Чем плох свой Open Source проект
К тому же потом можно мерятся количеством коммитов в rails и зарплату попросить побольше.
А что если вы решили написать свой open source проект?

История сия произошла в начале семидесятых годов прошлого века. Она наверняка тянет на сюжет крутого боевика, поскольку в ней присутствуют и засыпанный сибирскими снегами Вычислительный Центр и специальная бригада сотрудников КГБ во главе с майором и роскошная блондинка, которая разделась донага ради раскрытия большой тайны. Будут в этой истории допрос и обыск а также арест невиновного. А арестованным невиновным окажется сам автор.
Если интересно и есть время - читайте дальше.

Удивительно, но новость из заголовка сообщество почему-то обошло стороной, либо вокруг неё не было особого обсуждения, что достаточно странно, учитывая традиционную заинтересованность аудитории микроэлектроникой. Что ж, давайте восполним этот пробел. Если вам просто интересен вопрос, или же вы специалист и вам есть что сказать - так или иначе добро пожаловать под кат.
Ведь где иначе искать истины в этом вопросе, как не на Хабре...
Здравствуйте, уважаемые читатели!
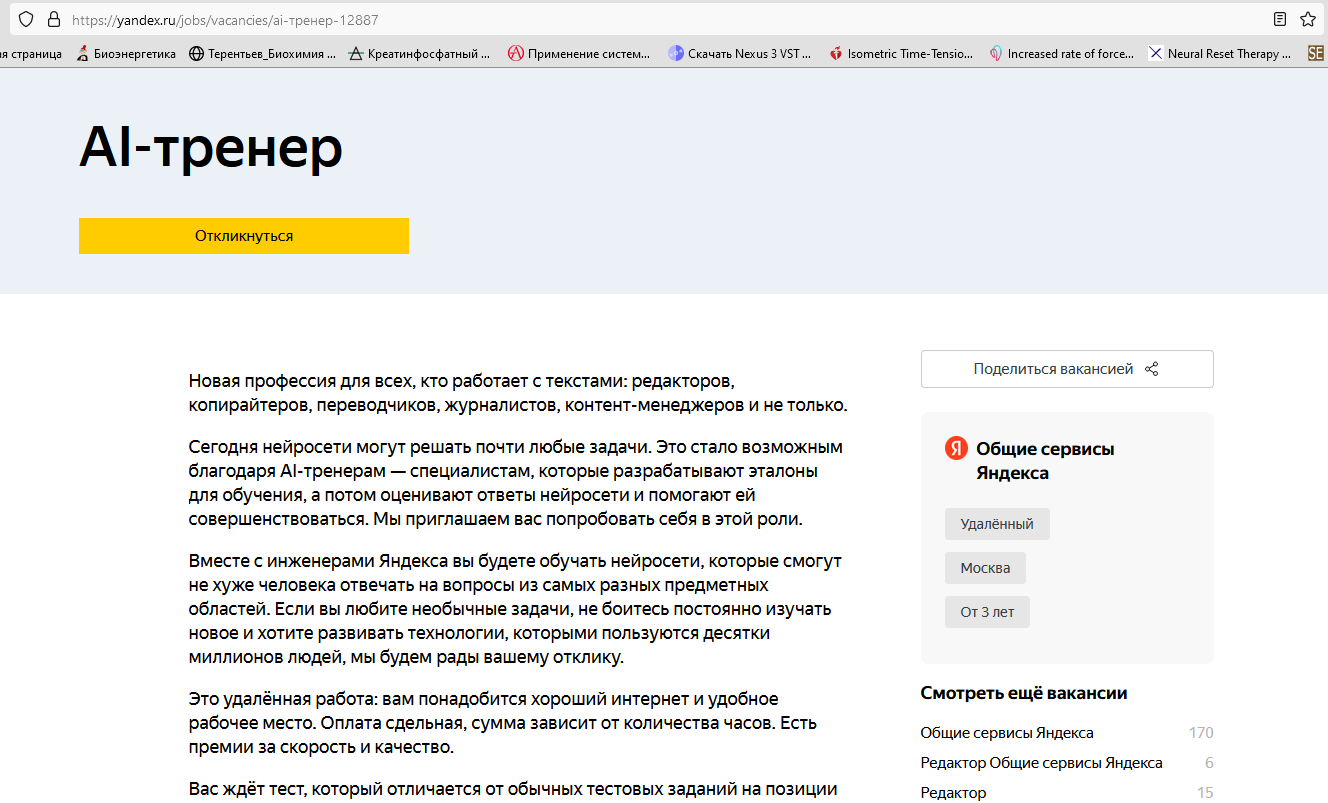
Тема сегодняшней статьи будет несколько нестандартная, однако, безусловно связанная с информационными технологиями, нейросетями и технологическим гигантом нашего времени – компанией Яндекс.
Сразу хочу отметить – я отлично осознаю факт того, что Хабр не является площадкой для сведения счетов, размещения жалоб или ломания копий. И идея о том, чтобы написать свой отзыв об опыте общения с компанией Яндекс так и осталась бы идеей, лежащей где-то чуть ли не на дальней полочке в моем мозге, если бы буквально на днях, 18.01.2024 г., спустя 5 месяцев после того, как поступили со мной, я не увидел полностью аналогичный случай, о котором написали в сети. См. ссылку ниже:
https://journal.tinkoff.ru/kak-ia-pytalas-ustroitsia-na-rabotu-v-iandeks/
Прочитав пост, я понял, что эпопея “Яндекс-швырялово” длится уже около полугода и при этом все её организаторы чувствуют себя предельно комфортно, поэтому я был просто вынужден расчехлить перо.


