Fancy Euclid's “Elements” in TeX
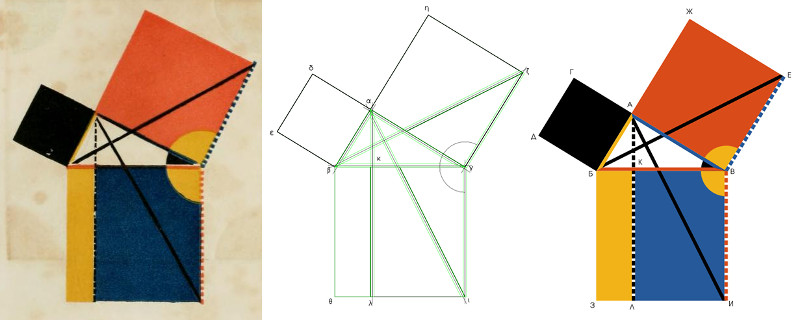
In 2016, I came across Oliver Byrne's “The first six books of the Elements of Euclid.” The main feature of this book is that instead of ordinary letter designations such as “triangle ABC,” it employs inclusions of miniature pictures directly in the text, that is, for example, an image of a triangle. As difficult as it probably was in the XIX century, as easy, with the right tools, it should be to make such a book nowadays. And so I decided to find out by myself whether that's the case.
Long journey to Tox-rs. Part 1

Hi everyone!
I like Tox and respect the participants of this project and their work. In an effort to help Tox developers and users, I looked into the code and noticed potential problems that could lead to a false sense of security. Since I originally published this article in 2016 (in Russian), many improvements have been made to Tox, and I lead a team that re-wrote secure Tox software from scratch using the Rust programming language (check out Tox-rs). I DO recommend using tox in 2019. Let's take a look what actually made us rewrite Tox in Rust.
Original article of 2016
There is an unhealthy tendency to overestimate the security of E2E systems only on the basis that they are E2E. I will present objective facts supplemented with my own comments for you to draw your own conclusions.
Spoiler: The Tox developers agree with my points and my source code pull request was accepted.
What is going to happen on February 1, 2020?
 Bangkok, in general, is a strange place to stay. Of course, it is warm there, rather cheap and some might find the cuisine interesting, along with the fact that about half of the world’s population does not need to apply for a visa in advance to get there. However, you still need to get acquainted with the smells, and the city streets are casting cyberpunk scenes more than anything else.
Bangkok, in general, is a strange place to stay. Of course, it is warm there, rather cheap and some might find the cuisine interesting, along with the fact that about half of the world’s population does not need to apply for a visa in advance to get there. However, you still need to get acquainted with the smells, and the city streets are casting cyberpunk scenes more than anything else.In particular, a photo to the left has been taken not far from the center of Thailand’ capital city, one street away from the Shangri-La hotel, where the 30th DNS-OARC organization meeting took place on May 12 and 13. It is a non-profit organization dedicated to security, stability, and overall development of the DNS — the Domain Name System.
Slides from the DNS-OARC 30 meeting are recommended for everyone interested in how the DNS works, though perhaps the most interesting is what is absent in those slides. Namely, a 45-minute round table with a discussion around the results of DNS Flag Day 2019, which occurred on February, 1, 2019.
And, the most impressive result of a round table is the decision to repeat DNS Flag Day once again.
Introducing Windows Terminal
We are beyond excited to announce Windows Terminal! Windows Terminal is a new, modern, fast, efficient, powerful, and productive terminal application for users of command-line tools and shells like Command Prompt, PowerShell, and WSL.
Windows Terminal will be delivered via the Microsoft Store in Windows 10 and will be updated regularly, ensuring you are always up to date and able to enjoy the newest features and latest improvements with minimum effort.
