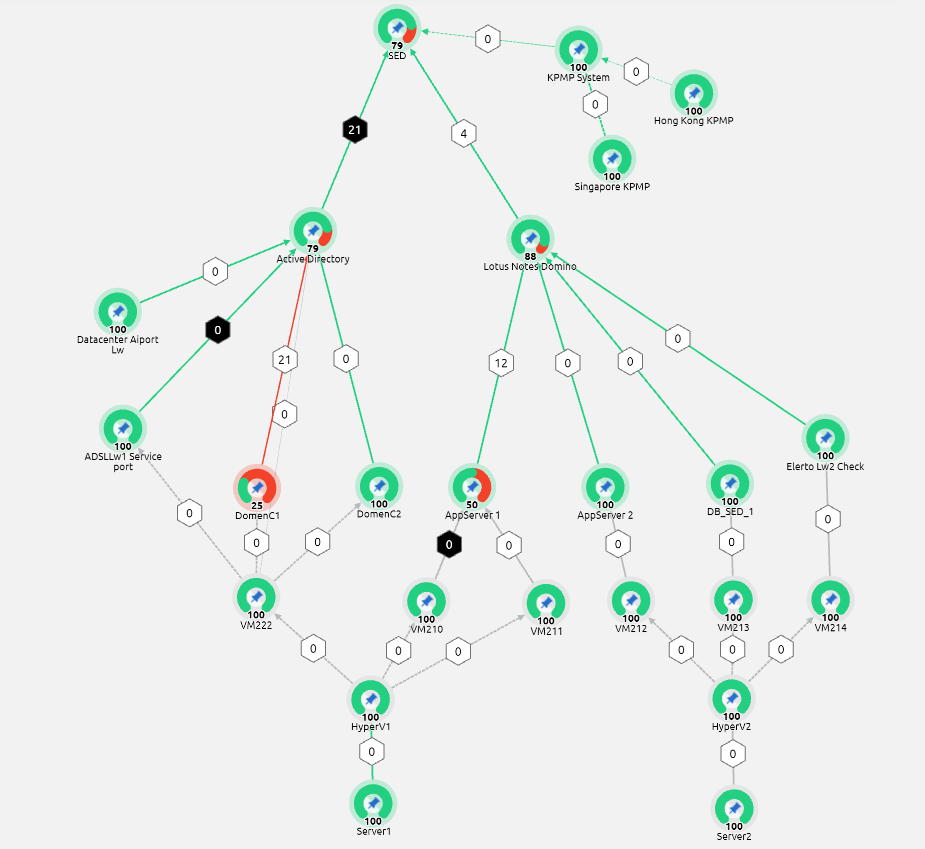
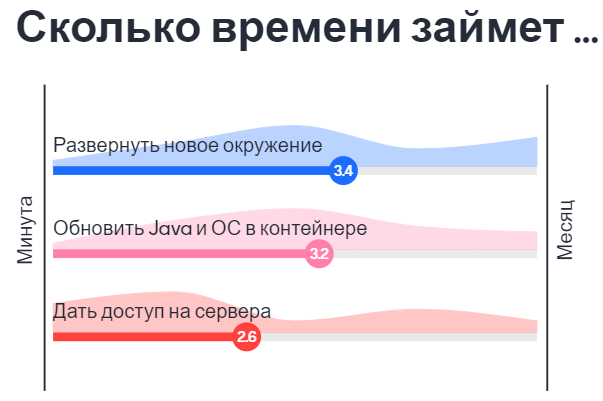
We all strive to build better software, and to do it faster. I believe Test-driven Development offers us a path towards this goal. Still struggling to efficiently utilize this approach? Then I invite you to discuss my tips and tricks to unlock the benefits of TDD!