
The second quarter of the year has ended and, as usual, we take a look back at the mitigated DDoS attacks activity and BGP incidents that occurred between April and June 2022.

Data protection

The second quarter of the year has ended and, as usual, we take a look back at the mitigated DDoS attacks activity and BGP incidents that occurred between April and June 2022.


The IDS Bypass contest was held at the Positive Hack Days conference for the third time (for retrospective, here's . This year we created six game hosts, each with a flag. To get the flag, participants had either to exploit a vulnerability on the server or to fulfill another condition, for example, to enumerate lists of domain users.
The tasks and vulnerabilities themselves were quite straightforward. The difficulty laid in bypassing the IDS: the system inspected network traffic from participants using special rules that look for attacks. If such a rule was triggered, the participant's network request was blocked, and the bot sent them the text of the triggered rule in Telegram.
And yes, this year we tried to move away from the usual CTFd and IDS logs towards a more convenient Telegram bot. All that was needed to take part was to message the bot and pick a username. The bot then sent an OVPN file to connect to the game network, after which all interaction (viewing tasks and the game dashboard, delivering flags) took place solely through the bot. This approach paid off 100%!

The first text-based CAPTCHA ( we’ll call it just CAPTCHA for the sake of brevity ) was used in 1997 by AltaVista search engine. It prevented bots from adding Uniform Resource Locator (URLs) to their web search engine.
Back then it was a decent defense measure. However the progress can't be stopped, and this defense was bypassed using OCR available at those times (for example FineReader).
CAPTCHA became more complex, noise was added to it, along with distortions, so the popular OCRs couldn’t recognize this text. And then OCRs custom made for this task appeared. It costed extra money and knowledge for the attacking side. The CAPTCHA developers were required to understand the challenges the attackers met, what distortions to add, in order to make the automation of the CAPTCHA recognition more complex.
The misunderstanding of the principles the OCRs were based on, some CAPTCHAs were given such distortions, that they were more of a hassle for regular users than for a machine.
OCRs for different types of CAPTCHAs were made using heuristics, and the most complicated part of it was the CAPTCHA segmentation for the stand along symbols, that subsequently could be easily recognized by the CNN (for example LeNet-5), also SVM showed a good result even on the raw pixels.
In this article I’ll try to grasp the whole history of CAPTCHA recognition, from heuristics to the contemporary automated recognition systems. We’ll figure out, if a CAPTCHA is still alive.
I’ll review the yandex.com CAPTCHA. The Russian version of the same CAPTCHA is more complex.

Positive Hack Days 11 will begin in a matter of weeks. This international forum on practical security will be held on May 18–19 in Moscow.
As per tradition, PHDays will have three big tracks dedicated to countering attacks (defensive), protection through attack (offensive), and the impact of cybersecurity on business. It is our pleasure to present the first talks.

The first quarter of the year 2022 has passed; now, it is time to look at the events of Q1 in terms of mitigated DDoS activity and recorded BGP incidents.
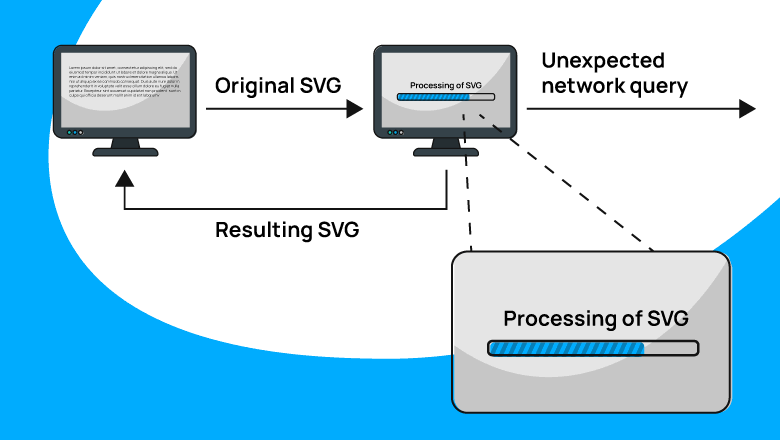
You decided to make an app that works with SVG. Encouraged by the enthusiasm, you collected libraries and successfully made the application. But suddenly you find that the app is sending strange network requests. And data is leaking from the host-machine. How so?
How can simple XML files processing turn into a security weakness? How can a blog deployed on your machine cause a data leak? Today we'll find answers to these questions, learn what XXE is and how it looks like.

When you have an IT, which supports all aspects of your organization automated performance and you have a firm confidence that IT executes well, there is always a chance that something could go wrong in technology or in related IT processes. Depending on complexity of IT environment varieties of risks scenarios could arise. This article as a summary of different faithworthy sources aims to help you in getting high level understanding on what could go wrong and how you can predict it in a more conscious way.
My name is Maxim Tornov and I have been working in various IT areas for a long period of time. Since then, for over 14 years I am working in the area of IT/IS risk management with focus on in IT/IS audits, internal control implementation and assessment.
I am sure that at the present the topic of Information Technologies risk management became more vital. Organization’s efficiency in IT risk management directly affects the achievement of various organization’s goals, goals which have dependency on IT, those goals may include reliability and efficiency of business processes, the organization's compliance with regulatory requirements, the integrity of financial reporting, and many others.
I sincerely hope that this material will be useful to you and may give you some new ideas that you can contribute to the benefit of your personal development and the development of your organization's risk management culture.

