Обратная связь

 в hex-редакторе, и, конечно, ссылку на спецификацию.
в hex-редакторе, и, конечно, ссылку на спецификацию.

Всем привет! Меня зовут Паша и возможно вы уже пользуетесь моим расширением Ave blacklist для блокировки продавцов спамеров на авито. Но сегодня не об этом.
Больше года назад Кабинет министров не поддержал законопроект с ценой за килограмм или литр, новость была на Пикабу в том числе
Что ж, Кабинет министров не поддержал, а я поддерживаю двумя руками!
И написал расширение для браузеров для расчета цена за единицу измерения на сайтах доставок еды - заКило (chrome, firefox)
Мог бы научить и в офлайн магазинах цену за единицу измерения считать, но кто бы меня спрашивал :D

Были ещё и другие электронные игры, но именно «Ну, погоди!» считается классикой.
Игре посвящено много ностальгических статей и видео. На различных торговых площадках можно купить её в различном состоянии от убитого до «с хранения» и даже новодел.
Лет 10 назад и я купил её в идеальном состоянии, поигрался, вспомнил детство и положил в ящик. Но несколько месяцев назад с разочарованием увидел, что «потекла» нижняя часть экрана.
Можно было или отремонтировать, или купить другой экземпляр игры, но я сначала попробовал узнать, как её отремонтировать, а потом решил воссоздать игру на современных компонентах.
Я не был одинок в своём желании воссоздать игру, этой теме посвящено также немало статей, но в них обычно создавали симуляторы, а не эмуляторы игры. Симулятор у меня ассоциируется с фразой: «Я художник, я так вижу», эмулятор — это более точное воспроизведение устройства.
Формат статьи не позволяет выразить все те ощущения, которые я испытал при путешествии от зарождения идеи до реально работающей игры, практически ничем не отличающейся от оригинала. Много из того, что я узнал в этом путешествии, не поместилось в статью или поместилось в очень сжатом виде.
Эмулятор максимально приближен к оригиналу, если не считать экран (он не сегментный, как в оригинале) и корпус (я пока реализовал на беспаечной макетной плате).
Если вам интересно, как за несколько вечеров воссоздать у себя эмулятор «Ну, погоди!» на современном микроконтроллере или просто поностальгировать, добро пожаловать под кат.

