
一组印度科学家发表了以其本国为例政府机构采用的现代互联网屏蔽方法概述。他们研究了互联网服务提供商限制访问被禁信息的机制,评估了这些机制的准确性以及绕过这些屏蔽的能力。2captcha常驻代理团队整理了这项研究,并提请大家关注这项工作成果的主要论点。
Research, trends and forecasts in the IT field

一组印度科学家发表了以其本国为例政府机构采用的现代互联网屏蔽方法概述。他们研究了互联网服务提供商限制访问被禁信息的机制,评估了这些机制的准确性以及绕过这些屏蔽的能力。2captcha常驻代理团队整理了这项研究,并提请大家关注这项工作成果的主要论点。
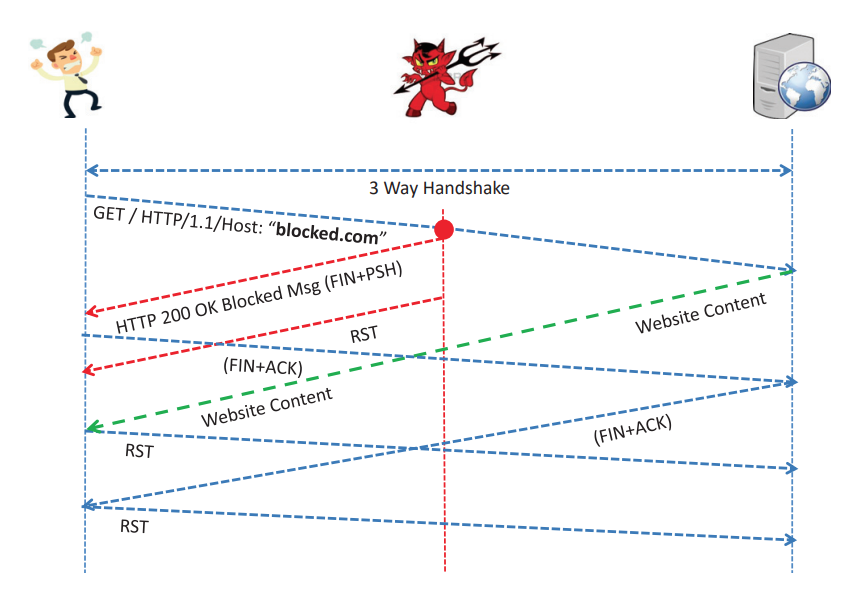
A group of Indian scientists has published an overview of modern methods of Internet blocking introduced by government agencies, using the example of their own country. They studied the mechanisms used by Internet service providers restricting access to prohibited information, assessed their accuracy, and the ability to bypass such blocks. We would like to bring to your attention the main theses of this work.

If you are at the beginning of your educational path in IT, or contemplating about making changes in your career and starting learning UX design, you might have some doubts and uncertainties on whether UX design is something worth studying and working in right now. We can dispel your doubts: UX designers are very required in the majority of companies, since they help to make products appealing to users, thus raising the companies income and enhancing their reputation. Professionals in this sphere are in high demand right now, and

Title:
After sale IT support for American and Western Companies
Let’s have a case study.
A Russian IT company sells software to a western country like say America. And you are working as an application developer on the support side.
One day, there is a problem with the program, and the program has stopped working.
You must contact the company now to inform them that the program is off-line.
THE NEXT STEP YOU TAKE IS VERY IMPORTANT.
The way, the two cultures operate in a situation like this are very different and it will have everything to do with how easy your job goes for you.
…………
Russia : “we have a problem”
“What is wrong?”
“I don’t know”
“When can it be fixed?”
“I don’t know”
……………
USA: “i’m just giving you a real quick call to let you know that there is a problem with the program.
I’ve already put my team on it and we will have it up and running shortly.
I will let you know more by 3 o’clock today what is going on”
It’s not important how long you think it will take you, but I will always tell them a few hours from the time that you informed them of a problem.
I understand that you have no idea how deep the bug is and also whether it will affect any other systems.
But it is important to set a time window very close to when you inform them that you will bring them more information.
This also works very well if you don’t know something that they ask you.
Question:
“What can we do to fix this problem?”
Answer:
“I understand what you’re saying. I will look into it and get back to you in two hours. By 1 PM today.”
in this case, it’s important that you:
1. Take responsibility for yourself and your team.
2. Communicate that you understand this responsibility.
3. Gives strict timelines. (if it’s not possible, you can always say that there is a problem, but do it before the deadline.)
4. Use certain key language.
“ I understand you”
“ I understand what you were saying”
“ I wanted to inform you”
“ we are working on it right now”

