Demid Efremov and Ivan Kornienko.
Music box on Verilog HDL for Cyclone IV.
Demid Efremov and Ivan Kornienko.
Music box on Verilog HDL for Cyclone IV.
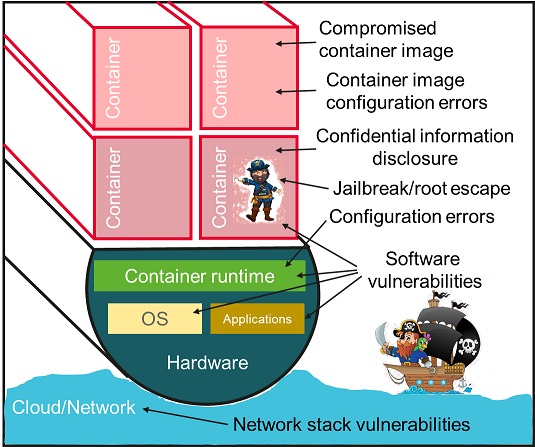
In any history textbooks, the modern time has already been called the time of the next change of the industrial structure or the fourth industrial revolution (Industry 4.0). The main role, in this case, is given to information and IT systems. In an attempt to reduce the cost of IT infrastructure, unify and accelerate the process of developing IT solutions, humanity first invented "clouds" in order to replace traditional data centers, and then containers to replace virtual machines.
Clearly, containers appear more vulnerable from a security point of view. What are the advantages of containerization over virtualization? In fact, there are quite a lot of them:
• the possibility of more flexible use of available resources (no need to backup them as in the case of virtual machines);
• the ability to save resources (no need to spend them on many copies of the OS for each virtual machine);
• no delays at startup (just start of the process is almost instantaneous compared to the time needed to load the virtual machine);
• the interaction between processes, even if isolated, is much easier to implement when needed than between virtual machines. That is how, by the way, came the concept of microservices, which has recently become very popular.
All of the above led to the very rapid development of container technologies, despite the recurring problems with the security of already deployed container cloud systems, their hacks, and data leaks. Accordingly, the work on strengthening container security is also continuing. This is what will be discussed further in this article.
This article investigates why the standard library needs a way to deduce a common type, how it is implemented and how it works.
It's cool when enthusiastic developers create a working clone of a famous game. It's even cooler when people are ready to continue the development of such projects! In this article, we check TheXTech with PVS-Studio. TheXTech is an open implementation of the game from the Super Mario universe.

Multimodality has led the pack in machine learning in 2021. Neural networks are wolfing down images, text, speech and music all at the same time. OpenAI is, as usual, top dog, but as if in defiance of their name, they are in no hurry to share their models openly. At the beginning of the year, the company presented the DALL-E neural network, which generates 256x256 pixel images in answer to a written request. Descriptions of it can be found as articles on arXiv and examples on their blog.
As soon as DALL-E flushed out of the bushes, Chinese researchers got on its tail. Their open-source CogView neural network does the same trick of generating images from text. But what about here in Russia? One might say that “investigate, master, and train” is our engineering motto. Well, we caught the scent, and today we can say that we created from scratch a complete pipeline for generating images from descriptive textual input written in Russian.
In this article we present the ruDALL-E XL model, an open-source text-to-image transformer with 1.3 billion parameters as well as ruDALL-E XXL model, an text-to-image transformer with 12.0 billion parameters which is available in DataHub SberCloud, and several other satellite models.
