The last decades the world economy regularly falls into this vortex of financial crises that have affected each country. It almost led to the collapse of the existing financial system, due to this fact, experts in mathematical and economic modelling have become to use methods for controlling the losses of the asset and portfolio in the financial world (Lechner, L. A., and Ovaert, T. C. (2010). There is an increasing trend towards mathematical modelling of an economic process to predict the market behaviour and an assessment of its sustainability (ibid). Having without necessary attention to control and assess properly threats, everybody understands that it is able to trigger tremendous cost in the development of the organisation or even go bankrupt.
Value at Risk (VaR) has eventually been a regular approach to catch the risk among institutions in the finance sector and its regulator (Engle, R., and Manganelli S., 2004). The model is originally applied to estimate the loss value in the investment portfolio within a given period of time as well as at a given probability of occurrence. Besides the fact of using VaR in the financial sector, there are a lot of examples of estimation of value at risk in different area such as anticipating the medical staff to develop the healthcare resource management Zinouri, N. (2016). Despite its applied primitiveness in a real experiment, the model consists of drawbacks in evaluation, (ibid).
The goal of the report is a description of the existing VaR model including one of its upgrade versions, namely, Conditional Value at Risk (CVaR). In the next section and section 3, the evaluation algorithm and testing of the model are explained. For a vivid illustration, the expected loss is estimated on the asset of one of the Kazakhstani company trading in the financial stock exchange market in a long time period. The final sections 4 and 5 discuss and demonstrate the findings of the research work.



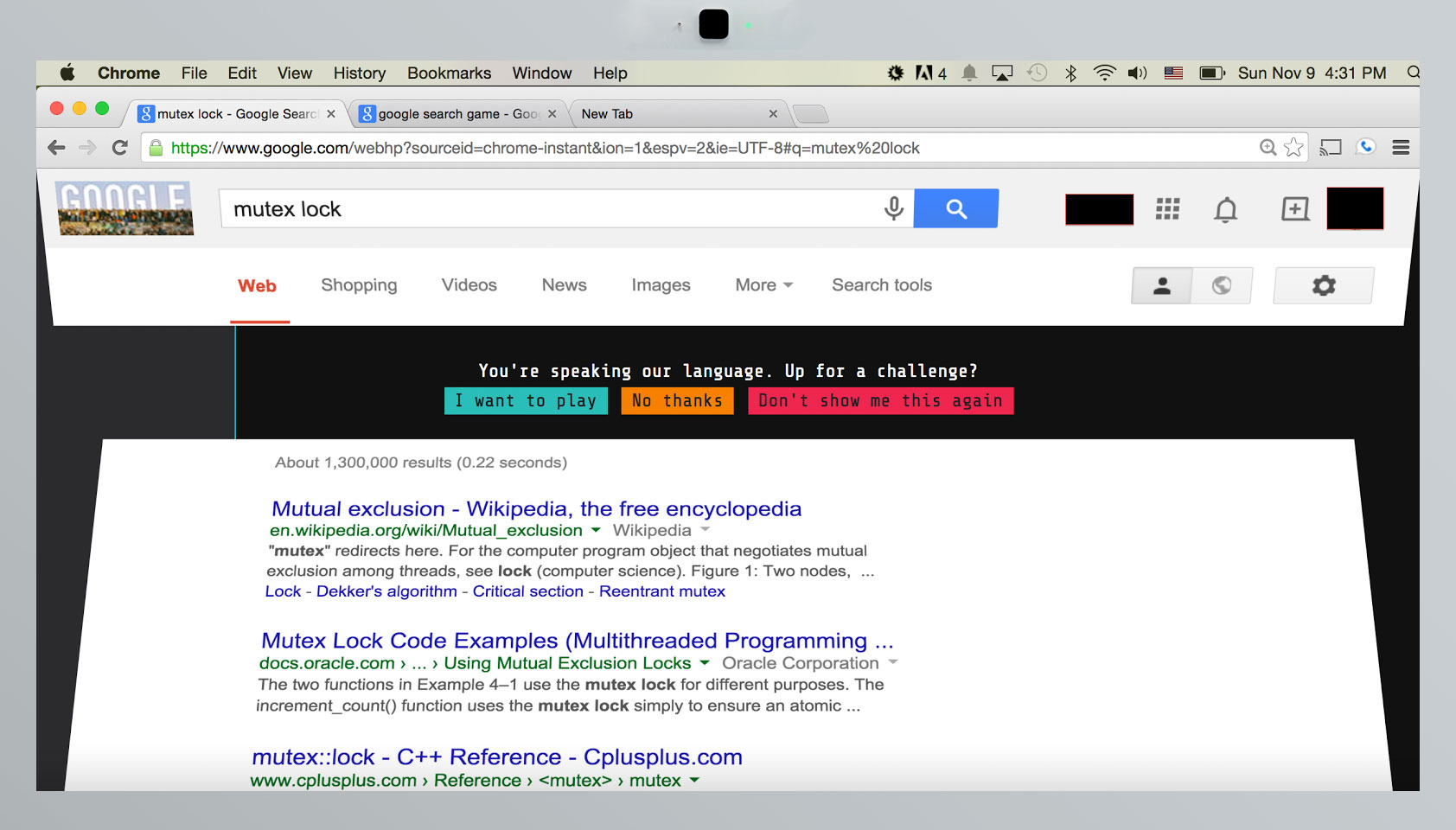
 Google loves easter eggs. It loves them so much, in fact, that you could find them in virtually every product of theirs. The tradition of Android easter eggs began in the very earliest versions of the OS (I think everyone there knows what happens when you go into the general settings and tap the version number a few times).
Google loves easter eggs. It loves them so much, in fact, that you could find them in virtually every product of theirs. The tradition of Android easter eggs began in the very earliest versions of the OS (I think everyone there knows what happens when you go into the general settings and tap the version number a few times).