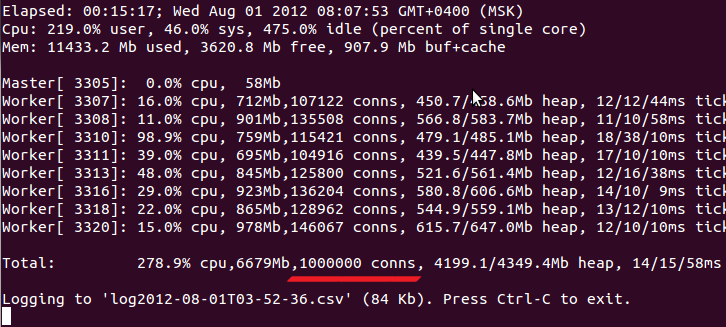
*много букв, местами неполиткорректно, текст лежал в столе 5 лет

Первое знакомство с представителями Китая на Сцене произошло через 2 дня после моего «
входа» в ту самую Сцену. Мне понадобился доступ к популярному в то время варез-FTP “
Typhoon Epicenter” (о том, что он располагался в Гонг Конге я узнал позже). Из всех друзей и знакомых организовать доступ мог только один человек – «
приятель знакомого моего друга». Он оказался китайцем по вере и паспорту, и мы некоторое время плотно общались. Именно после знакомства с ним, я стал относиться к китайцам с пассивным интересом.
Это сумасшедшие в плане доведения своих навыков до абсолюта. Собственно, мы за это их и уважали, потому что у них были "
мозги", которых порой не хватало нам – не в плане ума, а в плане кадров. А еще их было много… чертовски много.
Чаще всего китайцы вызывали у нас 3 вида эмоций: уважение, зависть и раздражение. В годах 1997-2004 любой пират, катающий болванки «Лучший Soft 200x», отдал бы почку за доступ к паре варезных серверов Китая.




 Код Хромиума весьма обширен, там каждому найдётся что-то по вкусу. А я вот решил рассказать о своём любимом файле в нём (а у вас есть такой?). Этот файл отражает всё: боль, разочарование, надежду, упорство, силу воли, ответственность за чужие провалы и самопожертвование. Я иногда читаю его
Код Хромиума весьма обширен, там каждому найдётся что-то по вкусу. А я вот решил рассказать о своём любимом файле в нём (а у вас есть такой?). Этот файл отражает всё: боль, разочарование, надежду, упорство, силу воли, ответственность за чужие провалы и самопожертвование. Я иногда читаю его 
 Первое знакомство с представителями Китая на Сцене произошло через 2 дня после моего «входа» в ту самую Сцену. Мне понадобился доступ к популярному в то время варез-FTP “Typhoon Epicenter” (о том, что он располагался в Гонг Конге я узнал позже). Из всех друзей и знакомых организовать доступ мог только один человек – «приятель знакомого моего друга». Он оказался китайцем по вере и паспорту, и мы некоторое время плотно общались. Именно после знакомства с ним, я стал относиться к китайцам с пассивным интересом.
Первое знакомство с представителями Китая на Сцене произошло через 2 дня после моего «входа» в ту самую Сцену. Мне понадобился доступ к популярному в то время варез-FTP “Typhoon Epicenter” (о том, что он располагался в Гонг Конге я узнал позже). Из всех друзей и знакомых организовать доступ мог только один человек – «приятель знакомого моего друга». Он оказался китайцем по вере и паспорту, и мы некоторое время плотно общались. Именно после знакомства с ним, я стал относиться к китайцам с пассивным интересом.