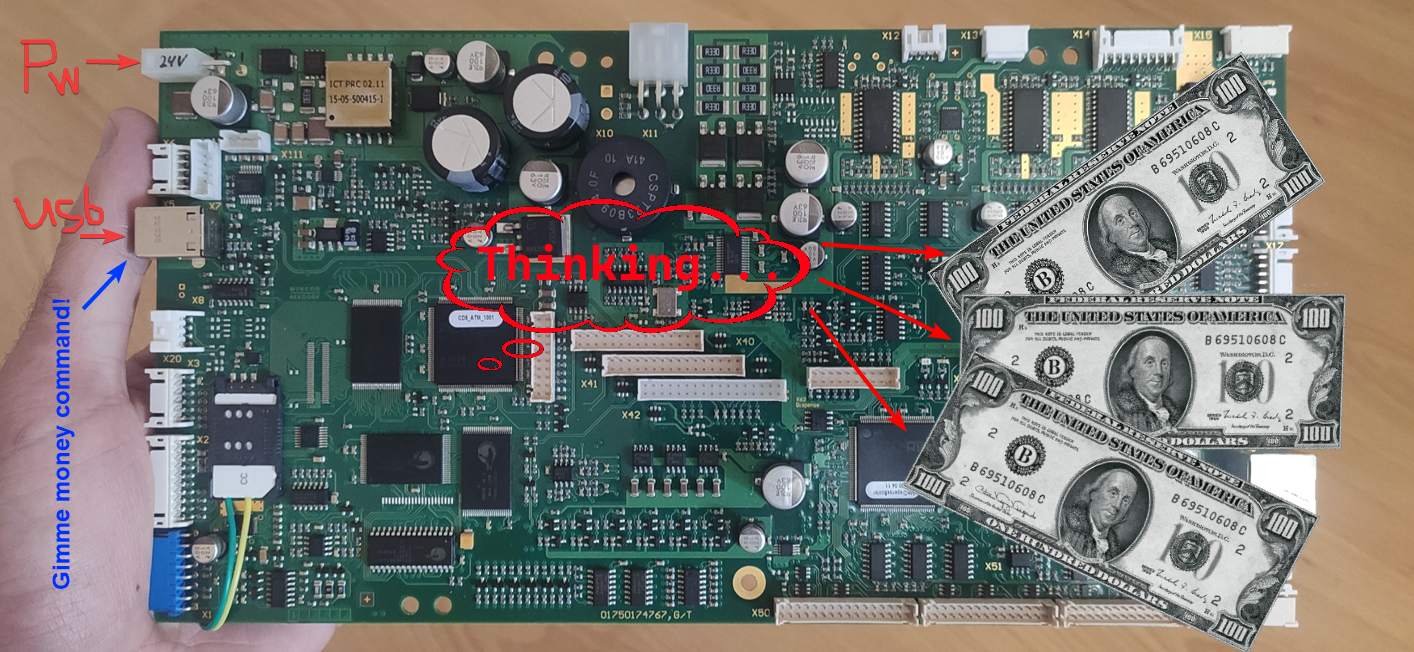
Hi there! A while ago, Positive Technologies published the news that ATMs manufactured by Diebold Nixdorf (previously known as Wincor), or more specifically, the RM3 and CMDv5 cash dispensers, contained a vulnerability which allowed attackers to withdraw cash and upload modified (vulnerable) firmware. And since my former colleague Alexei Stennikov and I were directly involved in finding this vulnerability, I would like to share some details.
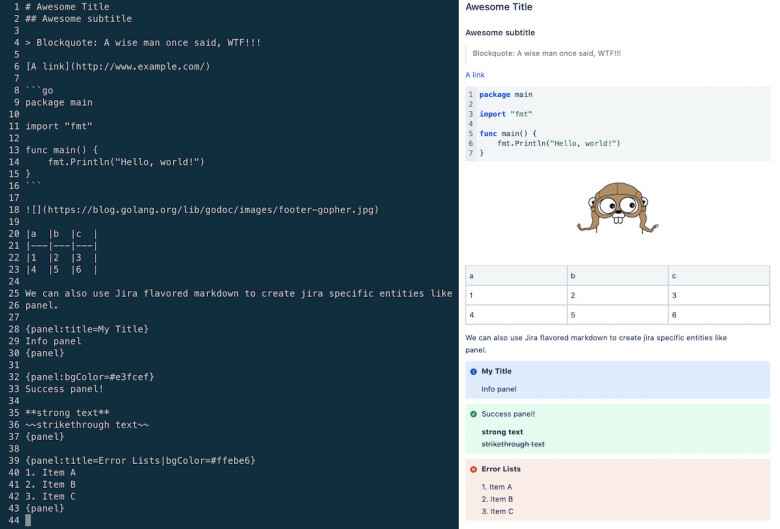
JiraCLI is an interactive command line tool for Atlassian Jira that will help you avoid Jira UI to some extent. This tool is not yet considered complete but has all the essential features required to improve your workflow with Jira.
The tool started with the idea of making issue search and navigation as straightforward as possible. However, the tool now includes all necessary features like issue creation, cloning, linking, ticket transition, and much more.
The tool supports both jira cloud and on-premise jira installation since the latest release.

Proactive search for complex threats seems to be a useful technology but inaccessible for many organizations. Is it really so? What do companies need to do to start Threat Hunting? What tools are needed for threat hunting? What trends in this area can be seen on the market in the coming years? These are some of the questions I would like to answer in my article today.
What is Threat Hunting?
Threat Hunting is a search for threats in a proactive mode when the information security specialist is sure that the network is compromised. He should understand how his network operates in order to be able to identify various attacks by examining the existing anomalies.
Threat Hunting is a search for threats that have already bypassed automated detection systems. Moreover, most often, you do not have signals or alerts that allow you to detect an intrusion.
From the SOC perspective, Threat Hunting is an extension of the service that allows you to counter any level of intruders, including those who use previously unknown tools and methods.
