Web and Azure Tool Updates in Visual Studio 2019
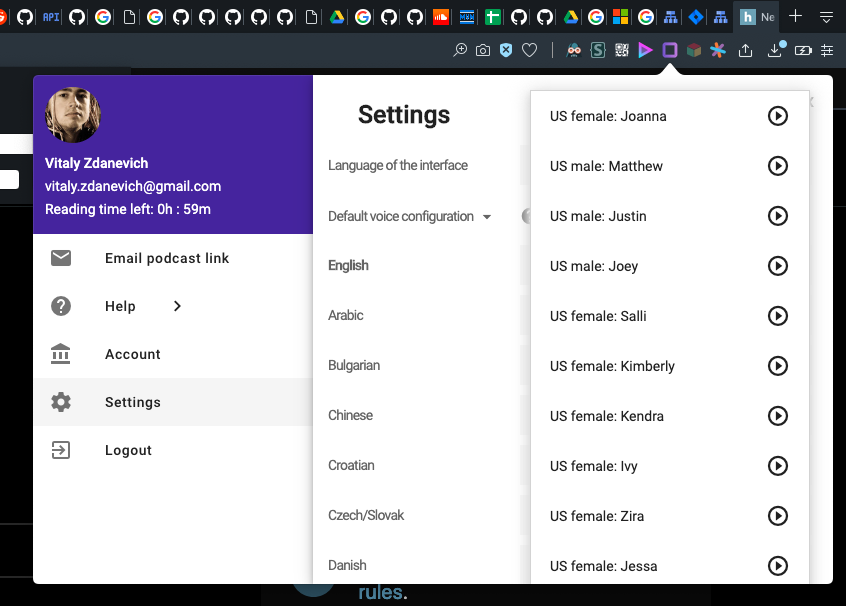
Hopefully by now you’ve seen that Visual Studio 2019 is now generally available. As you would expect, we’ve added improvements for web and Azure development. As a starting point, Visual Studio 2019 comes with a new experience for getting started with your code and we updated the experience for creating ASP.NET and ASP.NET Core projects to match:
If you are publishing your application to Azure, you can now configure Azure App Service to use Azure Storage and Azure SQL Database instances, right from the publish profile summary page, without leaving Visual Studio. This means that for any existing web application running in App Service, you can add SQL and Storage, it is no longer limited to creation time only.
Dog Breed Identifier: Full Cycle Development from Keras Program to Android App. on Play Market
However, there are still countless little details that… they are not insolvable, no. They simply take too much of your time, especially if you are a beginner. What would be of help is a step-by-step project, done right in front of you, start to end. A project that does not contain «this part is obvious so let's skip it» statements. Well, almost :)
In this tutorial we are going to walk through a Dog Breed Identifier: we will create and teach a Neural Network, then we will port it to Java for Android and publish on Google Play.
For those of you who want to see a end result, here is the link to NeuroDog App on Google Play.
Web site with my robotics: robotics.snowcron.com.
Web site with: NeuroDog User Guide.
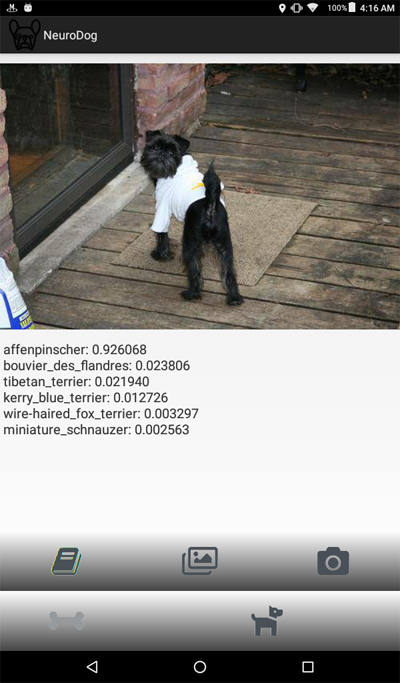
Here is a screenshot of the program:
Visual Studio 2019 .NET productivity
Your friendly neighborhood .NET productivity team (aka. Roslyn) focuses a lot on improving the .NET coding experience. Sometimes it’s the little refactorings and code fixes that really improve your workflow. You may have seen many improvements in the previews, but for all of you who were eagerly awaiting the GA release here’s a few features you may enjoy!
Web application firewalls
Web application firewall
Web application firewalls (WAFs) are a type of intrusion detection and prevention system and might be either a hardware or software solution. It is specifically designed to inspect HTTP(s) and analyse the GET and POST requests using the appalling detection logic explained below. Web application firewall software is generally available as a web server plugin.
WAF has become extremely popular and various companies offer a variety of solutions in different price categories, from small businesses to large corporations. Modern WAF is popular because it has a wide range of covered tasks, so web application developers can rely on it for various security issues, but with the assumption that this solution cannot guarantee absolute protection. A basic WAF workflow is shown below.
