
This article covers the new version of the C# language - C# 10. Compared to C# 9, C# 10 includes a short list of enhancements. Below we described the enhancements and added explanatory code fragments. Let's look at them.

This article covers the new version of the C# language - C# 10. Compared to C# 9, C# 10 includes a short list of enhancements. Below we described the enhancements and added explanatory code fragments. Let's look at them.
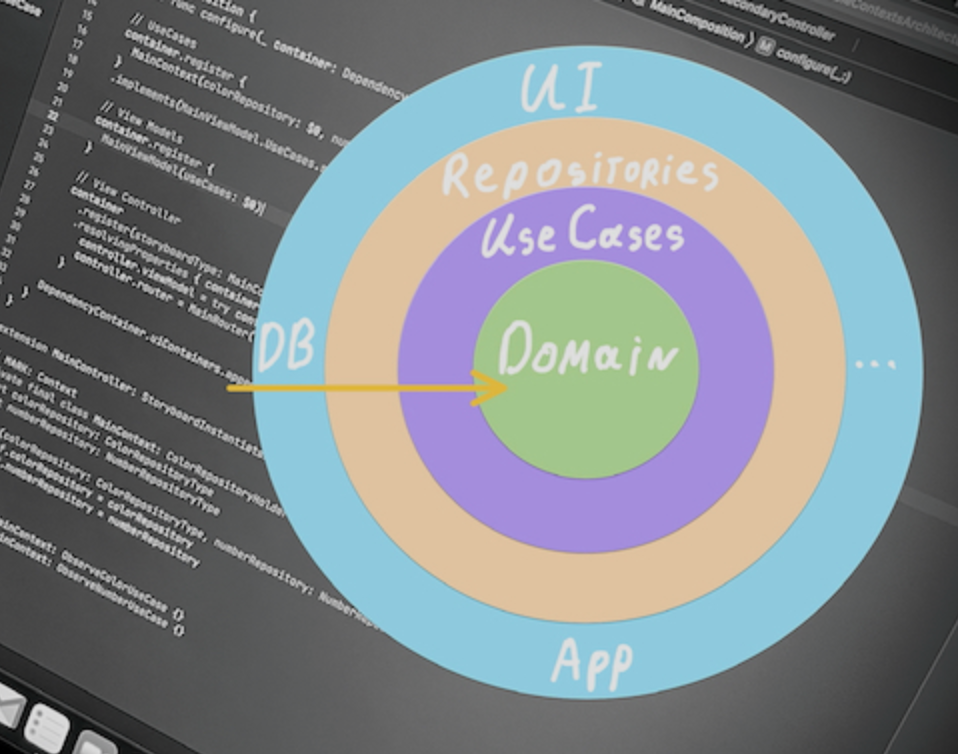
Let’s talk about app architecture and the approach I apply as an iOS software engineer in a few companies. My team and I were trying to build something solid without slipping into a dense swamp where following the rules distracts you from actual business domain code. As a result, we got something that works for us and good enough to be told from my point of view.

I am not an economist, but in light of current events with cryptocurrencies and the economy in general, I would like to share my thoughts on some kind of ideal economy, around which everything is happening now.
My name is Serhii Pimenov. I’m a web developer from Kyiv, Ukraine (maybe you know me by the nickname olton).
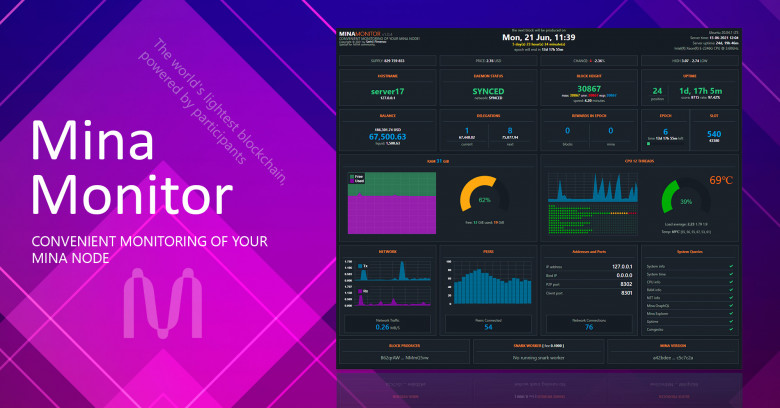
Today I'm going to speak about one of my tools for the Mina blockchain - “Mina Monitor”. It’s the first article in the series about Mina and Mina Tools. In this article, I will introduce you to my tool for monitoring the Mina nodes.
UIKit first appeared in iOS 2, and it is still here. Eventually we got to know it well and learned how to work with it. We have found many architectural approaches. MVVM, the most popular architecture in my opinion, has strengthened its position with the release of SwiftUI, while other architectures seemed to have some kind of problematic relationships with SwiftUI.
But what if I told you that Clean Swift, VIPER and other approaches can be adapted to SwiftUI. What if I told you that there are some modern architectures which might be as good as MVVM or even better.
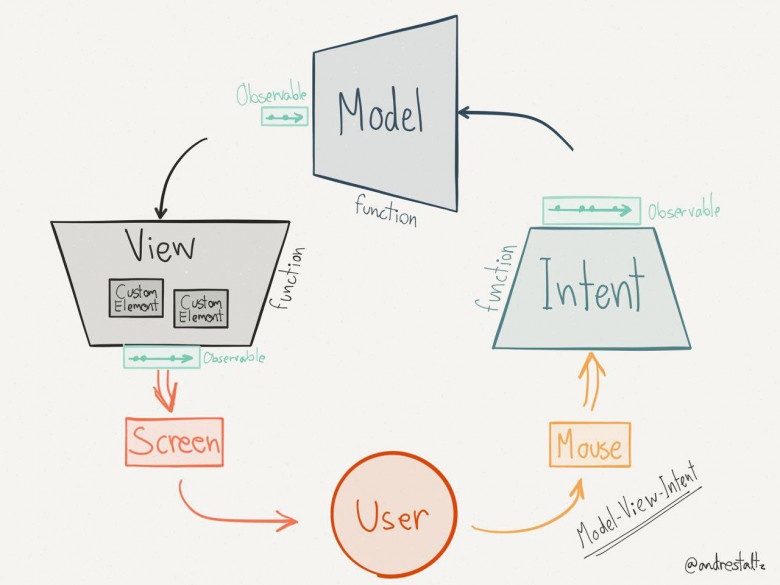
We will talk about MVI.
Modern applications have lots of code. And the C++ language doesn't get easier. Nowadays, code reviews are not enough to fully analyze program code. Here's where static code analysis comes in.