2021 was an action-packed year for Qrator Labs.
It started with the official celebration of our tenth year anniversary, continued with massive routing incidents, and ended with the infamous Meris botnet we reported back in September.
Now it is time to look at the events of the last quarter of 2021. There are interesting details in the BGP section, like the new records in route leaks and hijacking ASes, but first things first, as we start with the DDoS attacks statistics.
Link to GitHub. More details about the operation of the algorithm and the module can be found here.
The ACME protocol client is used to automatically obtain a security certificate for your site. Basically everyone uses Let's Encrypt to get a free certificate and auto-renewal. But there are other services, such as Zero SSL. It also supports the ACME protocol.
I relied on two articles from Habr (this and this), as well as RFC8555. But the information in them was not enough to implement their own version of the modulation. At least several times higher than several implementations of the module [at another level]. The tests were conducted on a live service, so there are no autotests yet. You can write and init pull request.
The module is written under Linux. Only the second version of the protocol is considered.


Application Programming Interfaces or API’s are responsible for majority of system integration and functional components of modern computing landscape in both consumer and enterprise environments.
Properly constructed secure API’s provide significant benefits during initial build, integration with other systems and during entire application lifecycle while protecting sensitive information stored in business systems.
Based on author's experience designing and implementing API’s for variety of clients in financial, insurance, telecom and public sectors, security is often overlooked in favor of simplistic, vendor/product specific solutions.
This article addresses best practices for API security design in product neutral manner to help architects to plan and build easy to work with and secure API's.
Recommended approach is to separate API security from its business functionality and allow back-end developers to concentrate only on business functions. Once business logic for an API is ready, it can be published using common security components described in this article.
This article does not provide any product specific recommendations, but any modern API security/governance platform will be able to satisfy majority of suggested requirements using out-of-the-box functionality.
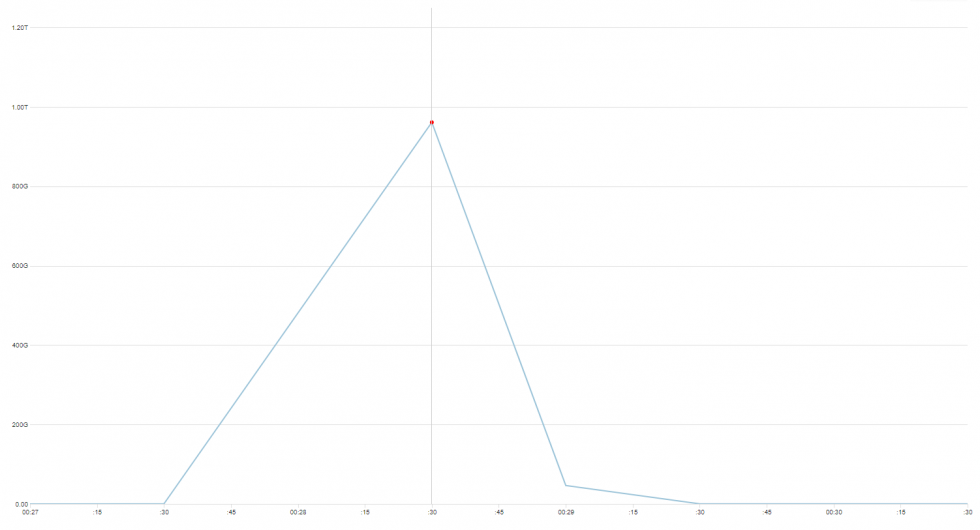
DDoS attacks send ripples on the ocean of the Internet, produced by creations of various sizes - botnets. Some of them feed at the top of the ocean, but there also exists a category of huge, deep water monstrosities that are rare and dangerous enough they could be seen only once in a very long time.
November 2021 we encountered, and mitigated, several attacks from a botnet, that seems to be unrelated to one described and/or well-known, like variants of Mirai, Bashlite, Hajime or Brickerbot.
Although our findings are reminiscent of Mirai, we suppose this botnet is not based purely on propagating Linux malware, but a combination of brute forcing and exploiting already patched CVEs in unpatched devices to grow the size of it. Either way, to confirm how exactly this botnet operates, we need to have a sample device to analyze, which isn’t our area of expertise.
This time, we won’t give it a name. It is not 100% clear what we are looking at, what are the exact characteristics of it, and how big this thing actually is. But there are some numbers, and where possible, we have made additional reconnaissance in order to better understand what we’re dealing with.
But let us first show you the data we’ve gathered, and leave conclusions closer to the end of this post.
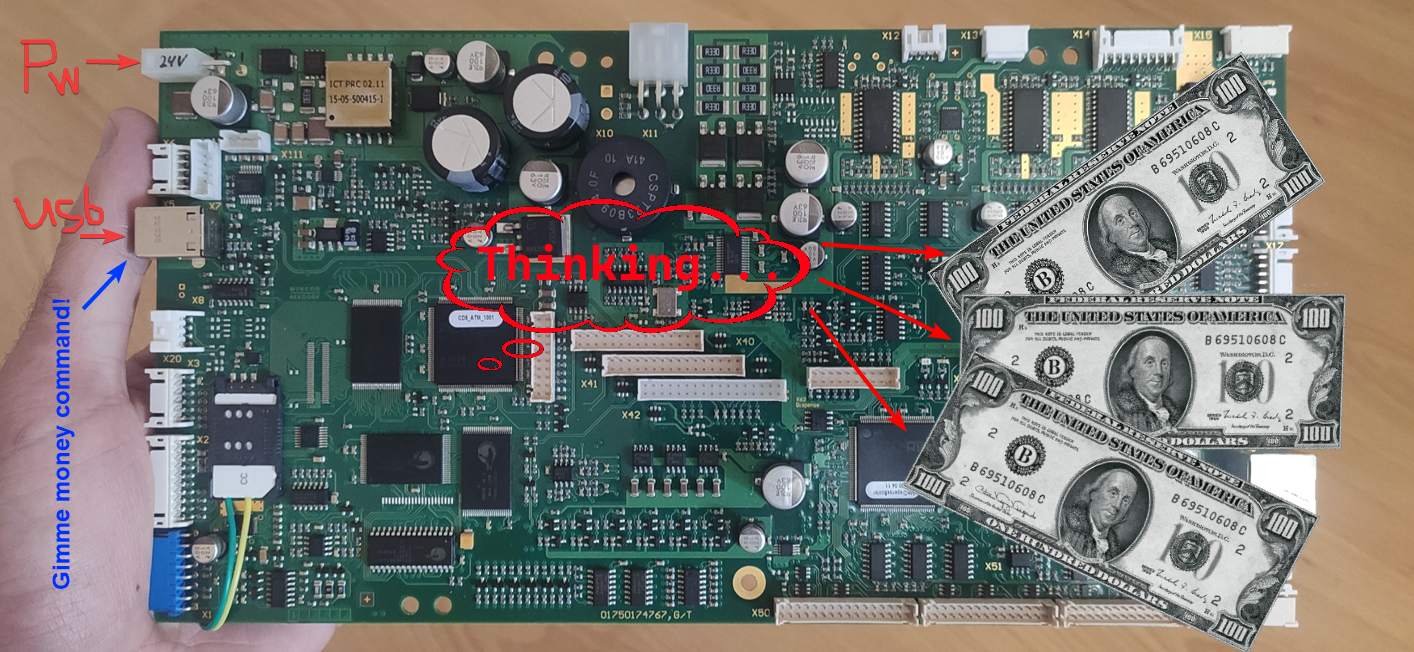
Hi there! A while ago, Positive Technologies published the news that ATMs manufactured by Diebold Nixdorf (previously known as Wincor), or more specifically, the RM3 and CMDv5 cash dispensers, contained a vulnerability which allowed attackers to withdraw cash and upload modified (vulnerable) firmware. And since my former colleague Alexei Stennikov and I were directly involved in finding this vulnerability, I would like to share some details.