Frontend Weekly Digest (13 – 19 May 2019)

In-App Updates Flexible Flow: Speed Up the App Update Process on Android
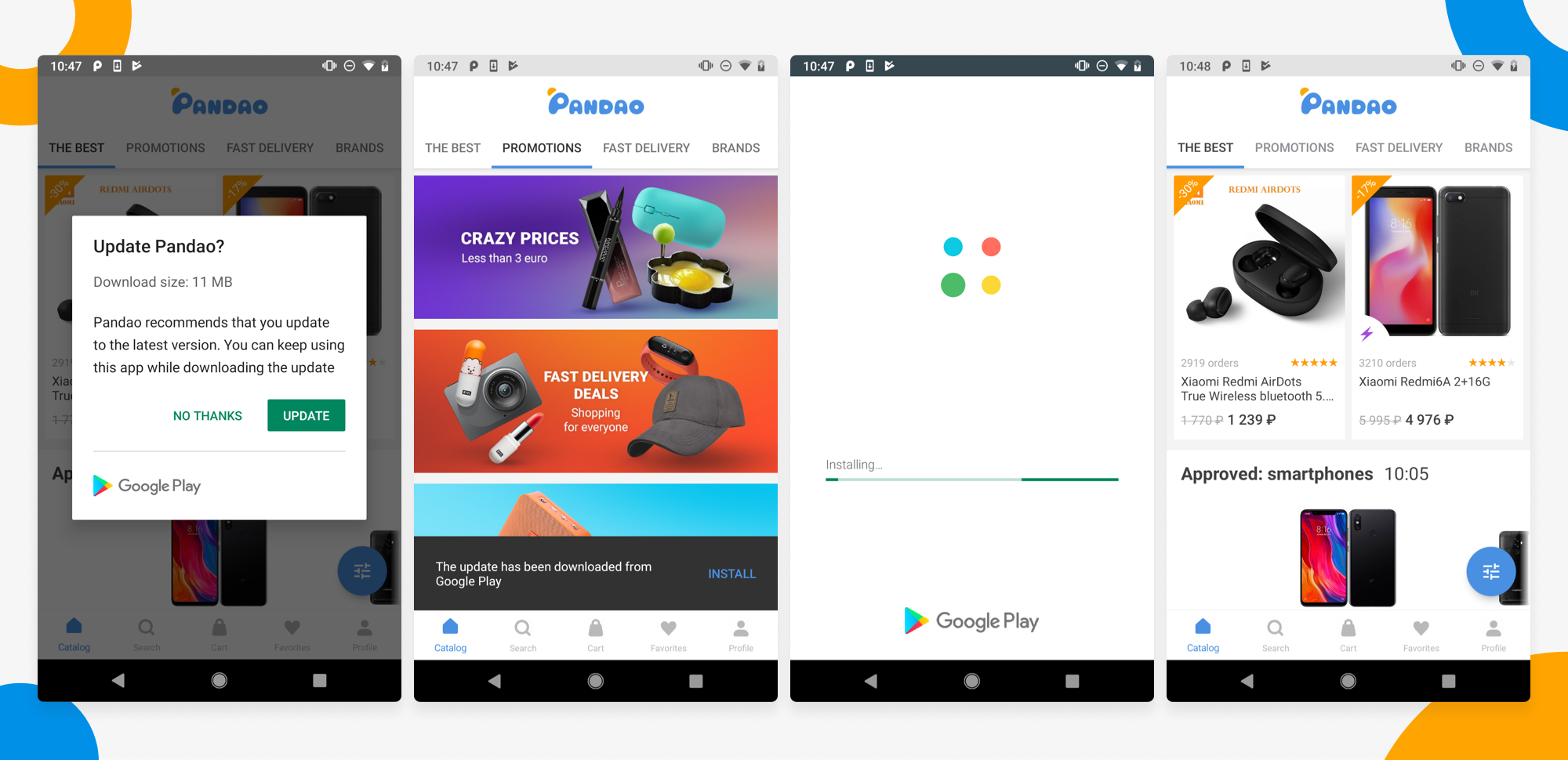
With a variety of new tools and features announced at Android Dev Summit, special attention should be given to the In-App Updates (IAUs) API allowing developers to increase the speed of delivering features, bug-fixes and performance improvements to active users. Since this feature was finally released after Google I/O 2019, in this article I’ll deep dive on IAUs API, describe in details recommended user flows and provide with some code samples. Moreover, I'll share some experience of IAUs integration in the Pandao app, a marketplace platform for Chinese goods.