This is one of the most important articles I’ve written.
In this article, I’m going to dive deep into one of the largest differences between Russia and America pertaining to sales and marketing.
1. You must use your name.
2. You must have a personal approach.
3. You must show that you are involved.
4. You must show that you care about the needs and desires of the client.
Recently, I was faced with an interesting problem. I was asked to call clients without making it personal.
So let’s go back to when I was in America, living and working as a sales person. The company I work for, was very large, and had multiple branches around the Washington DC area. They had offices in three states.
They put me through a sales training course.
The biggest “take away” from the course…..
You’re not selling the product/
you’re selling yourself.
It's important to use your charisma and your genuine caring for the customer to win them over. Once they understand that you're actually trying to help them, then they will seriously consider the item you are telling them about.
I also want to say, very clearly, that it's not a prideful approach. It should be a professional approach. You're responsible to tell the customer/ the client all the benefits of the item and how this item will help their business.
Everything above pertains to sales in America. So if you are approaching America as a sales manager this is how you should craft your approach.
Now I've spoken to my colleague,
Kristina Pashnina and we have agreed upon some stark differences to the Russian sales climate. Here she will begin to tell you how the Russians see sales.

My last article stirred up some definite comments and even questions about different things in business. I’m going to keep giving you as much information as I can so that you can continue to do business as IT professionals outside of Russia with other countries.
How do you design a website that will be viewed in the west and appreciated by the people there?
What are the most important elements
for, America and other western markets?
Information shared below is exactly how I work with my IT professionals who are going to be participating in pre-sales to America. I tell them exactly this, and it helps prepare them to successfully sell the the United States companies.
As developers and IT companies, we must sell our software.
What can give you an edge in this very competitive market place?
Please, if you would allow me to let me explain why this is important and how this can make your company more successful. There’s a certain type of thinking that is conducive to working as a software developer. This is a very practical mindset, but it goes beyond that. If you have the mindset of direct thinking.
Here are examples:
I see the target a target and I don’t see obstacles
Вижу цель, не вижу препятствий
This is an example of the practical mindset, how is approaches the problem of development. It makes people who have this mindset, the best developers in the world.
Example of mindset:
Problem……………… find a solution………… No problem.
Notice how this looks exactly like a line of code?
This is well-known around the world in places where you would like to sell your software, the United States, Germany, Belgium, and the Middle East.
Countries where people have this mindset have the best developers.
now let’s talk about your competition:
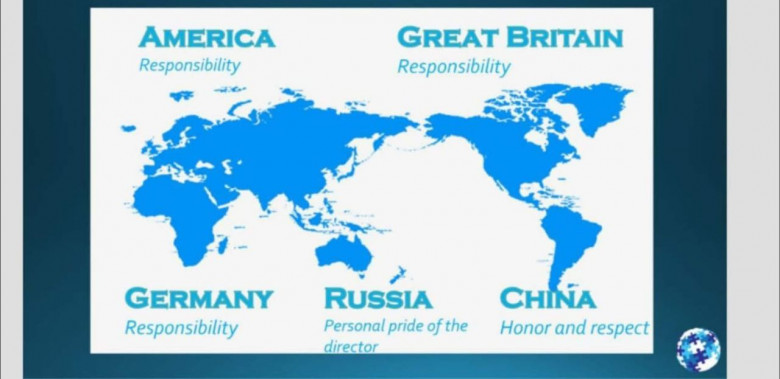
Americans: during the center process, “find a solution” Americans are overly concerned about responsibility. This slows them down in the decision making process.
i’m writing this series articles to spearhead the new marketing campaign for into the American market. I will be covering a wide range of topics that will allow us to position the company in the proper way so that is excepted as a provider of High-quality software in America.
The key to converting an American CEO or CFO is the trigger point for the American business culture. The trigger point for America is responsibility. This means in business you must be responsible. You also look for business partners that are responsible.
But let’s take this into the newest more powerful view that we need to have now.
The scene from the point of you of the CFO sitting at the head of the financial controls of a large hospital conglomerate. Put yourself in the mind of the CFO. What are they concerned about?
As an American CFO they will be very concerned about whether they are being responsible in their job and responsible to the hospital, staff, shareholders, patients and the management above them.