Hello, everybody!
My name is Alexander Zubkov and today I’d like to talk about routing loops.
Tools to improve and control code quality can be a key success factor in a complex software project implementation. Static analyzers belong to such tools. Nowadays, you can find various static analyzers: from free open-source to cross-functional commercial solutions. On the one hand, it's great – you can choose from many options. On the other hand – you have to perform advanced research to find the right tool for your team.
Money theft is one of the most important risks for any organization, regardless of its scope of activity. According to our data, 42% of cyberattacks on companies are committed to obtain direct financial benefits. You can detect an attack at various stages—from network penetration to the moment when attackers start withdrawing money. In this article, we will show how to detect an attack at each of its stages and minimize the risk, as well as analyze two common scenarios of such attacks: money theft manually using remote control programs and using special malware—a banking trojan.

The OWASP Top Ten 2017 category A9 (which became A6 in OWASP Top Ten 2021) is dedicated to using components with known vulnerabilities. To cover this category in PVS-Studio, developers have to turn the analyzer into a full SCA solution. How will the analyzer look for vulnerabilities in the components used? What is SCA? Let's try to find the answers in this article!

The third quarter of 2021 brought a massive upheaval in the scale and intensity of DDoS attacks worldwide.
It all led to September when together with Yandex, we uncovered one of the most devastating botnets since the Mirai and named it Meris, as it was held accountable for a series of attacks with a very high RPS rate. And as those attacks were aimed all over the world, our quarterly statistics also changed.
This quarter, we've also prepared for your consideration a slice of statistics on the application layer (L7) DDoS attacks. Without further ado, let us elaborate on the details of DDoS attacks statistics and BGP incidents for Q3, 2021.