Setting up Atom for working with python is quite a tricky task. I've spent a lot of time making it work. Autocompleting, autoformatting, type hints, and much more will be available to you after reading this tutorial.

Setting up Atom for working with python is quite a tricky task. I've spent a lot of time making it work. Autocompleting, autoformatting, type hints, and much more will be available to you after reading this tutorial.
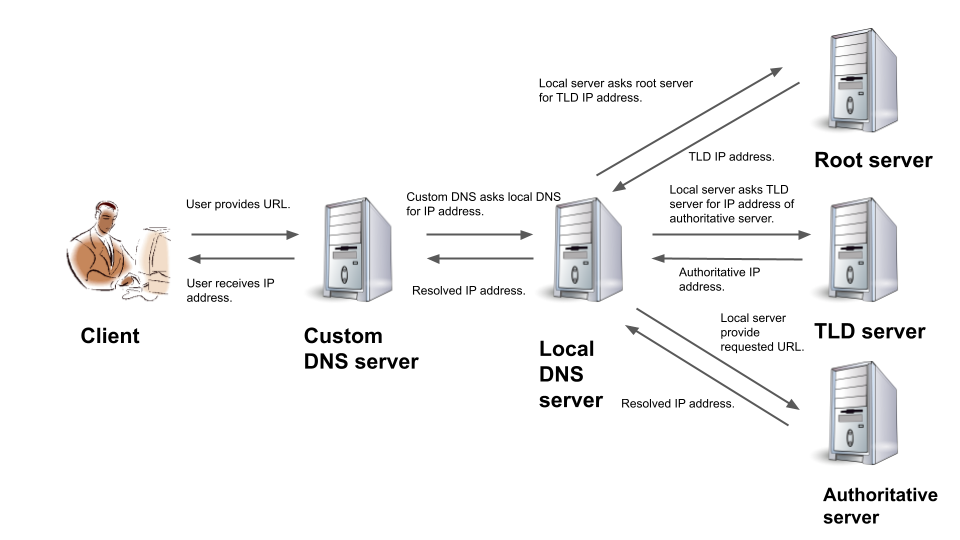
We describe the implementation of a custom Domain Name System (DNS) by using C socket programming for network communication, together with SQLite3 database for the storage of Internet Protocol (IP) for Uniform Resource Locator (URL). Then we provide a performance analysis of our implementation. Our code is available publicly [1].

Types of smart traffic lights: adaptive and neural networks
Adaptive works at relatively simple intersections, where the rules and possibilities for switching phases are quite obvious. Adaptive management is only applicable where there is no constant loading in all directions, otherwise it simply has nothing to adapt to – there are no free time windows. The first adaptive control intersections appeared in the United States in the early 70s of the last century. Unfortunately, they have reached Russia only now, their number according to some estimates does not exceed 3,000 in the country.
Neural networks – a higher level of traffic regulation. They take into account a lot of factors at once, which are not even always obvious. Their result is based on self-learning: the computer receives live data on the bandwidth and selects the maximum value by all possible algorithms, so that in total, as many vehicles as possible pass from all sides in a comfortable mode per unit of time. How this is done, usually programmers answer – we do not know, the neural network is a black box, but we will reveal the basic principles to you…
Adaptive traffic lights use, at least, leading companies in Russia, rather outdated technology for counting vehicles at intersections: physical sensors or video background detector. A capacitive sensor or an induction loop only sees the vehicle at the installation site-for a few meters, unless of course you spend millions on laying them along the entire length of the roadway. The video background detector shows only the filling of the roadway with vehicles relative to this roadway. The camera should clearly see this area, which is quite difficult at a long distance due to the perspective and is highly susceptible to atmospheric interference: even a light snowstorm will be diagnosed as the presence of traffic – the background video detector does not distinguish the type of detection.

Let's say you use GitHub, write code, and do other fun stuff. You also use a static analyzer to enhance your work quality and optimize the timing. Once you come up with an idea - why not view the errors that the analyzer gave right in GitHub? Yeah, and also it would be great if it looked nice. So, what should you do? The answer is very simple. SARIF is right for you. This article will cover what SARIF is and how to set it up. Enjoy the reading!

