What Are Coin Features in Short Video Apps and How Do They Work?

Discover what coin features are in short video apps, how they work, and how users earn rewards. Learn how coin systems boost engagement and monetization in 2025.

Everything about software

Discover what coin features are in short video apps, how they work, and how users earn rewards. Learn how coin systems boost engagement and monetization in 2025.

Short video apps have completely reshaped how people consume entertainment. Instead of sitting down for a two-hour movie or a 45-minute TV episode, viewers are now hooked on bite-sized videos that fit into their busy schedules. This shift has been accelerated by Gen Z and Millennials, who prefer quick storytelling formats that are both interactive and engaging.
In 2025, the OTT and short video industry is projected to see over 1.5 billion monthly active users worldwide, with an average revenue per user (ARPU) of nearly $12. The reasons are clear: affordability, accessibility, and convenience. The success of apps like DramaBox shows that people are willing to spend money on shorter dramas as long as they deliver strong storytelling.
For entrepreneurs, this presents a golden opportunity to build OTT platforms like DramaBox and tap into this global demand.

This article presents a business-driven approach to software architecture, focusing on maximizing profitability through technical decisions. It advocates for:
Distributed, stateless services with immutable models for scalability
Isolated third-party integrations without disrupting core logic
Simple, modular design
Best for:
✔ Tech leads designing scalable systems
✔ Managers optimizing dev efficiency
✔ Stakeholders evaluating ROI on architecture
There was already news on Habr about this significant event. Indeed, it resembles a retelling of the official Microsoft press release, but that's how the 'news' should be.
Surprisingly, there are strict mathematical methods that literally allow to hear visual geometric forms and, conversely, to see the beauty of musical harmonies...
Referential transparency, a key concept in functional programming, is often associated with more reliable, easier to test, and safer software. This term refers to a principle in which a function, given the same input, will always produce the same output without producing any side effects.
In the real world of software development, side effects are inevitable. Programs are rarely useful unless they interact with the outside world. This interaction could be reading from or writing to the console, making network requests, querying a database, or modifying a variable.
Yet, despite the necessity of side effects, they introduce risks and complexities. Programs with side effects are harder to test, harder to reason about, and more prone to bugs. They can also make the system as a whole more difficult to understand and maintain, due to hidden dependencies between components.
Enter referential transparency - a concept that means a function, given the same input, will always provide the same output, without creating any side effects. A function that adheres to this principle doesn't read any global state or change any state outside of its scope. The result is code that is more predictable and easier to reason about.
In terms of software safety and reliability, the absence of side effects is not enough. Programs should also be free from external influence - their results should only depend on their arguments. That is, programs should not read data from the console, a file, network, database, or even system variables.

As a product owner, it is common to face the question of whether to proceed with option A or option B. Or, which version of the screen should be implemented to achieve better results? Making such decisions can be challenging, especially when you are under tight deadlines with limited resources. Furthermore, such decisions are made based on personal judgment or copying the approach of a competitor, which can lead to suboptimal results.
The good news is that one can avoid such pitfalls by setting up a simple experiment environment that requires relatively low effort. In this article, we will describe how you can achieve this.

I believe listicles have a huge potential for testing demand hypotheses. Have you tried using listicles for your demand validation? If so - let us know in the comments how this worked for you.
Do you know these "Top N something something" kind of articles? Like:
- 5 best GPS vehicle trackers
- The 14 hair growth products that actually work
- Top 10 Best CRM Software Tools in 2023
They are often referred to as "listicles" - articles presented in the form of a list.
I love them - they make picking a new phone, a movie to watch, an app to install much easier. I also use them at work all the time while looking for solutions to everyday challenges.
So what if we use one of them to benchmark our product against the best available alternatives?
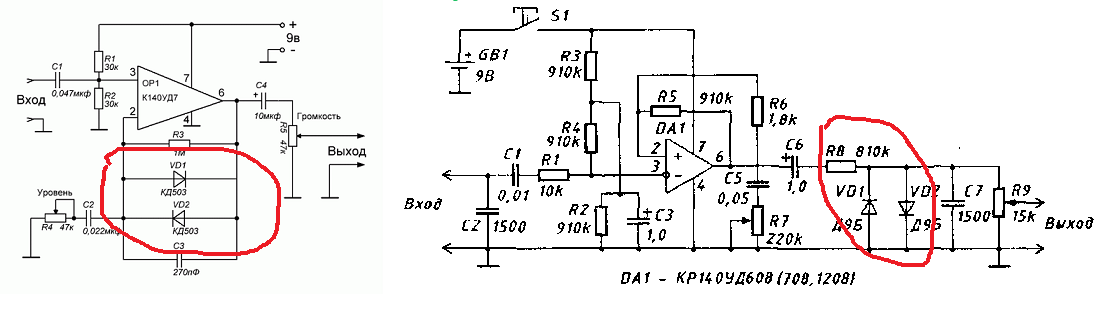
The sound of rock music, in particular of hard rock and heavy metal, is largely based on a specially distorted guitar sound, for which electronic “distortion” devices, tube amplifiers in “overloaded” mode, computers with appropriate software and digital processors are used. increasingly using neural network algorithms.
The distorted sound of electric guitars began to gain popularity around the 1960s. Since that time, the sound of overloaded tube amplifiers, connected to powerful dedicated guitar speakers with large dedicated speakers, has been considered the benchmark in rock music. But tube amplifiers were relatively expensive and inconvenient to operate. Therefore, semiconductor distortion devices were developed.
At that time, the electrical circuitry of distortion devices was relatively simple and the signal output from their output only vaguely resembled the sound of an overloaded tube amplifier. Nevertheless, it was still somewhat similar to the “sound of a lamp” and this provided a powerful incentive for designers of analog semiconductor distortion circuits to continue their research, complicate circuits and propose new circuit solutions. The heyday of analog solid-state distortion was around 1995-2010. The most popular were electrical circuit diagrams like those shown in the figure below.

