The sound of rock music, in particular of hard rock and heavy metal, is largely based on a specially distorted guitar sound, for which electronic “distortion” devices, tube amplifiers in “overloaded” mode, computers with appropriate software and digital processors are used. increasingly using neural network algorithms.
The distorted sound of electric guitars began to gain popularity around the 1960s. Since that time, the sound of overloaded tube amplifiers, connected to powerful dedicated guitar speakers with large dedicated speakers, has been considered the benchmark in rock music. But tube amplifiers were relatively expensive and inconvenient to operate. Therefore, semiconductor distortion devices were developed.
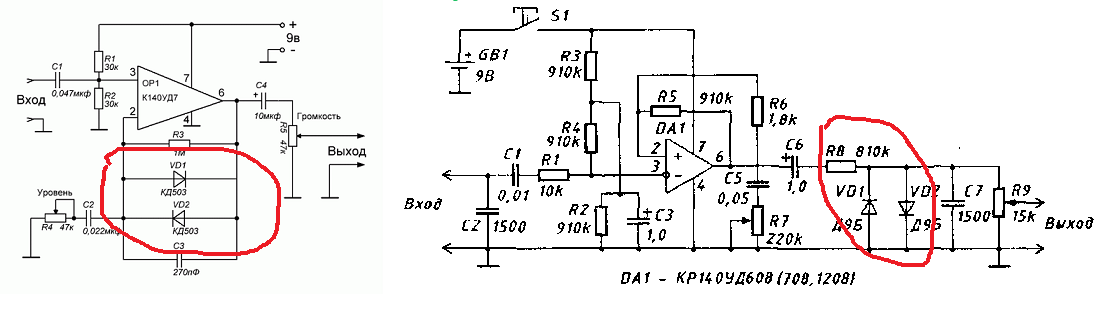
At that time, the electrical circuitry of distortion devices was relatively simple and the signal output from their output only vaguely resembled the sound of an overloaded tube amplifier. Nevertheless, it was still somewhat similar to the “sound of a lamp” and this provided a powerful incentive for designers of analog semiconductor distortion circuits to continue their research, complicate circuits and propose new circuit solutions. The heyday of analog solid-state distortion was around 1995-2010. The most popular were electrical circuit diagrams like those shown in the figure below.