In this video, we are making a cable for connecting a quadrature encoder to a Servosila brushless motor controller, and and then running a servo motor in Direct Drive mode. To make the cable we are using a cable assembly kit that can be purchased from the internet store. Alternatively, the components for the cable can be bought in other places. The part numbers are given in the controller's datasheet.
The cable assembly kit consists of a connector and a set of wires with pre-crimped socket blades. If you have a crimper tool, you can also attach the socket blades to wires by yourself.
Lets open a datasheet document that comes with the brushless motor controller. Note that each connector has its first pin clearly marked with a "1" sign. Conventionally, the numbering of pins is done in such a way that there are rows of odd-numbered and even-numbered pins.
The quadrature encoder's electrical interface has 5 wires in total. Positions of the pins of each of the wires are given in the table. The socket blades need to be pushed into the connector until you feel a "click". The blades lock into the connector's sockets. Optionally, primarily for cosmetic reasons, you may want to add a heat-shrink tubing to your cable.
The brushless motor controllers come in two distinct forms, a circular and a rectangular one. Both models are identical in terms of capabilities, features, firmware, and external electrical connectors.
The connector has a locking mechanism that keeps it in place. I soldered a mating connector to the other side of the cable - a connector that my brushless motor needs. Note that your motor will likely require a different connector, or no connector at all. It is always a good idea to test an end-to-end integrity of the cable and its connectors. Lets buzz the wires using a multimeter. The cable is ready.
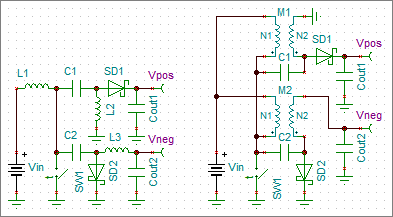
SEPIC-Ćuk split-rail converter can be used to make positive and negative supplies from a single input voltage for relatively well-matched loads like operational amplifiers.
Transient models are time consuming. Average models reduce modeling time drastically.
The PWM switch average models for current- and voltage-mode are described in details in Christophe Basso’s book “Switch-Mode Power Supplies, Second Edition: SPICE Simulations and Practical Designs”. Using of these models for SEPIC and Ćuk converters is also shown.
This text shows how to use the PWM switch average model to design a split-rail SEPIC-Ćuk converter.
Commercial static analyzers perform deeper and fuller code analysis compared to compilers. Let's see what PVS-Studio found in the source code of the LLVM 13.0.0 project.

