Why does Dodo Pizza need 250 developers?


Before we start, I would like to thank Elena Indrupskaya for translating the articles to English.
Things have changed a bit since the original publication. My comments on the current state of affairs are indicated like this.

Visual Studio 2019 pushes the boundaries of individual and team productivity. We hope that you will find these new capabilities compelling and start your upgrade to Visual Studio 2019 soon.
As you are considering this upgrade, rest assured that Visual Studio 2019 makes it distinctively easy to move your codebase from previous versions of Visual Studio. This post captures the reasons why your upgrade to Visual Studio 2019 will be pain-free.



Machine Learning (ML) technologies are becoming increasingly popular and have various applications, ranging from smartphones and computers to large-scale enterprise infrastructure that serves billions of requests per day. Building ML tools, however, remains difficult today because there are no industry-wide standardised approaches to development. Many engineering students studying ML and Data Science must re-learn once they begin their careers. In this article, I've compiled a list of the top five problems that every ML specialist faces only on the job, highlighting the gap between university curriculum and real-world practice.

I strain to make the far-off echo yield
A cue to the events that may come in my day.
(‘Doctor Zhivago’, Boris Pasternak)
I’ll be honest: I don’t write in pure C that often anymore and I haven’t been following the language’s development for a long time. However, two unexpected things happened recently: С won back the title of the most popular programming language according to TIOBE, and the first truly interesting book in years on this language was published. So, I decided to spend a few evenings studying material on C2x, the future version of C.
Here I will share with you what I consider to be its most interesting new features.



 Starting from .NET Core 2.0 and .NET Framework 4.5 we can use new data types:
Starting from .NET Core 2.0 and .NET Framework 4.5 we can use new data types: Span and Memory. To use them, you just need to install the System.Memory nuget package:
PM> Install-Package System.MemoryThese data types are notable because the CLR team has done a great job to implement their special support inside the code of .NET Core 2.1+ JIT compiler by embedding these data types right into the core. What kind of data types are these and why are they worth a whole chapter?
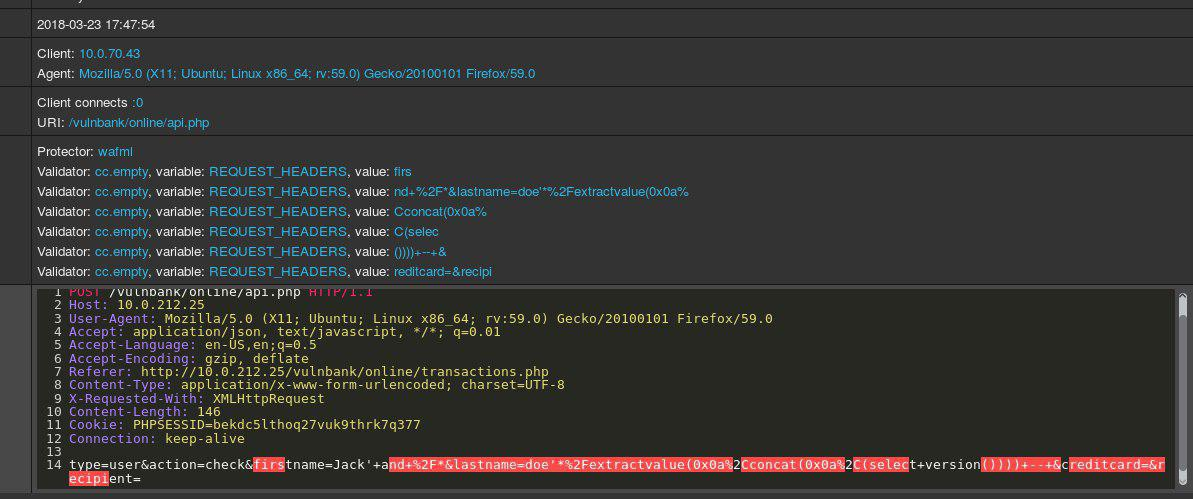
If we talk about problems that made these types appear, I should name three of them. The first one is unmanaged code.
Both the language and the platform have existed for many years along with means to work with unmanaged code. So, why release another API to work with unmanaged code if the former basically existed for many years? To answer this question, we should understand what we lacked before.
This chapter was translated from Russian jointly by author and by professional translators. You can help us with translation from Russian or English into any other language, primarily into Chinese or German.
Also, if you want thank us, the best way you can do that is to give us a star on github or to fork repositorygithub/sidristij/dotnetbook.

Google and Facebook are the computerized behemoths who dependably contend. Their answers for designers Angular and React appear matches as well. Demand helps look at both. The article was initially posted here
Toward the start of its advancement, SPA web stages did not have an adaptable however basic framework for making the ventures that could revise and, now and again, supplant both portable and work area applications. Around then, a client whose issue was very basic needed to discover an application equipped for tackling the issue. Over the span of time, the advancements continued pushing ahead making web administrations gain ubiquity since the last had no should be introduced. What was required is simply to visit a site for getting to some administration. Already, such errands could be tackled through sites written in either ActionScript or Java. Nonetheless, those frameworks required to introduce either Flash or Java being in the meantime a long way from the speed expected by the clients.@Angular
By then, JavaScript advanced adequately to desert its adversaries because of a fast, improvement straightforwardness, and ceaseless help of the programs' engineers. The period of JavaScript began inciting such definition as SPA (Single Page Application) which gave another way to deal with the advancement of web stages. Not at all like its precursor MPA (Multi-Page Application), SPA permitted a web administration to work a lot quicker just as to give it an increasingly refined usefulness fit for changing progressively as per clients' needs. The greatest disadvantage was in unadulterated JavaScript which couldn't give a quick improvement when even a crude SPA web administration required a ton of time to be made. That is the reason Google chosen to help the methodology with a system that could enable different organizations to create muddled web administrations without investing a lot of energy for it.
If someone of you has tried create angular libraries, he may face the issue with lazy loading Feature Module from node_modules. Let's dive deeper and go thru the dark water.

The possibility of acquiring more profit through a chat app solution is gaining popularity than adopting to monthly plans based chat platforms
