
Cloud computing *
The concept of sharing resources
11 Kubernetes implementation mistakes – and how to avoid them

I manage a team that designs and introduces in-house Kubernetes aaS at Mail.ru Cloud Solutions. And we often see a lack of understanding as to this technology, so I’d like to talk about common strategic mistakes at Kubernetes implementation in major projects.
Most of the problems arise because the technology is quite sophisticated. There are unobvious implementation and operation challenges, as well as poorly used advantages, all of those resulting in money loss. Another issue is the global lack of knowledge and experience with Kubernetes. Learning its use by the book can be tricky, and hiring qualified staff can be challenging. All the hype complicates Kubernetes-related decision making. Curiously enough, Kubernetes is often implemented rather formally – just for it to be there and make their lives better in some way.
Hopefully, this post will help you to make a decision you will feel proud of later (and won’t regret or feel like building a time machine to undo it).
The hunt for vulnerability: executing arbitrary code on NVIDIA GeForce NOW virtual machines
Introduction
Against the backdrop of the coronavirus pandemic, the demand for cloud gaming services has noticeably increased. These services provide computing power to launch video games and stream gameplay to user devices in real-time. The most obvious advantage of this gaming type is that gamers do not need to have high-end hardware. An inexpensive computer is enough to run the client, spending time in self-isolation while the remote server carries out all calculations.
NVIDIA GeForce NOW is one of these cloud-based game streaming services. According to Google Trends, worldwide search queries for GeForce NOW peaked in February 2020. This correlates with the beginning of quarantine restrictions in many Asian, European, and North and South American countries, as well as other world regions. At the same time in Russia, where the self-isolation regime began in March, we see a similar picture with a corresponding delay.
Given the high interest in GeForce NOW, we decided to explore this service from an information security standpoint.
Production-ready chatbot in GCP for less than a dollar

We have all been there — having a nice idea for a hackathon, hobby or a side project and having a burning desire to start coding as soon as possible. And how many possibilities (Heroku, Glitch and others) are there now to bootstrap your app and deploy it immediately.
The QC House of Cards
Gold rushes can make people crazy. 1848 was enough of an indicator of that. When Sam Brannan announced to the world: ‘Gold! Gold! Gold from the American River!’, half the world’s population (or so it seemed to the tiny California population which lived there at the time) descended on the soon to be the newest state of the union.
San Francisco, before a small hamlet with a few hundred pioneers living there, became a centre of vice, murder and debauchery overnight.

Two hundred years before tulip mania hit Europe, and like in California with its argonauts or 49ers, it impoverished more than it made rich. In the early 2000s, too, the Dot.Com bubble created a speculative tendency in people when irrationality took over all reason.
How to Deploy Hyperledger Fabric 1.4 to AWS
The documentation of Hyperledger Fabric describes the creation of a blockchain network on one machine using Docker, where each member of the network is a separate container. But the process of setting up a network on several physical or virtual machines is not well described. Therefore, we decided to discuss this in the article.
Our blockchain application is a service for storing the medical data of school and preschool children. The data must remain unchanged. It will be presented in the form of information on vaccination and on the patient's agreement with a particular doctor. The members of the network include Parents (an organization that represents the interests of parents), Hospital (a hospital which represents pediatricians with whom parents can enter into an agreement to care for their children) and Kindergarten (a kindergarten that can request health and vaccinations reports of a child from the hospital).
Scientists Turn a Quantum Computer into a Time Machine — At least, for a Second…
Scientists said they were able to return the state of a quantum computer a fraction of a second into the past, according to a university press release. The researchers, who are from the Moscow Institute of Physics and Technology, along with colleagues from the U.S. and Switzerland, also calculated the probability that an electron in empty interstellar space will spontaneously travel back into its recent past. The study came out recently in Scientific Reports.“This is one in a series of papers on the possibility of violating the second law of thermodynamics. That law is closely related to the notion of the arrow of time that posits the one-way direction of time: from the past to the future,” commented the study’s lead author Gordey Lesovik, who heads the Laboratory of the Physics of Quantum Information Technology at MIPT.
While the researchers don’t expect you to take a trip back to the high school prom just yet, they added that the time reversal algorithm could prove useful for making quantum computers more precise.
“Our algorithm could be updated and used to test programs written for quantum computers and eliminate noise and errors,” Lebedev explained.
The researchers said that the work builds on some earlier work that recently garnered headlines.
“We began by describing a so-called local perpetual motion machine of the second kind. Then, in December, we published a paper that discusses the violation of the second law via a device called a Maxwell’s demon,” Lesovik said. “The most recent paper approaches the same problem from a third angle: We have artificially created a state that evolves in a direction opposite to that of the thermodynamic arrow of time.”
Safe-enough linux server, a quick security tuning
The case: You fire up a professionally prepared Linux image at a cloud platform provider (Amazon, DO, Google, Azure, etc.) and it will run a kind of production level service moderately exposed to hacking attacks (non-targeted, non-advanced threats).
What would be the standard quick security related tuning to configure before you install the meat?
release: 2005, Ubuntu + CentOS (supposed to work with Amazon Linux, Fedora, Debian, RHEL as well)

The World’s Top 12 Quantum Computing Research Universities
In just a few years, quantum computing and quantum information theory has gone from a fringe subject offered in small classes at odd hours in the corner of the physics building annex to a full complement of classes in well-funded programs being held at quantum centers and institutes at leading universities.
The question now for many would-be quantum computer students is not, “Are there universities that even offer classes in quantum computing,” but, rather, “Which universities are leaders at quantum computing research.”
We’ll look at some of the best right now:
The Institute for Quantum Computing — University of Waterloo
The University of Waterloo can proudly declare that, while many universities avoided offering quantum computing classes like cat adoption agencies avoided adoption applications from the Schrodinger family, this Canadian university went all in.
And it paid off.
Build apps for free with Azure Cosmos DB Free Tier

