A few months ago I came across a very interesting documentary series on Netflix called
Abstract, they basically explore the output of professional designers from different sectors like architecture, graphic design, fashion, … in their workplaces.
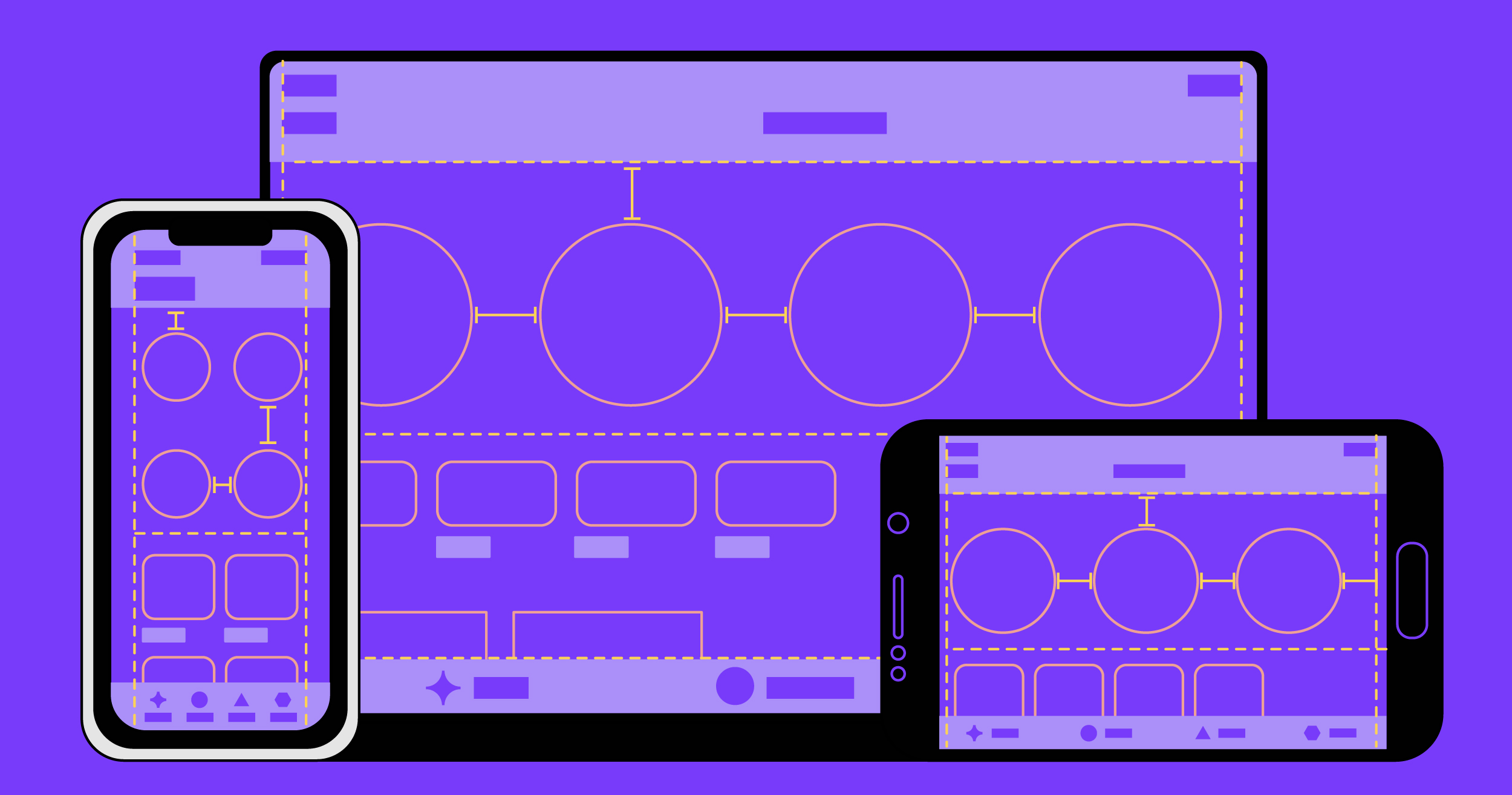
It was easy to spot some similarities in the work of designers from other fields with that of an iOS developer who implements user interfaces. For example, when a designer is creating something that is big enough to be broken down into smaller parts, using a strategy like ‘
Divide and Conquer’ is key to being able to focus on smaller parts that will be assembled at later stages in the process.
Breaking down a whole design into smaller subunits allows us to think about each problem in isolation, removing any dependencies between the components. But the full picture also needs to be present throughout the whole process, otherwise there can be problems when the time comes to fit everything back together.
On the other hand, while watching
Abstract I noticed that in the design process for objects like a shoes, banners or buildings the final design remains fixed for the lifetime of the product. The design of a Nike shoe isn’t going to change after it is released and there aren’t going to be any updates once it’s on the shelf in the shop. Sometimes a design remains unchanged even 20 years later, and the product is still sound.





 This chapter was translated from Russian jointly by author and by
This chapter was translated from Russian jointly by author and by