Threat Hunting can be based on some data obtained by a security specialist, or it can be based on a hypothesis. If after testing the hypothesis, the test gives a positive result, then later, it can be used to improve the processes and mechanisms of detecting threats. And also, Threat Hunting allows you to find blind spots in the security system and expand the monitoring area.
What organizations need Threat Hunting?
Proactive threat hunting is relevant to those organizations that can become the target of a complex, targeted APT attack. At the same time, given the trend towards supply chain attacks, a small company may also become a target for motivated attackers.
 Since 2011 all Intel GPUs (integrated and discrete Intel Graphics products) include Intel Quick Sync Video (QSV) — the dedicated hardware core for video encoding and decoding. Intel QSV is supported by all popular video processing applications across multiple OSes including FFmpeg. The tutorial focuses on Intel QSV based video encoding and decoding acceleration in Windows native (desktop) applications using FFmpeg/libavcodec for video processing. To illustrate concepts described, the open source 3D Streaming Toolkit is used.
Since 2011 all Intel GPUs (integrated and discrete Intel Graphics products) include Intel Quick Sync Video (QSV) — the dedicated hardware core for video encoding and decoding. Intel QSV is supported by all popular video processing applications across multiple OSes including FFmpeg. The tutorial focuses on Intel QSV based video encoding and decoding acceleration in Windows native (desktop) applications using FFmpeg/libavcodec for video processing. To illustrate concepts described, the open source 3D Streaming Toolkit is used.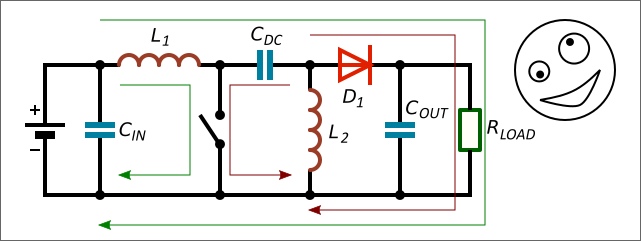
Knowing parameters of small-signal control-to-output transfer functions makes it easier for engineers to design compensation networks of DC/DC converters. The equations for SEPIC can be found in different works and Application Notes, but there are differences. A work has been done to solve this problem.
Simplified design equations for SEPIC with Current Mode control (CM) in Continuous Conduction Mode (CCM) suitable for practical design of compensation networks are shown.
Hello!
This post is about writing a fast enumerator in C#:
foreach (var i in 1..10)
We will figure out whether it's possible to make it as fast as for, and what can we do to improve our performance.
A lot of benchmarks and sharplab coming. Let's rock!

In my project, I was faced with the need to implement a scroll bar. The standard approaches didn't fully satisfy what designers wanted to see. Here is an example, it is slightly different in appearance from what I needed, but the essence is approximately the same: the scroll bar should be on the right side of the list and take into account the padding of the scroll bar, with the slider displaying the percentage of the scrolled part of the list.
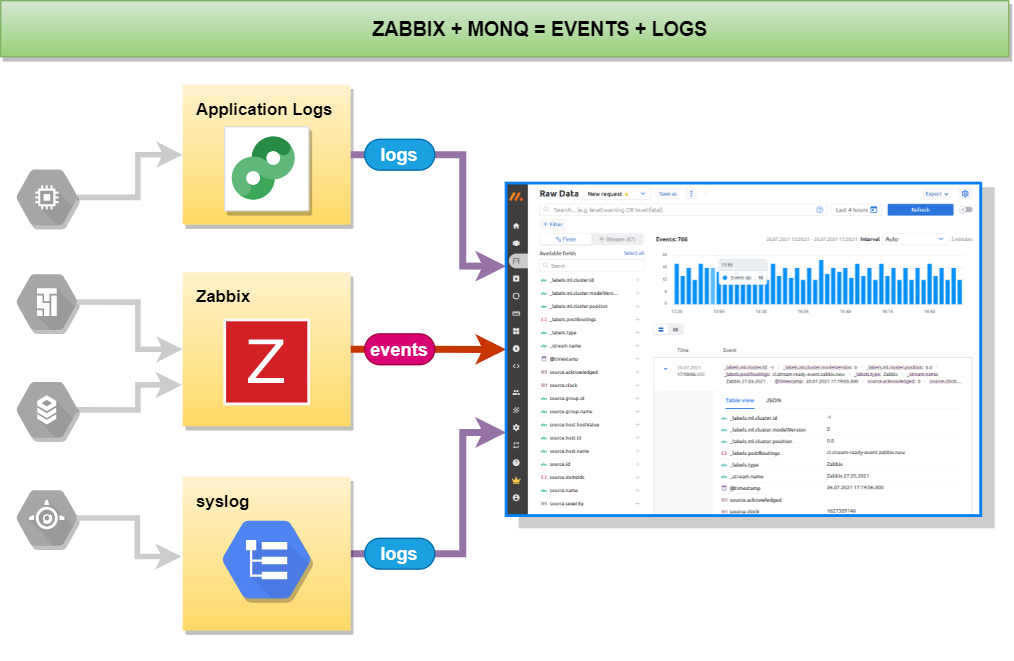
If you use Zabbix to monitor your infrastructure objects but have not previously thought about collecting and storing logs from these objects then this article is for you.