Citymobil — a manual for improving availability amid business growth for startups. Part 5

This is the final part of the series describing how we’re increasing our service availability in Citymobil (you can read the previous part here). Now I’m going to talk about one more type of outages and the conclusions we made about them, how we modified the development process, what automation we introduced.
Reverse engineering a high-end soldering station

(This is the translation of the original article performed by baragol)
We had a bunch of photographs of the main PCB, a YouTube video with drain-voltage waveforms of MOSFETs, a forum post with a breakdown of the capacitance values of LC circuit capacitors and also a number of unboxing videos showing the heating-up of the soldering tip. The only thing that really worried me was the video with the measurement of the peak power consumption during the heating-up. There is nothing in the world more helpless and irresponsible and depraved than burned cartridge newly bought for 60 bucks from Amazon. But let me start from the beginning.
Making games is [not] hard. Looking back at small mobile project on Unity3D

Tips and tricks from my Telegram-channel @pythonetc, April 2019

It is a new selection of tips and tricks about Python and programming from my Telegram-channel @pythonetc.
Previous publications.
Practicalities of deploying dockerized ASP.NET Core application to Heroku
Intro
.NET is a relative newcomer in the open-source world, and its popularity is nowhere near mainstream platforms like Node.js. So you can imagine there're few tutorials that deal with .NET and frameworks such as ASP.NET on Heroku. And those that do, probably won't use containers.
Do you see C#/.NET here? Yes, me neither.
Citymobil — a manual for improving availability amid business growth for startups. Part 4

This is the next article of the series describing how we’re increasing our service availability in Citymobil (you can read the previous parts here: part 1, part 2, part 3). In further parts, I’ll talk about the accidents and outages in detail.
1. Bad release: database overload
Let me begin with a specific example of this type of outage. We deployed an optimization: added USE INDEX in an SQL query; during testing as well as in production, it sped up short queries, but the long ones — slowed down. The long queries slowdown was only noticed in production. As a result, a lot of long parallel queries caused the database to be down for an hour. We thoroughly studied the way USE INDEX worked; we described it in the Do’s and Dont’s file and warned the engineers against the incorrect usage. We also analyzed the query and realized that it retrieves mostly historical data and, therefore, can be run on a separate replica for historical requests. Even if this replica goes down due to an overload, the business will keep running.
Legacy Outage
Right at the beginning, we need to outline a couple of details for our readers:
- All Autonomous System Numbers under 1000 are called “lower ASNs,” as they are the first autonomous systems on the Internet, registered by IANA in the early days (the late 80’s) of the global network. Today they mostly represent government departments and organizations, that were somehow involved in Internet research and creation in 70-90s.
- Our readers should remember, that the Internet became public only after the United States’ Department of Defense, which funded the initial ARPANET, handed it over to the Defense Communication Agency and, later in 1981, connected it to the CSNET with the TCP (RFC675)/IP (RFC791) over X.25. A couple of years later, in 1986, NSF swapped the CSNET in favor of NSFNET, which grew so fast it made possible ARPANET decommission by 1990.
- IANA was established in 1988, and supposedly at that time, existing ASNs were registered by the RIRs. It is no surprise that the organization that funded the initial research and creation of the ARPANET, further transferring it to another department because of its operational size and growth, only after diversifying it into 4 different networks (Wiki mentions MILNET, NIPRNET, SIPRNET and JWICS, above which the military-only NIPRNET did not have controlled security gateways to the public Internet).