Однажды мне захотелось изучить Kubernetes и мобильную разработку, но не знал, с чего начать. В то же время меня сильно тревожило отсутствие в интернете новостей без политической повестки и негативного окраса. Отовсюду лился поток манипулятивной информации, и я мечтал о фильтре, который бы отсеивал весь этот информационный шлак.
Это моя небольшая история, как я за месяц написал карманное медиа с полной автоматизацией, где роботы-ведущие заменили кожаных мешков и ведут подкасты, в которых шутят про AI
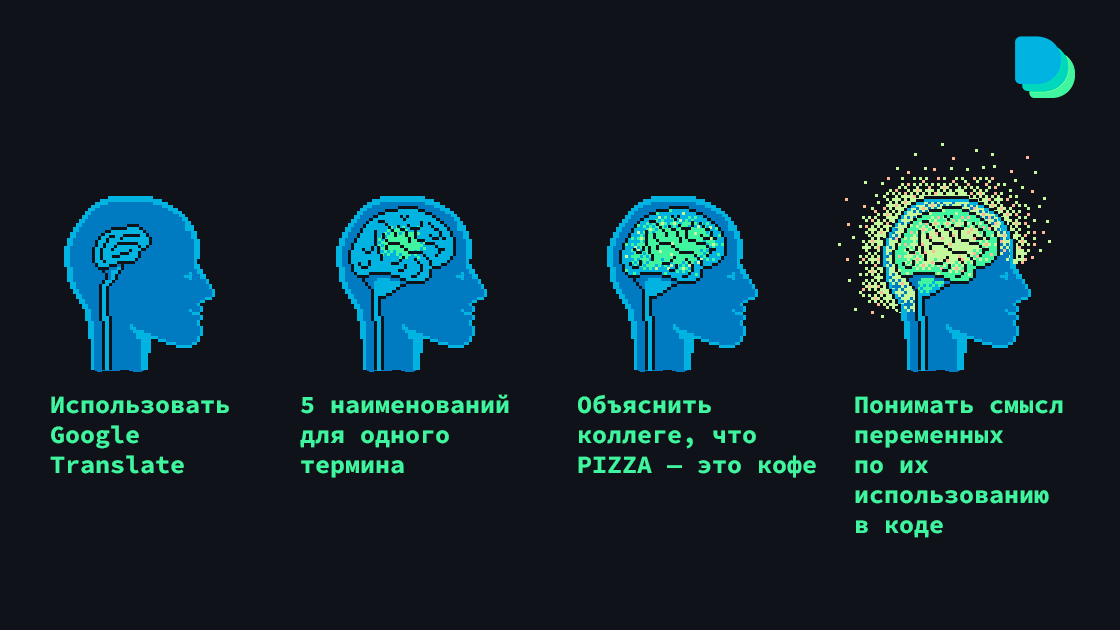
Это объект Pizza, там хранится инфа о латте, а заказали его в Restaurant или в Pizzeria? Неудобно? Максимально. Мы читаем код существенно больше, чем пишем. И хочется сразу понимать, что происходит, не играя в квесты «что имел в виду автор», «да как это работает» и «я снова ничего не понял». Без навыка давать хороший нейминг невозможно писать качественный и поддерживаемый код. Про нейминг говорят заодно, в рамках архитектуры и общих инженерных практик. В статье поговорим про него отдельно.
Как получается, что код становится мало понятным даже для его авторов? Почему нейминг так важен? Как придумывать названия, не применяя целые теории нейминга? Как лёгким процессом организовать работу с неймингом в команде? На все эти вопросы мы ответим в статье.
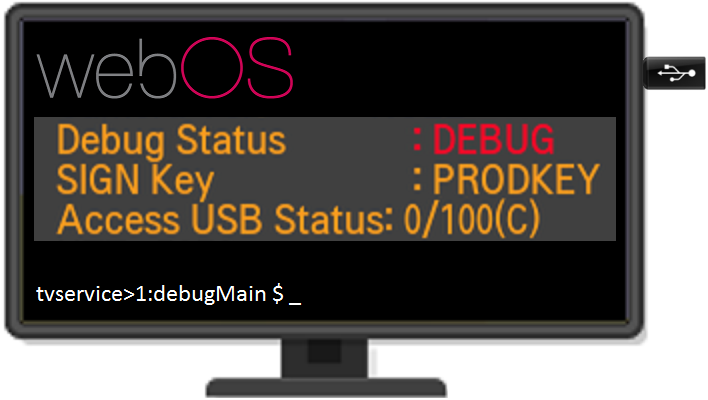
Многие современные телевизоры имеют скрытые сервисные меню, через которые можно посмотреть и изменить различные параметры, недоступные в обычном пользовательском меню. В телевизорах LG есть 2 основных сервисных меню - InStart и EzAdjust, которые можно вызвать посылкой "секретных" ИК кодов, отсутствующих на обычном пульте. Подробности о том, как открыть эти меню, легко найти в интернете, не буду на этом останавливаться, один из вариантов - в этой статье. К сожалению, многие интересные опции в сервисных меню были недоступны для изменения.
В меню InStart меня заинтересовала строка Access USB Status. Гугление не давало никакой информации о том, что это за Access USB, но интуиция подсказывала, что это что-то интересное.

TL;DR в Российских системах электронного голосования нет достаточного обеспечения тайны голосования, и похоже это сделано специально
Executive summary: В Российских системах Дистанционного Электронного голосования допущена организационная ошибка при постановке задания, позволяющая при использовании побочного канала сбора данных о пользователях (на уровне логов вебсервера) организатору голосования нарушить тайну голосования. Разработчики специально обходят тему наличия и необходимости ликвидации такой уязвимости.
Уже третий день у всех на слуху слова Meltdown и Spectre, свеженькие уязвимости в процессорах. К сожалению, сходу найти что либо про то, как именно работают данные уязвимости (для начала я сосредоточился на Meldown, она попроще), у меня не удалось, пришлось изучать оригинальные публикации и статьи: оригинальная статья, блок Google Project Zero, статья аж из лета 2017. Несмотря на то, что на хабре уже есть перевод введения из оригинальной публикации, хочется поделиться тем, что мне удалось прочитать и понять.


Приглашаем вас вновь посетить Free-lance.ru
Мы заметили, что вы давно не заходили на Free-lance.ru. Тем временем, на сайте публикуется около 40 000 проектов в месяц, а средняя стоимость проекта составляет 20 000 рублей. Наверняка, многие из этих проектов будут вам интересны.