With Azure Cosmos DB Free Tier enabled, you’ll get the first 400 RU/s throughput and 5 GB storage in your account for free each month, for the lifetime of the account. That means that you can start small and grow with confidence, knowing your app will be running on a high-performance database service. You’ll only pay if your account exceeds 400 RU/s and 5 GB. Additionally, if your app has a lot of containers you can create up to 25 containers in a shared throughput database and have them all share the free 400 RU/s. You can have up to one free tier Azure Cosmos DB account per Azure subscription.
Fault Tolerance Web Architecture for Our Cloud Solutions

Hi Habr,
I'm Artyom Karamyshev, a system administration team leader at Mail.Ru Cloud Solutions (MCS). We launched many products in 2019. We've aimed to make API services easily scalable, fault-tolerant, and ready to accommodate rapid growth. Our platform is running on OpenStack, and in this article, I describe all the component fault tolerance issues that we've resolved.
The overall fault tolerance of the platform is consists of its components fault tolerance. So, I'm going to show you step by step tutorial about all levels where we've found the risks.
Announcing the preview of Azure Spot Virtual Machines
The workloads that are ideally suited to run on Spot Virtual Machines include, but are not necessarily limited to, the following:
- Batch jobs.
- Workloads that can sustain and/or recover from interruptions.
- Development and test.
- Stateless applications that can use Spot Virtual Machines to scale out, opportunistically saving cost.
- Short-lived jobs which can easily be run again if the Virtual Machine is evicted.

Learn Azure in a Month of Lunches — our new free e-book
Read this e-book to build your cloud computing skills quickly and efficiently. You’ll be productive immediately, and when you finish, you’ll be well on your way to Azure mastery.
Learn more below.

Datacenter TCP explained
DCTCP is a set of modification to TCP, targeting to fulfill two properties:
1. Improve latency for latency-sensitive small messages
2. Not to decrease the throughput for throughput-sensitive big flows
Azure Media Services' new AI-powered innovations
Signing into Azure DevOps using your GitHub credentials
Across all of Microsoft, we are focusing on empowering developers to build better apps, faster. One way we are accomplishing that is by providing a range of products and services covering all stages of the software development lifecycle. This includes IDEs and DevOps tools, application and data platforms on the cloud, operating systems, Artificial Intelligence and IoT solutions, and more. All of these are centered around developers, both as individuals working in teams and organizations, and as members of developer communities.
GitHub is one of the largest developer communities, and for millions of developers around the world their GitHub identity has become a critical aspect of their digital life. Recognizing that, we’re excited to announce improvements that will help GitHub users get started more easily with our developer services, including Azure DevOps and Azure.
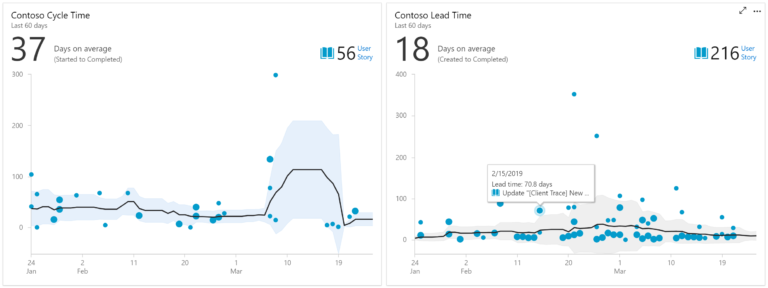
Analytics For Azure DevOps Services is Now Generally Available
Reporting has been an important capability for Azure DevOps customers who rely on Analytics to make data driven decisions.
Today, we’re excited to announce that the following Analytics features listed below will be included in our Azure DevOps Services offering at no additional cost. Customers will start to see these changes rolled out to their accounts soon.
Extending Azure security capabilities
As more organizations are delivering innovation faster by moving their businesses to the cloud, increased security is critically important for every industry. Azure has built-in security controls across data, applications, compute, networking, identity, threat protection, and security management so you can customize protection and integrate partner solutions.
We keep investing in security and we are excited to share exciting updates this week at Hannover Messe 2019. We are excited to announce that Dedicated Hardware Security Module Service (HMS) in UK, Canada, and Australia, Azure disk encryption support for Virtual Machine Scale Sets (VMSS) are generally available. Also Advanced Threat Protection for Azure Storage, the Regulatory Compliance Dashboard, and support for virtual machine sets are now generally available as part of Azure Security Center.

How iOS Developers Are Seeking To Up The Ante With Cloud Computing

As a platform, many enterprises are leveraging iOS to realize the amazing benefits of cloud computing. This is one aspect of digital transformation that has been rocking the entire industry in recent times. Generally, there is only a few internet-based development and deployment service performed on the platform that is not concerned with cloud application development. Nowadays, there is a growing population of iOS developers and app development companies that are steadily adopting cloud computing.
Pentesting Azure — Thoughts on Security in Cloud Computing
 A few months ago I worked with a customer on how a team should evaluate the security of their Azure implementation. I had never done a pentest(extensive security testing)on an Azure application before, so these ideas were just the thoughts off of the top of my head at that time based on my experience in security.
A few months ago I worked with a customer on how a team should evaluate the security of their Azure implementation. I had never done a pentest(extensive security testing)on an Azure application before, so these ideas were just the thoughts off of the top of my head at that time based on my experience in security.Matt Burrough’s book, Pentesting Azure Applications, goes even deeper and it is a must-read for security experts focused in Cloud Computing, I’m reading it right now.
Below I share with you these pre-book thoughts, and will compare them in a future article with the ones I will learn — or confirm — after reading Matt's book.