How to create a dark theme without breaking things: learning with the Yandex Mail team
My name is Vladimir, and I develop mobile front-end for Yandex Mail. Our apps have had a dark theme for a while, but it was incomplete: only the interface and plain emails were dark. Messages with custom formatting remained light and stood out against the dark interface, hurting our users’ eyes at night.
Today I'll tell you how we fixed this problem. You will learn about two simple techniques that didn't work for us and the method that finally did the trick — adaptive page recoloring. I'll also share some ideas about adapting images to a dark theme. To be fair, darkening pages with custom CSS is a rather peculiar task, but I believe some of you may find our experience helpful.
Google News and Leo Tolstoy: visualizing Word2Vec word embeddings using t-SNE
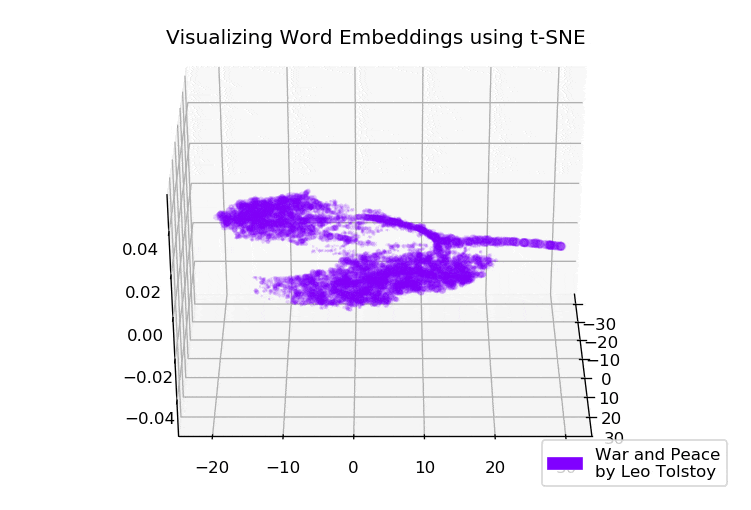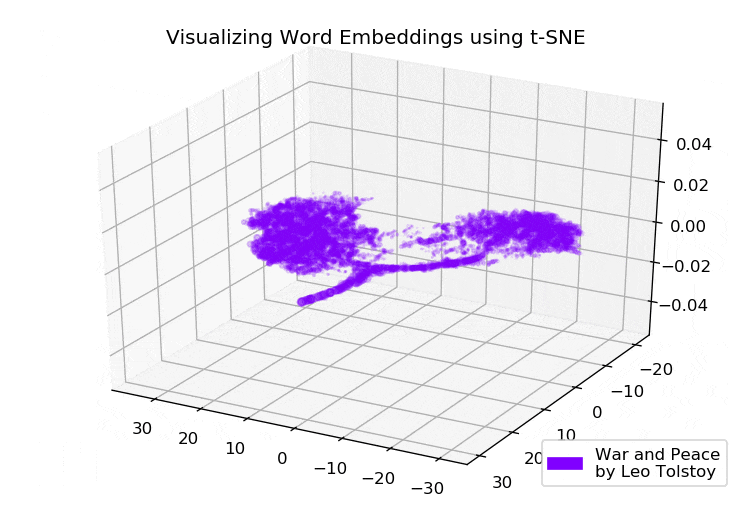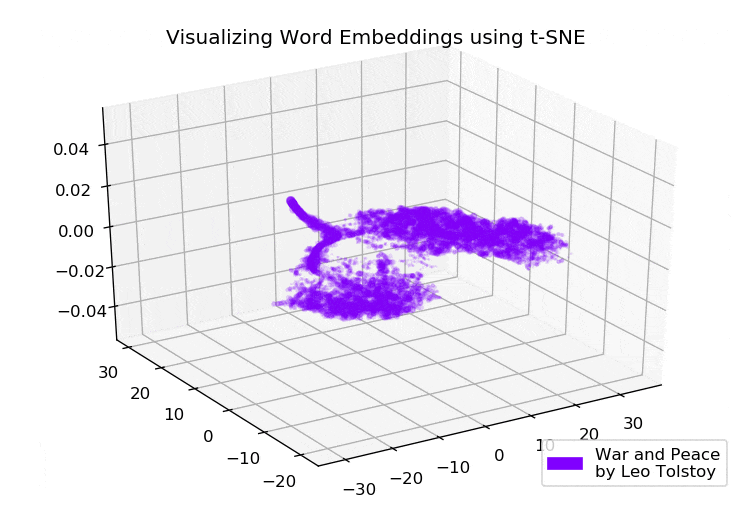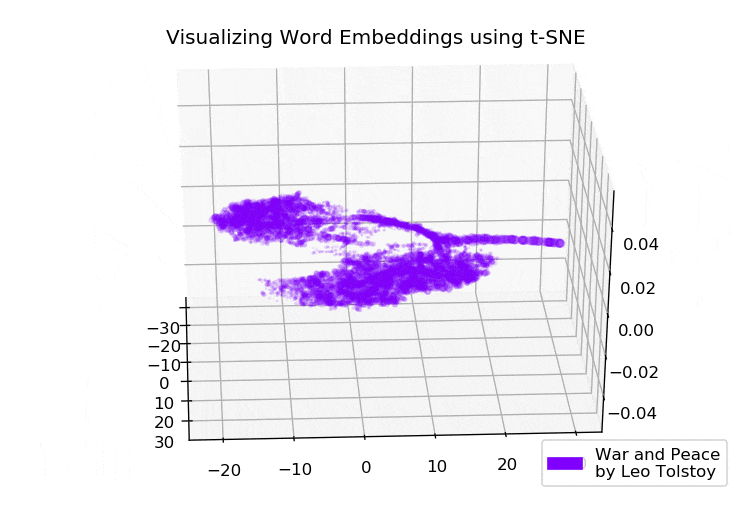
Everyone uniquely perceives texts, regardless of whether this person reads news on the Internet or world-known classic novels. This also applies to a variety of algorithms and machine learning techniques, which understand texts in a more mathematical way, namely, using high-dimensional vector space.
This article is devoted to visualizing high-dimensional Word2Vec word embeddings using t-SNE. The visualization can be useful to understand how Word2Vec works and how to interpret relations between vectors captured from your texts before using them in neural networks or other machine learning algorithms. As training data, we will use articles from Google News and classical literary works by Leo Tolstoy, the Russian writer who is regarded as one of the greatest authors of all time.
We go through the brief overview of t-SNE algorithm, then move to word embeddings calculation using Word2Vec, and finally, proceed to word vectors visualization with t-SNE in 2D and 3D space. We will write our scripts in Python using Jupyter Notebook.
Finding Bugs in LLVM 8 with PVS-Studio
It's been two years since we last checked the code of the LLVM project with PVS-Studio, so let's see if PVS-Studio is still the leader among tools for detecting bugs and security weaknesses. We'll do that by scanning the LLVM 8.0.0 release for new bugs.
