Итак, по просьбе
Shoohurt рассказываю все известное нам (команде разработчиков Miranda IM) на данный момент о проделках AOL.
Сегодня, около 13.00 МСК почти все пользователи неофициальных клиентов после входа в сеть и загрузки контакт-листа получали от пользователя с UIN 1 сообщение о том, что используемая версия клиента не используется и неавторизованна. На официальном сайте прямо на главной появилось сообщение, гласящее о том, что отныне поддерживаются только официальные версии программ, которые вот прям тут и можно скачать.
Пользователи, которые уже находились в сети, никаких изменений не почувствовали и не были отключены от сервера. У тех, кто пытался подключиться в первые час-полтора это получалось с переменным успехом: это объясняется тем, что что сеть icq распределенная и состоит из множества серверов, и даже после входа вас могут перебросить на другой, и судя по всему изменения применялись на них по очереди.
Немного технических деталей. Процедура входа проходит вполне обычно: проходит инициализация протокола, отсылка capabilities, загрузка серверного контакт-листа и собственных данных. Примерно в это время и приходит сообщение от номера один, и после этого получить что-либо с сервера становится невозможно.
Решив, что сегодня повторилась ситуация 8-го декабря, когда клиенты перестали работать из-за того что во время логина идентифицировали себя как icq5.1 и более ранние версии, мы попробовали идентифицировать себя как icq6.5 последней модели. Это не принесло никаких результатов. Стало понятно, что в этот раз АОЛ пошел путем глубокой защиты — видимо теперь уже стали учитываться отправляемые капсы (capabilities, информация о поддерживаемых клиентом фишках протокола). Действительно, подмена их набора на тот, что использует icq6 помогла, однако только на время первого входа — если после этого переподключиться, то это уже не поможет. Судя по всему в последовательность входа и начальной инициализации внесли какие то изменения, при невыполнении которых клиент считается альтернативным. Разработчики QIP высказали предположение о том, что серверу нужен некий дополнительный ключ, который может как просто быть зашит в клиент, так и вычисляться на основе полученной от сервера информации. Они в настоящий момент тоже усиленно работают над поиском причины отказа клиента.
Надеюсь в течение ближайших суток — двух мы найдем причину.
Кроме того хочу заметить интересный факт — эти изменения затронули только жителей стран СНГ. Когда я связался с нашими разработчиками из Чехии и Германии они были слегка в недоумении — у них все работало прекрасно. Кроме того мы успешно смогли подключиться с миранды, используя американский прокси-сервер, так что есть подозрения о том, что это целенаправленная блокировка разрабатываемых в России альтернативных мессенджеров.
UPD: Сейчас разработчик QIP, INF, поделился со мной мыслью о том, что все дело в используемом начальном значении идентификатора последовательности у отправляемых пакетов. Все неофициальные клиенты генерируют их случайным образом, и это может быть тот самый ключ. Основная проблема заключается в том чтобы узнать алгоритм его генерации.
Еще небольшой
UPD: для наглядности можете сравнить скриншоты сайта
icq.com, отдаваемые
российским и
американским посетителям
Обсуждение происходящего ведется в жаббере, в конфе icq_stop@conference.jabber.ru
UPD2: Как сообщает
Shoohurt, завтра, возможно, в течение дня будут комментарии со стороны господ, имеющих непосредственное отношение к русской версией ICQ (Рамблер-ICQ). Следите за обновлениями.
UPD3: Сейчас нашли корреляцию между временем входа и используемым номером последовательности, так что есть зацепка, что для генерации все же используется какое то случайное число, но эту версию надо проверять. Так же как оказалось коннектятся все старые клиенты, даже icq2003b, и TestBuddy 2002 года. Плюс есть несколько сообщений о том что у некоторых провайдеров в Омске все работает нормально.
В общем сейчас конечный вывод — «асечники» нашли коренное различие между официальным клиентом и всеми клонами и активно его используют.
Похоже что команда разработчиков QIP нашла решение проблемы, уже доступны рабочие билды QIP Infium 9022
Как и обещал — исправленная версия плагина Miranda IM ICQ+ — качаем
Господа, прошу терпения. Я сегодня вымотан на нет и уже больше суток без сна. Завтра я выложу весь код и объясню суть моего решения. Оно довольно тривиальное, и основано на том что исходное предположение про seq ид верно. И вообще оно слегка на подпорках.







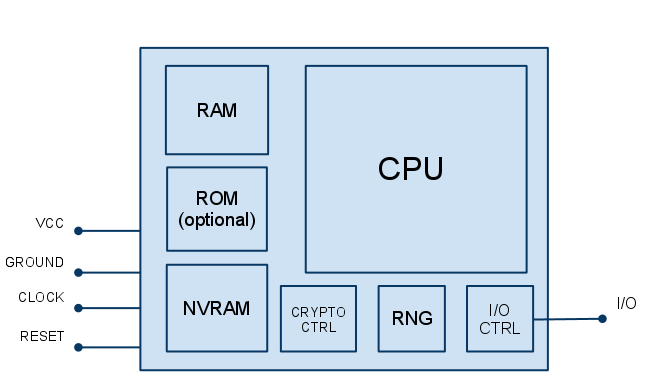


 Возможное, многие из вас думали после ситуации с Фобос-Грунтом — что такого особенного в микросхемах для космоса и почему они столько стоят? Почему нельзя поставить защиту от космического излучения? Что там за история с арестом людей, которые микросхемы экспортировали из США в Россию? Где все полимеры?
Возможное, многие из вас думали после ситуации с Фобос-Грунтом — что такого особенного в микросхемах для космоса и почему они столько стоят? Почему нельзя поставить защиту от космического излучения? Что там за история с арестом людей, которые микросхемы экспортировали из США в Россию? Где все полимеры?