And this is how we get our foot in the door in this American niche market. If we present ourselves as offering something that “May” give an answer to specific problems that they know that they have, they must give us a chance to present a Presale. The reason is because they are responsible, and if there is a solution as an American Director you must explore that solution.
It would be irresponsible to not explore a potential solution.
Then it’s a simple case to actually give value in the presale meeting and convince them that we can deliver some thing that will benefit their business and profits.
In our last article we covered the anatomy of a presale meeting gone wrong. In that article we posed some questions for everyone to think about. What exactly does an American company wanting to hire a Russian custom software development company, feel about this Russian company? What are they afraid of? What are their concerns?
In the end we came up with five concerns.
1. Is the company a fly by night company, is the company a one-day company?
2. Will they be professional in supporting or developing the software that they've sold to us?
3. Will they have proper data security?
And now the two new ones that are because of the mess the world is in now...
4. Will they be able to complete the project on time? This includes proper internet access an infrastructure to support IT.
5. Where is your team located? Are you still located in Russia?
Now we're going to look at the last 2, number four and five.
However let's look at number 5 first.
Many IT companies today if they want to work with the United States or even Europe they must not have their developers located inside of Russia. Matter of fact it goes so far that if a developer is located in Russia and they're using a VPN and somehow the VPN is breached the credentials are canceled for that developer to work on the project.
It's for this reason that Russian IT companies are opening offices around the world. Let's look at Armenia as an example.
Wait a minute I have to go back for a second...... We must discuss how countries look to America Canada and Western Europe. I basically give them a score based on questions that are brought up in the mind of the American company or European company.
My name is Paul Karol and I work connecting Russian IT with their customers in the United States. Please find on Hbar my previous article for a complete explanation of my credentials.
Today we're going to look at a presale meeting that was not successful and we will explain exactly how the Russian company lost this business. Please take a look at this photograph.
Going into this presale meeting the client (large American chain store) had worked with the software for a little more than a month and we're pretty happy with the result. From all indications they were going to buy the software this day. The sales manager had a good relationship with the American managers of the company. There was lots of buying sign that was known to the Russian company prior to this presale meeting. Suffice to say that they believe that they would have an easy sale today.
There was some very specific things that the Russians did that cost them this business.
We will be using this as a case study and we will discuss exactly everything that they did as a mistake and how to not do these same mistakes for your company.
First we must do some brain work. A thought experiment, if you will. What do you believe are the concerns of an American company doing business with Russian IT developers today. The current situation between the countries does make it more difficult but the same exact concerns are still there from before maybe slightly more amplified and there may be one more concern that wasn't there prior to the difficulties in Ukraine.
Russian speaking IT presales and passing interviews to the West
I'm Paul Karol an American and I've been living in Russia and working internationally with businesses for the last 10 years. My first client was a Gazprom high level director and we worked on international communication and connections with the West and China.
I am the keynote speaker in many events and also give companywide training for companies that interact with other countries. I have been working deeply with The IT community of Russia for 6 years. My job is to make them pass their project interviews. Also I work with the presales and make sure that the company gets the projects that they want.
I'm the expert on Russia, Chinese and the Western cultural relations.
First: if your company is just beginning to approach the Western market including America you want to have success in the beginning. If you're successful at passing the first few presale meetings or project interviews your reputation will be established. If you fail a few interviews or presales then you start to develop a reputation.