NodeMCU simple driver model (SDM) showcase: dynamic user interface
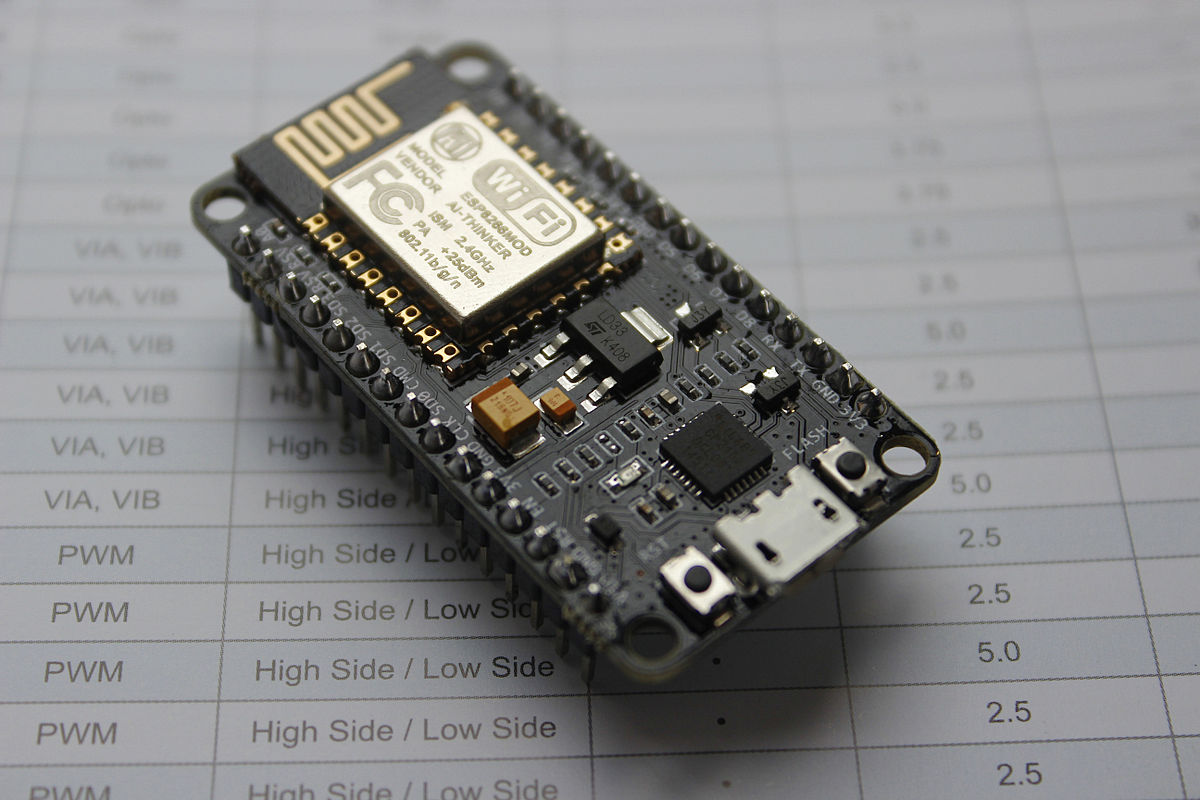
NodeMCU is an interactive firmware, which allows running Lua interpreter on the ESP8266 microcontroller (ESP32 support is in development). Alongside with all the regular hardware interfaces, it has WiFi module and SPIFFS file system.
This article describes the new module for the NodeMCU — sdm. SDM stands for simple driver model and it provides device-driver model abstraction for the system. In the first part of this article we will discuss the model itself and in the second part will be a showcase of dynamically created web user interface using sdm with some commentaries.
Citymobil — a manual for improving availability amid business growth for startups. Part 3

This is the next article of the series describing how we’re increasing our service availability in Citymobil (you can read the previous parts here and here). In further parts, I’ll talk about the accidents and outages in detail. But first let me highlight something I should’ve talked about in the first article but didn’t. I found out about it from my readers’ feedback. This article gives me a chance to fix this annoying shortcoming.