Speech analytics is the process of analysing recorded speech, such as phone calls, to gather customer information to improve communication and future customer interaction. Speech analytics as a technology has been evolving especially rapidly over the last few years. It gives the ability to structure and analyse previously lost streams of insight-rich data, such as phone conversations. Empowered with this technology, operations can gather incredibly valuable business intelligence to drive call delivery performance improvements. It’s smart in that it automatically identifies focus areas in which customer service or sales teams may need additional call training which then, in turn, improves the call’s successful outcome. Speech analytics, as a process, can isolate buzzwords and phrases used most frequently within a given time period, plus indicate usage is trending up or down. This data is highly useful to call managers to spot changes in consumer behaviour so that action can be taken to improve customer satisfaction.
Zadarma is a leading global VoIP provider and offers a smart speech analytics feature as part of their incredibly easy to use telecommunications offering. The tool is free as part of the wider PBX phone system bundles, included in the free recognition minutes. Zadarma’s analytics feature allows data access to every internal or external call conversation. The benefits of speech analytics include:
Before we start, I'd like to get on the same page with you. So, could you please answer? How much time will it take to:
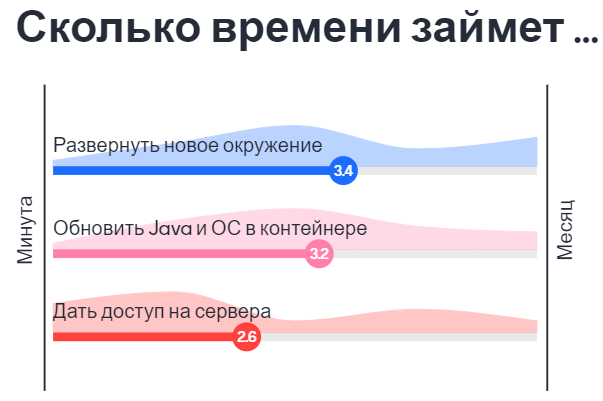
It will take longer than you expect. I will explain why.


Academic data warehouse design recommends keeping everything in a normalized form, with links between. Then the roll forward of changes in relational math will provide a reliable repository with transaction support. Atomicity, Consistency, Isolation, Durability — that's all. In other words, the storage is explicitly built to safely update the data. But it is not optimal for searching, especially with a broad gesture on the tables and fields. We need indices, a lot of indices! Volumes expand, recording slows down. SQL LIKE can not be indexed, and JOIN GROUP BY sends us to meditate in the query planner.


There was a custom configuration management solution.
I would like to share the story about a project. The project used to use a custom configuration management solution. Migration lasted 18 months. You can ask me 'Why?'. There are some answers below about changing processes, agreements and workflows.

It is the translation of my speech at DevOps-40 2020-03-18:
After the second commit, each code becomes legacy. It happens because the original ideas do not meet actual requirements for the system. It is not bad or good thing. It is the nature of infrastructure & agreements between people. Refactoring should align requirements & actual state. Let me call it Infrastructure as Code refactoring.
Scientists said they were able to return the state of a quantum computer a fraction of a second into the past, according to a university press release. The researchers, who are from the Moscow Institute of Physics and Technology, along with colleagues from the U.S. and Switzerland, also calculated the probability that an electron in empty interstellar space will spontaneously travel back into its recent past. The study came out recently in Scientific Reports.“This is one in a series of papers on the possibility of violating the second law of thermodynamics. That law is closely related to the notion of the arrow of time that posits the one-way direction of time: from the past to the future,” commented the study’s lead author Gordey Lesovik, who heads the Laboratory of the Physics of Quantum Information Technology at MIPT.
This is small cross-platform linux-distro with zabbix server. It's a simple way to deploy powerful monitoring system on ARM platfornms and x86_64.
Worked as firmware (non-changeable systemd image with config files), have web-interface for system management like network settings, password and other.