I believe listicles have a huge potential for testing demand hypotheses. Have you tried using listicles for your demand validation? If so - let us know in the comments how this worked for you.
Do you know these "Top N something something" kind of articles? Like:
- 5 best GPS vehicle trackers
- The 14 hair growth products that actually work
- Top 10 Best CRM Software Tools in 2023
They are often referred to as "listicles" - articles presented in the form of a list.
I love them - they make picking a new phone, a movie to watch, an app to install much easier. I also use them at work all the time while looking for solutions to everyday challenges.
So what if we use one of them to benchmark our product against the best available alternatives?


The year 2021 started on such a high note for Qrator Labs: on January 19, our company celebrated its 10th anniversary. Shortly after, in February, our network mitigated quite an impressive 750 Gbps DDoS attack based on old and well known DNS amplification. Furthermore, there is a constant flow of BGP incidents; some are becoming global routing anomalies. We started reporting in our newly made Twitter account for Qrator.Radar.
Nevertheless, with the first quarter of the year being over, we can take a closer look at DDoS attacks statistics and BGP incidents for January - March 2021.

Technology is as adaptable and compatible as mankind; it finds its way through problems and situations. 2020 was one such package of uncertain events that forced businesses to adapt to digital transformation, even to an extent where many companies started to consider the remote work culture to be a beneficiary long-term model. Technological advancements like Hyper automation, AI Security, and Distributed cloud showed how any people-centric idea could rule the digital era. The past year clearly showed the boundless possibilities through which technology can survive or reinvent itself. With all those learnings let's deep-dive and focus on some of the top technology trends to watch out for in 2021.


Annotation. This article gives an analogy between the forces of nature and various types of money. A justification for the "money conservation laws" is made. Explanation of the IT-money phenomenon by analogy to physics laws is given, as well as gold and currency money. The transition from the gold and currency to the gold-currency-computing economy is considered. A reasonable assumption is made that the fourth type of money after gold, securities and IT money will be so-called "citation indices" or "ratings", which are similar in their properties to stock indices.

This article is an attempt to understand what money is from the physics and econophysics points of view. Econophysics (economics and physics) is an interdisciplinary research field, applying theories and methods originally developed by physicists to solve problems in economics, usually those including uncertainty or stochastic processes, nonlinear dynamics and evolutionary games.
The last decades the world economy regularly falls into this vortex of financial crises that have affected each country. It almost led to the collapse of the existing financial system, due to this fact, experts in mathematical and economic modelling have become to use methods for controlling the losses of the asset and portfolio in the financial world (Lechner, L. A., and Ovaert, T. C. (2010). There is an increasing trend towards mathematical modelling of an economic process to predict the market behaviour and an assessment of its sustainability (ibid). Having without necessary attention to control and assess properly threats, everybody understands that it is able to trigger tremendous cost in the development of the organisation or even go bankrupt.
Value at Risk (VaR) has eventually been a regular approach to catch the risk among institutions in the finance sector and its regulator (Engle, R., and Manganelli S., 2004). The model is originally applied to estimate the loss value in the investment portfolio within a given period of time as well as at a given probability of occurrence. Besides the fact of using VaR in the financial sector, there are a lot of examples of estimation of value at risk in different area such as anticipating the medical staff to develop the healthcare resource management Zinouri, N. (2016). Despite its applied primitiveness in a real experiment, the model consists of drawbacks in evaluation, (ibid).
The goal of the report is a description of the existing VaR model including one of its upgrade versions, namely, Conditional Value at Risk (CVaR). In the next section and section 3, the evaluation algorithm and testing of the model are explained. For a vivid illustration, the expected loss is estimated on the asset of one of the Kazakhstani company trading in the financial stock exchange market in a long time period. The final sections 4 and 5 discuss and demonstrate the findings of the research work.