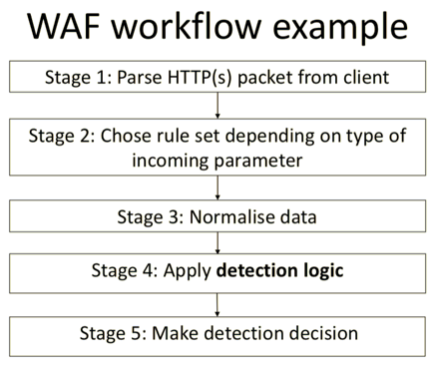
Its main function is the detection and blocking of queries in which, according to WAF analysis, there are some anomalies, or an attacking vector is traced. Such an analysis should not make it difficult for legitimate users to interact with a web application, but, at the same time, it must accurately and timely detect any attempted attack. In order to implement this functionality, WAF developers usually use regular expressions, tokens, behavioural analysis, reputation analysis and machine learning, and, often, all these technologies are used together.
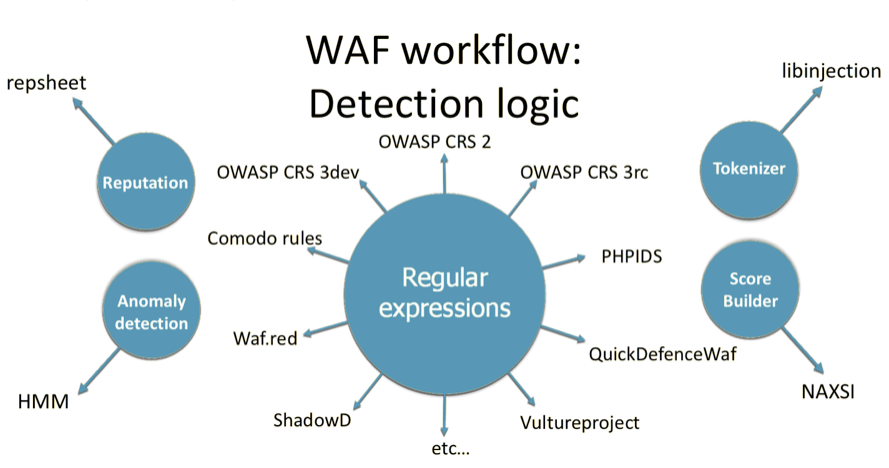
In addition, WAF can also provide other functionality: protection from DDoS, blocking of IP-addresses of attackers, tracking of suspicious IP-addresses, adding an HTTP-only flag to the cookie, or adding the functionality of CSRF-tokens. Each WAF is individual and has a unique internal arrangement, but there are some typical methods used for analysis.
Dependency Injection in Flutter
We’re currently experimenting with Flutter while developing our side project for step challenges with colleagues. This side project should also be considered as a playground, where we can check if we can use Flutter in more serious projects. That’s why we want to use some approaches there that can look like an over-engineering for such a small project.
So one of the first questions was what can we use for dependency injection. A quick search in the internet revealed 2 libraries with positive reviews: get_it and kiwi. As get_it turned out to be a Service Locator (and I’m not a fan of this pattern), I was going to play with kiwi, which looked more promising, but then I’ve found another one library: inject.dart. It is heavily inspired by Dagger library, and as we use the latest one in our other Android projects, I’ve decided to dig into it.
What's new in CUBA 7
What's new in CUBA 7
Three years ago we announced the second publicly available major version of the framework. CUBA 6 was the game-changing version — the licensing was turned from proprietary to Apache 2.0. Those days we couldn't even guess where it was going to bring the framework in long term. CUBA community started to grow exponentially, so we have learned a lot of possible (and sometimes impossible) ways of how developers use the framework. Now we are happy to announce CUBA 7, which, we hope, will make development more coherent and joyful for all community members from those just starting their journey in CUBA and Java to skilled enterprise developers and Java experts.