Аббревиатура OFDM расшифровывается как Orthogonal frequency-division multiplexing. В русскоязычной литературе встречается несколько различных переводов, несущих, в принципе, один смысл: OFDM — это механизм мультиплексирования (уплотнения) посредством ортогональных поднесущих.
В статье описаны плюсы и минусы механизма OFDM. Рассмотрен принцип функционирования с физико-математической позиции. Статья содержит вводное описание радиофизических терминов, необходимых для понимания материала широкому кругу читателей.

Иллюстраций: 18, символов: 27 399, строк кода: 99.
<img src="http://placehold.it/350x50" />и получаете:

Начну с истории вопроса.
Очень давно я написал Fresh IDE – навороченнoe IDE для программирования на ассемблере, а точнее на FlatAssembler.
Fresh IDE долгие годы меня полностью устраивал, поэтому я с перерывами выпустил 2 главные версии и начал просто его использовать, время от времени внося какие-то исправления и изредка новые функции.
Когда перешел полностью на Linux, оказалось, что Fresh IDE прекрасно работает под WINE, и я продолжил им пользоваться без угрызений совести. В процессе даже удалось исправить несколько багов WINE (вот, вот и вот).
Как бы то ни было, но я начал писать библиотеку для переносимости ассемблерных программ между Linux и Windows (и KolibriOS). Одновременно с этим задумался и над тем, чтобы сделать Fresh IDE переносимым. Из-за архитектуры библиотеки, огромная часть кода уже и так была переносимой. А точнее все, что не касалось GUI. К сожалению, GUI был полностью написан на Win32 API и его нельзя просто так перенести на другие платформы.
Поэтому и пришлось начинать все сначала. И третья версия Fresh IDE писалась почти с нуля.

Я люблю критику. Если вы не заметили, я, как старый дед, всё поливаю грязью и всем недоволен.
Забавно, но в то же время я люблю, когда критикуют меня самого, потому что именно в такие моменты я что-то начинаю понимать, развиваюсь и становлюсь лучше. А в этой статье я решил совместить приятное с забавным и рассказать вам о своих самых идиотских решениях и самых эпичных провалах за свою карьеру программиста - такая вот само-критика. Возможно, кто-то узнает себя, а если нет, то я просто прошу вас: не делайте так же, как делал я.
 В этой статье я расскажу об одном необычном подходе к генерации лабиринтов. Он основан на модели Амари́ нейронной активности коры головного мозга, являющейся непрерывным аналогом нейронных сетей. При определенных условиях она позволяет создавать красивые лабиринты очень сложной формы, подобные тому, что приведен на картинке.
В этой статье я расскажу об одном необычном подходе к генерации лабиринтов. Он основан на модели Амари́ нейронной активности коры головного мозга, являющейся непрерывным аналогом нейронных сетей. При определенных условиях она позволяет создавать красивые лабиринты очень сложной формы, подобные тому, что приведен на картинке. Недавно на Хабре была опубликована статья под провокационным заголовком и призывом к прекращению изобретений велосипедов в API-строении. Поскольку тема мне интересна, то я просто не мог пройти мимо.
Недавно на Хабре была опубликована статья под провокационным заголовком и призывом к прекращению изобретений велосипедов в API-строении. Поскольку тема мне интересна, то я просто не мог пройти мимо.