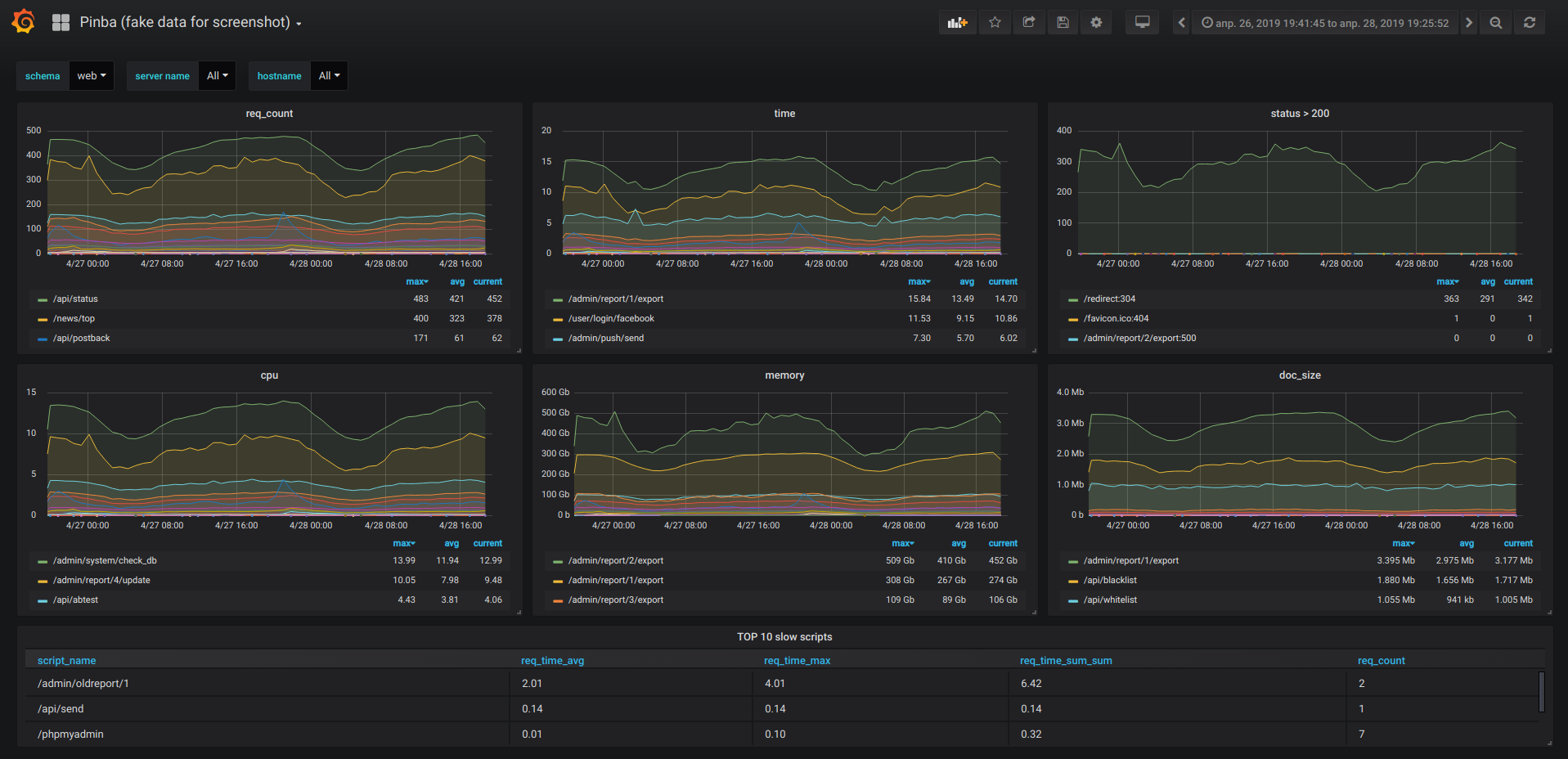
Statistics and monitoring of PHP scripts in real time. ClickHouse and Grafana go to Pinba for help
On the php project pinba is probably the only reliable way to understand what is happening with performance. But usually people start to use pinba only when problems are already observed and it isn't clear where to look in.
Often developers have no idea how many RPS each script has. So they begin to optimize starting from places that seem to have problem.
Someone is analyzing the nginx logs, and someone is slow queries in the database.
Of course pinba would not be superfluous, but there are several reasons why it is not on every project.