Zotero hacks: unlimited synced storage and its smooth use with rmarkdown
Here is a bit refreshed translation of my 2015 blog post. The post shows how to organize a personal academic library of unlimited size for free. This is a funny case of a self written manual which I came back to multiple times myself and many many more times referred my friends to it, even non-Russian speakers who had to use Google Translator and infer the rest from screenshots. Finally, I decided to translate it adding some basic information on how to use Zotero with rmarkdown.

A brief (and hopefully unnecessary for you) intro of bibliographic managers
Bibliographic manager is a life saver in everyday academic life. I suffer almost physical pain just thinking about colleagues who for some reason never started using one — all those excel spreadsheets with favorite citations, messy folders with PDFs, constant hours lost for the joy-killing task of manual reference list formatting. Once you start using a reference manager this all becomes a happily forgotten nightmare.
Frontend Weekly Digest (25 Feb – 3 Mar 2019)

Implementation of the digital mobile-only bank in Kazakhstan
On the other side of the world, the digital and mobile banks namely, Starling bank, Monzo, N26 are becoming increasingly popular among society in the United Kingdom. As a vivid illustration, Starling Bank has increased considerably the number of customers for 8 times (up to 400 000 people) at the end of the 2018 year (Starling Bank, 2019). At the same time, one million clients have joined and used Monzo’s services (Monzo). Such tendency establishes substantial competition for all players including high-street banks in the payments market.
In consequences, the main object of the paper is identification the advantages of digital bank and illumination capabilities to deploy analogous mobile bank in Kazakhstani real financial sector.
Blazor 0.8.0 experimental release now available

Blazor 0.8.0 is now available! This release updates Blazor to use Razor Components in .NET Core 3.0 and adds some critical bug fixes.
Get Blazor 0.8.0
To get started with Blazor 0.8.0 install the following:
- .NET Core 3.0 Preview 2 SDK (3.0.100-preview-010184)
- Visual Studio 2019 (Preview 2 or later) with the ASP.NET and web development workload selected.
- The latest Blazor extension from the Visual Studio Marketplace.
The Blazor templates on the command-line:
dotnet new -i Microsoft.AspNetCore.Blazor.Templates::0.8.0-preview-19104-04
You can find getting started instructions, docs, and tutorials for Blazor at https://blazor.net.
MSVC Backend Updates in Visual Studio 2019 Preview 2: New Optimizations, OpenMP, and Build Throughput improvements

In Visual Studio 2019 Preview 2 we have continued to improve the C++ backend with new features, new and improved optimizations, build throughput improvements, and quality of life changes.
The Links Theory 0.0.2

This world needs a new theory — a theory that could describe all the theories on the planet. A theory that could easily describe philosophy, mathematics, physics, and psychology. The one that makes all kinds of sciences computable.
This is exactly what we are working on. If we succeed, this theory will become the unified meta-theory of everything.
A year has passed since our last publication, and our task is to share the progress with our English-speaking audience. This is still not a stable version; it’s a draft. Therefore, we welcome any feedback, as well as your participation in the development of the links theory.
As with everything we have done before, the links theory is published and released into the public domain — it belongs to humanity, that means, it is yours. This work has many authors, but the work itself is far more important than any specific authorship. We hope that today it can become useful to more people.
We invite you to become a part of this exciting adventure.
PostgreSQL 18: Part 2 or CommitFest 2024-09

Statistically, September CommitFests feature the fewest commits. Apparently, the version 18 CommitFest is an outlier. There are many accepted patches and many interesting new features to talk about.
If you missed the July CommitFest, get up to speed here: 2024-07.
PostgreSQL 17: Part 5 or CommitFest 2024-03

Since the PostgreSQL 17 RC1 came out, we are on a home run towards the official PostgreSQL release, scheduled for September 26, 2024.
Let's take a look at the patches that came in during the March CommitFest.
PostgreSQL 16: Part 5 or CommitFest 2023-03

The end of the March Commitfest concludes the acceptance of patches for PostgreSQL 16. Let’s take a look at some exciting new updates it introduced.
I hope that this review together with the previous articles in the series (2022-07, 2022-09, 2022-11, 2023-01) will give you a coherent idea of the new features of PostgreSQL 16.
Writing The Matrix in Python

Programming textbooks usually do not indulge us with variety of examples. In most manuals, exercises are similar to each other and not particularly interesting: create another address book, draw a circle using turtle, develop a website for a store selling some kind of "necessary" advertising nonsense. Too far from the authentic imitation of "The Matrix". Although…
How about taking over the control and starting to invent exercises yourself?
Would you like to write your own personal little "Matrix"? Of course, not the one with skyscrapers, stylish phones of the time, and the ubiquitous invincible Agent Smiths. We will need a couple of more months of learning for that. But any beginner programmer can write a model of the cult splash screensaver with the green streams of digits flowing down the screen. Let's try to creat it in the "great and mighty" Python.
Turning a typewriter into a Linux terminal

Hi everyone, a few months ago I got a Brother AX-25, and since then, I've been working on turning it into a computer. It uses an Arduino to scan the custom mechanical keyboard and control the typewriter, and a Raspberry Pi is connected to the Arduino over serial so I can log into it in headless mode.