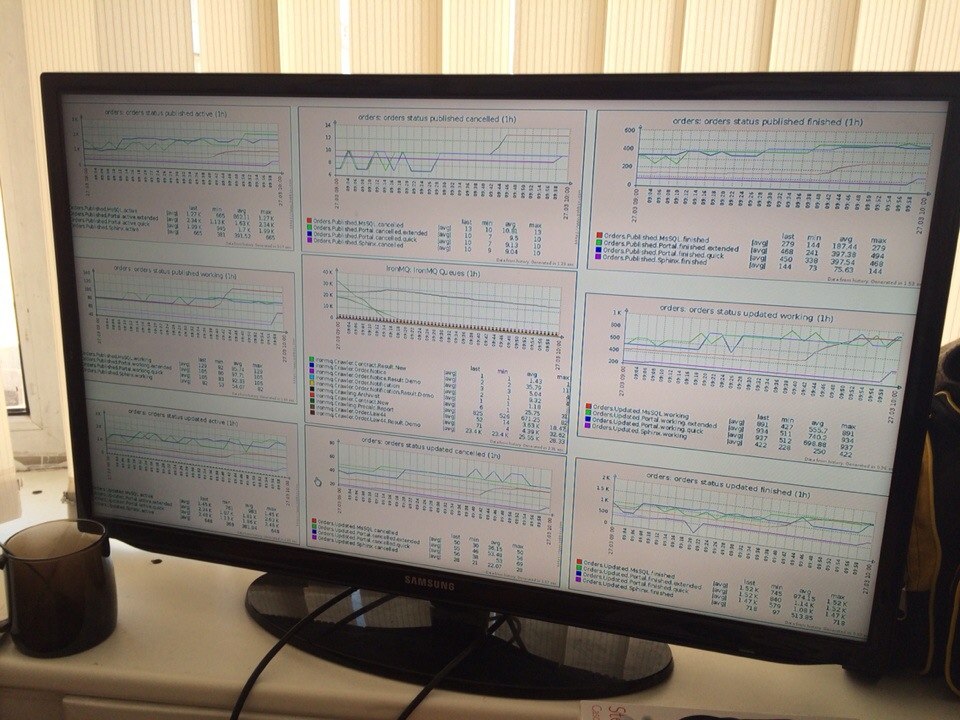
This world needs a new theory — a theory that could describe all the theories on the planet. A theory that could easily describe philosophy, mathematics, physics, and psychology. The one that makes all kinds of sciences computable.
This is exactly what we are working on. If we succeed, this theory will become the unified meta-theory of everything.
A year has passed since our last publication, and our task is to share the progress with our English-speaking audience. This is still not a stable version; it’s a draft. Therefore, we welcome any feedback, as well as your participation in the development of the links theory.
As with everything we have done before, the links theory is published and released into the public domain — it belongs to humanity, that means, it is yours. This work has many authors, but the work itself is far more important than any specific authorship. We hope that today it can become useful to more people.
We invite you to become a part of this exciting adventure.


 A few months ago I worked with a customer on how a team should evaluate the security of their Azure implementation. I had never done a
A few months ago I worked with a customer on how a team should evaluate the security of their Azure implementation. I had never done a