Title:
After sale IT support for American and Western Companies
Let’s have a case study.
A Russian IT company sells software to a western country like say America. And you are working as an application developer on the support side.
One day, there is a problem with the program, and the program has stopped working.
You must contact the company now to inform them that the program is off-line.
THE NEXT STEP YOU TAKE IS VERY IMPORTANT.
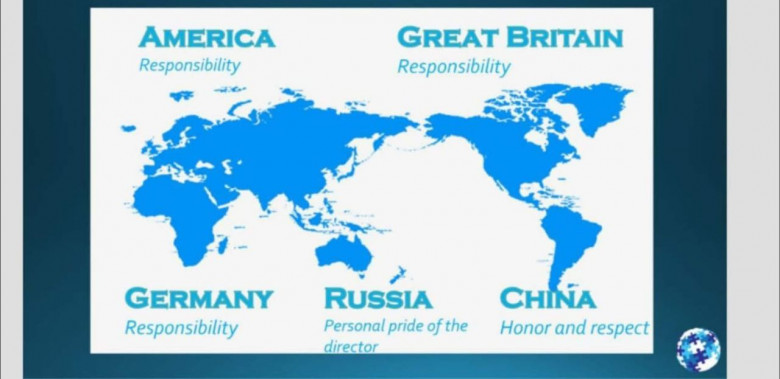
The way, the two cultures operate in a situation like this are very different and it will have everything to do with how easy your job goes for you.
…………
Russia : “we have a problem”
“What is wrong?”
“I don’t know”
“When can it be fixed?”
“I don’t know”
……………
USA: “i’m just giving you a real quick call to let you know that there is a problem with the program.
I’ve already put my team on it and we will have it up and running shortly.
I will let you know more by 3 o’clock today what is going on”
It’s not important how long you think it will take you, but I will always tell them a few hours from the time that you informed them of a problem.
I understand that you have no idea how deep the bug is and also whether it will affect any other systems.
But it is important to set a time window very close to when you inform them that you will bring them more information.
This also works very well if you don’t know something that they ask you.
Question:
“What can we do to fix this problem?”
Answer:
“I understand what you’re saying. I will look into it and get back to you in two hours. By 1 PM today.”
in this case, it’s important that you:
1. Take responsibility for yourself and your team.
2. Communicate that you understand this responsibility.
3. Gives strict timelines. (if it’s not possible, you can always say that there is a problem, but do it before the deadline.)
4. Use certain key language.
“ I understand you”
“ I understand what you were saying”
“ I wanted to inform you”
“ we are working on it right now”