This is one of the most important articles I’ve written.
In this article, I’m going to dive deep into one of the largest differences between Russia and America pertaining to sales and marketing.
1. You must use your name.
2. You must have a personal approach.
3. You must show that you are involved.
4. You must show that you care about the needs and desires of the client.
Recently, I was faced with an interesting problem. I was asked to call clients without making it personal.
So let’s go back to when I was in America, living and working as a sales person. The company I work for, was very large, and had multiple branches around the Washington DC area. They had offices in three states.
They put me through a sales training course.
The biggest “take away” from the course…..
You’re not selling the product/
you’re selling yourself.
It's important to use your charisma and your genuine caring for the customer to win them over. Once they understand that you're actually trying to help them, then they will seriously consider the item you are telling them about.
I also want to say, very clearly, that it's not a prideful approach. It should be a professional approach. You're responsible to tell the customer/ the client all the benefits of the item and how this item will help their business.
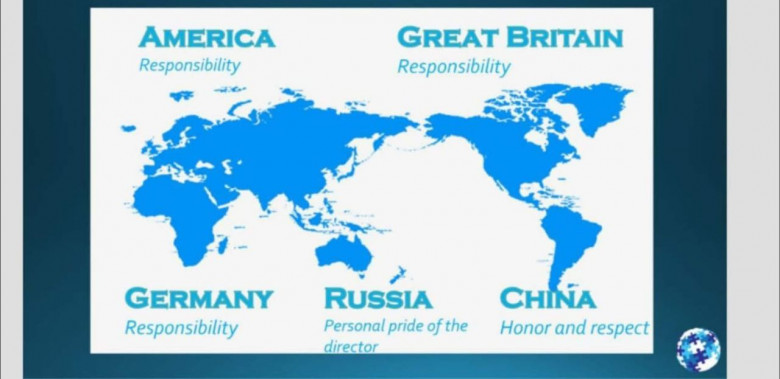
Everything above pertains to sales in America. So if you are approaching America as a sales manager this is how you should craft your approach.
Now I've spoken to my colleague,
Kristina Pashnina and we have agreed upon some stark differences to the Russian sales climate. Here she will begin to tell you how the Russians see sales.