e-Learning is an extension of/ alternative to a traditional classroom setup. e-learning, commonly known as ‘online learning’ or ‘virtual learning’ is ideally a one-way or two-way digital communication established on a device with video and voice call integration using internet access. The last two years made us realize how technology can facilitate and improve communication. Digital technology had its impact in almost every industry including the sensitive education sector.

In-app messages are targeted notifications sent to customers/ users while they are active on the website or mobile application. They are a very effective way to engage customers as they are already within the application looking for specific information. In-app chat applications help connect better with the users and improve user retention as they are timely and targeted.

Sometimes all of us need to make a graphical installer for one's own linux distro. It goes without saying that you are able to use a distro-specific installer like Anaconda for RedHat-based or DebianInstaller for debian-based. On the other hand Calamares is a graphical installer which is not aligned with only one package manager.
I want to share my experience how to make a universal install solution with GUI. I did not find any complete article about it, hence, I reinvented the wheel.

I reinstalled both Windows and Linux (Fedora) recently on a notebook PC, and I decided to write the summary article about my experience with both OS. I'm also going to describe how to configure each OS via command-line and set up a dual-boot system.
Tools to improve and control code quality can be a key success factor in a complex software project implementation. Static analyzers belong to such tools. Nowadays, you can find various static analyzers: from free open-source to cross-functional commercial solutions. On the one hand, it's great – you can choose from many options. On the other hand – you have to perform advanced research to find the right tool for your team.

These days, video streaming mobile apps have been witnessed with an increased spike of subscribers & now much video content is being much cherished without any interruptions via a streaming app.
This is duly because catering to the prerequisite needs of end-users have popularized several VOD streaming services that has bought keen interest as compared to to the big black box which is slowly diminishing its presence.
According to recent forecasted data, there is a positive anticipation of the entire VOD streaming platform development’s market to expand its size & peak its value by $842.93 billion by the year 2027! Source: Softermii

The previous year has been very distressing for businesses and employees. Though, software development didn’t get so much affected and is still thriving. While tech expansion is continuing, Java development is also going under significant transformation.
The arrival of new concepts and technologies has imposed a question mark on the potential of Java developers. From wearable applications to AI solutions, Java usage is a matter of concern for peers.
Moreover, it is high time that developers enhance their skills as to the changing demands of the industry. If you are a Java developer, surely you too would be wondering what I am talking about what things you should learn.

As we all are aware of the fact that the digital market is heavily leaning towards a reliable UX-driven process, app development has become quite complex, especially for targeting the industry for mobile platforms.
For every organization, creating a product that is beneficial for their customer needs always comes up with a plethora of challenges.
From the technical point of time, there are various challenges that every business faces, including selecting the right platform for the app, the right technology stack or framework, and creating an app that fulfills the needs and expectations of customers.
Similarly, there are more challenges that every business faces and needs to cope with while creating its dream product.
So, what to do??
Well, what if I say that the answer to all your queries and questions is Flutter app development with Artificial Intelligence (AI) integration……
Surprised? Wondering how?
Well, AI in Flutter app development is one of the best advancements in the software market. The concept of AI was first introduced during the 20th century with loads of innovations and advancements that we are still integrating into our mobile app development.
But, what are Artificial Intelligence and Flutter app development?
This article is about security. I’ll focus on this in the context of web applications, but I’ll also touch on other types of applications. Before I describe approaches and frameworks, I want to tell you a story.
Throughout my years working in the IT sphere, I’ve had the opportunity to work on projects in a variety of fields. Even though the process of authenticating requirements remained relatively consistent, methods of implementing the authorization mechanism tended to be quite different from project to project. Authorization had to be written practically from scratch for the specific goals of each project; we had to develop an architectural solution, then modify it with changing requirements, test it, etc. All this was considered a common process that developers could not avoid. Every time someone implemented a new architectural approach, we felt more and more that we should come up with a general approach that would cover the main authorization tasks and (most importantly) could be reused on other applications. This article takes a look at a generalized architectural approach to authorization based on an example of a developed framework.
As usual, before developing something new, we need to decide what problems we’re trying to solve, how the framework will help us solve them, and whether or not there is already a solution to these issues. I’ll walk you through each step, starting with identifying issues and describing our desired solution.
We’re focusing on two styles of coding: imperative and declarative. Imperative style is about how to get a result; declarative is about what you want to get as a result.