Working with speech recognition models we often encounter misconceptions among potential customers and users (mostly related to the fact that people have a hard time distinguishing substance over form). People also tend to believe that punctuation marks and spaces are somehow obviously present in spoken speech, when in fact real spoken speech and written speech are entirely different beasts.
Of course you can just start each sentence with a capital letter and put a full stop at the end. But it is preferable to have some relatively simple and universal solution for "restoring" punctuation marks and capital letters in sentences that our speech recognition system generates. And it would be really nice if such a system worked with any texts in general.
For this reason, we would like to share a system that:
To reiterate — the purpose of such a system is only to improve the readability of the text. It does not add information to the text that did not originally exist.
Test automation, with product built in microservice architecture could be very situational in context of testing goals and ways to achieve them. You got an easy life if you testing a service, that is an isolated entity, which is receiving some data and providing a result of it's work in a response, by callback or through additional endpoint. In this case all you need to do is cover all the endpoints of the service, and probably learn to catch it's callbacks. However, it's not the only case. Sometimes you need to test service which isn't totally isolated, but a part of a chain of interactions. This service could send some data to other services within your infrastructure or even to third parties. This time you got plenty of additional things to bother of:

I had some experience in the matching engine development for cryptocurrency exchange some time ago. That was an interesting and challenging experience. I developed it in clear C++ from scratch. The testing of it is also quite a challenging task. You need to get data for testing, perform testing, collect some statistics, and at last, analyze collected data to find weak points and bottlenecks. I want to focus on testing the C++ matching engine and show how testing can give insights for optimizations even without the need to change the code. The matching engine I developed can do more than 1’000’000 TPS (transactions per second) and is 10x times faster than the matching engine of the Binance cryptocurrency exchange (see one post on Binance Blog).
Effective data management is a critical aspect in retail. You have to manage information about customers, products, services, staff, materials, and so on. You should have a source that you will trust. And you need to store, process, moderate, and administer data in this system.
Until recently, retailers only knew MDM - Master Data Management. A traditional MDM system is a system that knows about different data sources. It contains the “golden standard” of data.
Imagine that your stores have one customer information, your online store has another, and your marketing services have third data. MDM system collects all these types of information in a single source. The system can find the same clients, spelled differently, and eliminate errors in the data based on different algorithms.
The evolution of MDM systems has led to the emergence of highly specialized master systems. Modern business does not need to implement a heavy MDM to manage only product data. There are PIM systems for this task.

Nothing and nobody will escape oblivion. Whatever you may say, the history of mankind is a history of automation and the subsequent evolution of workers. This happened both during the first industrial revolution and during the second. The same thing happened with digital revolution. Now machine learning and artificial intelligence are being implemented everywhere. What is the future of software testing?
For the first time PVS-Studio provided support for the CWE classification in the 6.21 release. It took place on January 15, 2018. Years have passed since then and we would like to tell you about the improvements related to the support of this classification in the latest analyzer version.


Recently we released a new build of the Big Data Tools plugin that is compatible with the 2021.3 versions of IntelliJ IDEA and PyCharm. DataGrip 2021.3 support will be available immediately after the release in October. The plugin also supports our new data science IDE – JetBrains DataSpell. If you still use previous versions, now is the perfect time to upgrade both your IDE and the plugin.
This year, we introduced a number of new features as well as some features that have been there for a while, for example, running Spark Submit with a run configuration.
Here’s a list of the key improvements:
In May 2021, CppCast recorded a podcast called ABI stability (CppCast #300). In this podcast, Marshall Clow and the hosts discussed rather old news — Visual Studio compilers support the AddressSantitzer tool. We have already integrated ASan into our testing system a long time ago. Now we want to tell you about a couple of interesting errors it found.
After you read this article, you'll have the knowledge to create your own static analyzer for C#. With the help of the analyzer, you can find potential errors and vulnerabilities in the source code of your own and other projects. Are you intrigued? Well, let's get started.

Proactive search for complex threats seems to be a useful technology but inaccessible for many organizations. Is it really so? What do companies need to do to start Threat Hunting? What tools are needed for threat hunting? What trends in this area can be seen on the market in the coming years? These are some of the questions I would like to answer in my article today.
What is Threat Hunting?
Threat Hunting is a search for threats in a proactive mode when the information security specialist is sure that the network is compromised. He should understand how his network operates in order to be able to identify various attacks by examining the existing anomalies.
Threat Hunting is a search for threats that have already bypassed automated detection systems. Moreover, most often, you do not have signals or alerts that allow you to detect an intrusion.
From the SOC perspective, Threat Hunting is an extension of the service that allows you to counter any level of intruders, including those who use previously unknown tools and methods.
Threat Hunting can be based on some data obtained by a security specialist, or it can be based on a hypothesis. If after testing the hypothesis, the test gives a positive result, then later, it can be used to improve the processes and mechanisms of detecting threats. And also, Threat Hunting allows you to find blind spots in the security system and expand the monitoring area.
What organizations need Threat Hunting?
Proactive threat hunting is relevant to those organizations that can become the target of a complex, targeted APT attack. At the same time, given the trend towards supply chain attacks, a small company may also become a target for motivated attackers.
A couple of years ago the PVS-Studio analyzer got its first diagnostic rules to check program code compliance with the MISRA C and MISRA C++ standards. We collected feedback and saw that our clients were interested in using the analyzer to check their projects for MISRA compliance. So, we decided to further develop the analyzer in this direction. The article covers the MISRA C/C++ standard and the MISRA Compliance report. It also shows what we already managed to do and what we plan to achieve by the end of the year.
