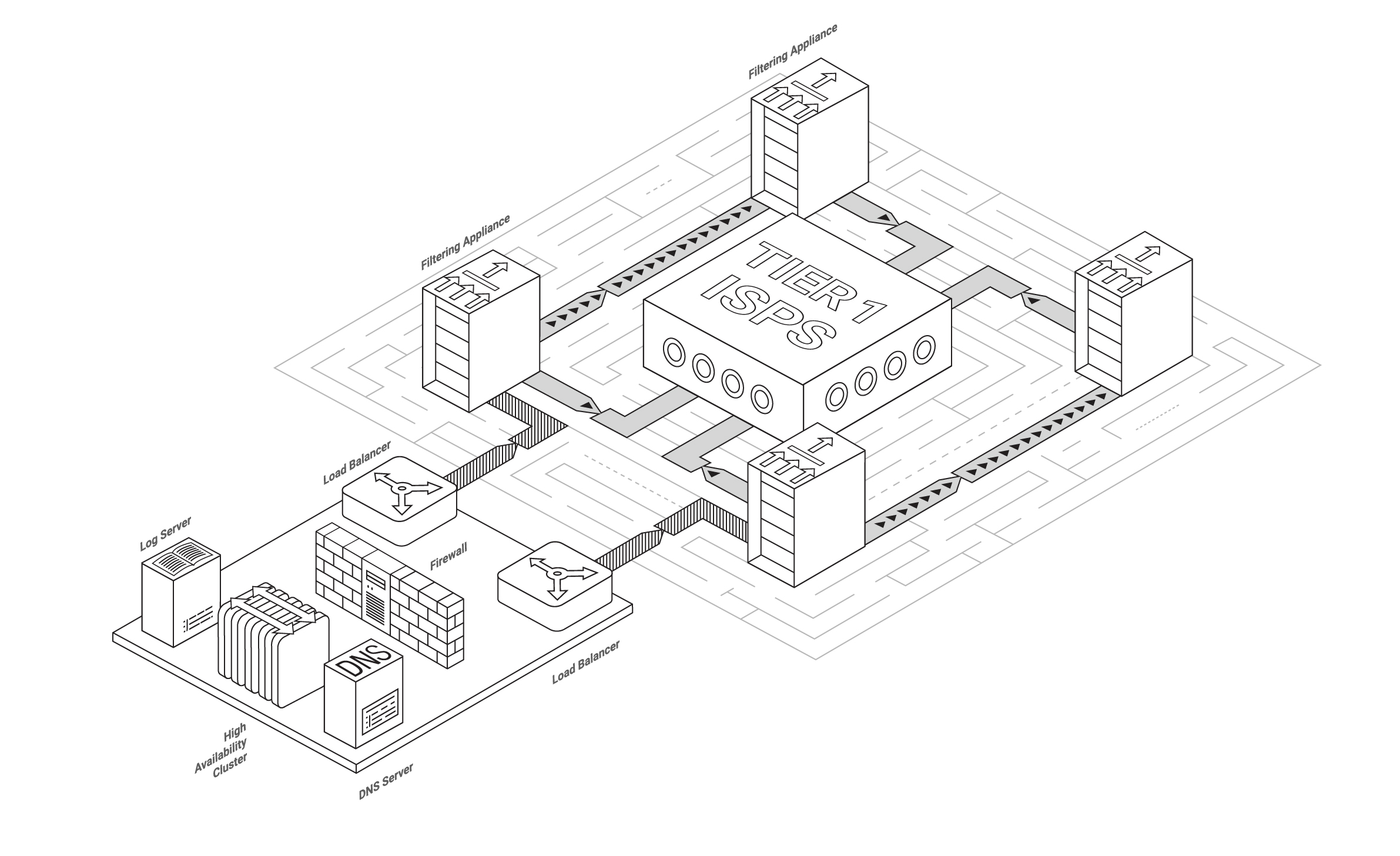
Beautiful scheme for BGP connection to Qrator filtering network
A little historical overview
- BGP hijacks — when an ISP originates an advertisement of address space that does not belong to it;
- BGP route leaks — when an ISP advertises prefixes received from one provider or peer to another provider or peer.
This week it has been 11 years since the memorable YouTube BGP incident, provoked by the global propagation of a more specific prefix announce, originated by the Pakistan Telecom, leading to an almost 2 hour in duration traffic disruption in the form of redirecting traffic from legitimate path to the bogus one. We could guess if that event was intentional, and even a correct answer wouldn’t help us completely prevent such incidents from happening today. While you read this, a route leak or a hijack is spreading over the networks. Why? Because BGP is not easy, and configuring a correct and secure setup is even harder (yet).
In these eleven years, BGP hijacking became quite damaging attack vector due to the BGP emplacement in the architecture of modern internet. Thanks to BGP, routers not only acquire peer information, and therefore all the Internet routes — they are able of calculating the best path for traffic to its destination through many intermediate (transit) networks, each representing an individual AS. A single AS is just a group of IPv4 and/or IPv6 networks operating under a single external routing policy.