People increasingly start optimizing the process of finding code errors using static analyzers. Nowadays, we can choose from a variety of products to view analysis results. This post covers the ways how to view an analyzer report in the most stylish and feature-rich IDE among multifunctional ones – VSCode. The SARIF format and a special plugin for it allow us to perform our task. Keep reading to find out about this. Let's get going!
Couple of weeks ago (or to be more precise, on July 2, 2021), the legendary BitTorrent protocol turned twenty years old. Created by Bram Cohen, the protocol has been developing rapidly since its inception, and has quickly become one of the most popular ways to exchange files. So why not check out a couple of long-lived related projects with the PVS-Studio analyzer for Linux?


In the first part of You don't know Redis, I built an app using Redis as a primary database. For most people, it might sound unusual simply because the key-value data structure seems suboptimal for handling complex data models.
In practice, the choice of a database often depends on the application’s data-access patterns as well as the current and possible future requirements.
Redis was a perfect database for a Q&A board. I described how I took advantage of sorted sets and hashes data types to build features efficiently with less code.
Now I need to extend the Q&A board with registration/login functionality.
I will use Redis again. There are two reasons for that.
Firstly, I want to avoid the extra complexity that comes with adding yet another database.
Secondly, based on the requirements that I have, Redis is suitable for the task.
Important to note, that user registration and login is not always about only email and password handling. Users may have a lot of relations with other data which can grow complex over time.
Despite Redis being suitable for my task, it may not be a good choice for other projects.
Always define what data structure you need now and may need in the future to pick the right database.

Goal: continuously send UDP packets from an Arduino Nano 33 IoT to a Raspberry Pi 4 to understand the reliability of this solution.
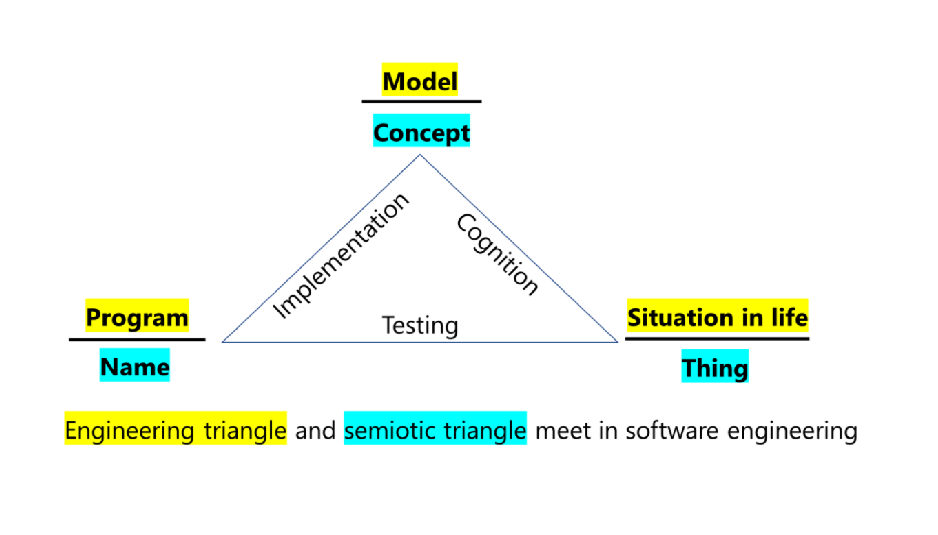
We present a guide to name entities in code based on putting naming in perspectives of semantic space, design, and readability.
The main idea is that naming should not be considered as creation of tags, but as a fundamental part of design process, which implies integral and consistent vocabulary to be used. We discuss naming process and naming formalism from these perspectives and we provide guidelines for practical use.
The work is based on 15 years of experience in engineering work, coding and development management in high-tech industries.
PVS-Studio is a static analysis tool that helps find errors in software source code. This time PVS-Studio looked for bugs in Storm Engine's source code.

Setting up Atom for working with python is quite a tricky task. I've spent a lot of time making it work. Autocompleting, autoformatting, type hints, and much more will be available to you after reading this tutorial.